Microsoft Defender 將 Wacatac 特洛伊木馬識別為包含多種威脅,這些威脅混合在一起 間諜軟件功能 具有傳播惡意軟件的能力. 因其高風險而被認可, 由於其危險性,Wacatac 需要謹慎處理.
了解瓦卡塔克
瓦卡塔克 用作廣泛惡意軟件的標籤,其特徵是其間諜軟件功能及其作為惡意軟件分發者或植入程序的作用. 這種雙重功能在許多現代惡意軟件實例中普遍存在, 讓 Wacatac 檢測變得越來越普遍.
偶爾, 檢測到的內容可能主要是植入程序,而不是間諜軟件或數據竊取程序. Droppers 通常會收集系統信息來識別目標設備, Microsoft Defender 可能解釋為數據收集的行為. 雖然這種數據收集不太全面, 它強調了檢測背後的基本原理.
威脅概述
| 姓名 | 木馬:Win32/Wacatac |
| 行為 | 數據盜竊, 惡意軟件分佈 |
| 惡意軟件類別 | 間諜軟件, 信息竊取者, 銀行木馬, 滴管 |
| 傳輸方式 | 惡意電子郵件附件, 來自非官方來源的未經授權的軟件 |
| 變體 | 木馬:win32/wacatac.b!毫升, 木馬:Win32/Wacatac.H!毫升, 木馬:腳本/Wacatac.H!毫升 |
木馬帶來的風險:Win32/Wacatac
Wacatac 的主要威脅包括其間諜軟件功能——這對用戶隱私構成威脅,因為它 捕獲密碼, cookie 文件, 和會話令牌. 它作為植入程序的角色通過引入額外的惡意軟件而加劇了風險, 從而增強攻擊者’ 獲得.
某些 Wacatac 變體針對特定領域,例如加密貨幣錢包或網上銀行, 用一般盜竊來換取潛在的重大財務損失. 儘管如此, 攻擊者可以輕鬆地將標準間諜軟件與銀行木馬結合起來, 密碼竊取者, 或勒索軟件作為輔助負載.
惡意軟件家族被檢測為特洛伊木馬 Wacatac
Wacatac 並不局限於單一惡意軟件家族,而是包括通過其共同特徵識別的多種類型. Microsoft Defender 經常在 Wacatac 名稱下識別以下系列:
| 阿瑪迪滴管 | 目前最活躍的惡意軟件之一, 用於分發 Vidar, 紅線偷竊者, 和 STOP/Djvu 勒索軟件. 偶爾會提供加密貨幣挖礦機 收集系統基本信息. |
| 包皮偷盜者 | 最初是數據竊取者, Gozi 後來增強了惡意軟件分發功能. 它的主要功能是作為間諜軟件. |
| 情感 (時代 4 變體) | 一種臭名昭著的惡意軟件,以結合植入者和竊取者角色而聞名. 雖然 Defender 通常將其歸類為 Sabsik, 時代的變遷 4 變體可能改變了它的簽名,使其更類似於 Wacatac. |
| QakBot | 一種長期存在的惡意軟件,主要用於偵察和橫向移動的定向攻擊. 它的網絡是 最近拆除的, 可能預示著即將復蘇. |
| 表格簿 | 也稱為 xLoader, 活躍以來 2016, 它結合了竊取器和滴管功能,但不如 Emotet 臭名昭著. |
消除 Wacatac 木馬
Wacatac 在感染後紮根很深, 使手動移除變得具有挑戰性. 這種隱秘行為對於試圖避免檢測的惡意軟件來說是典型的. 像這樣, 建議使用反惡意軟件工具徹底刪除.
GridinSoft 反惡意軟件 作為一個有效的解決方案脫穎而出, 得益於其不斷更新的數據庫和復雜的啟發式檢測功能, 確保識別和消除最新的惡意軟件威脅.
使用 Gridinsoft 反惡意軟件刪除 Wacatac 木馬
從那時起我們就一直在我們的系統上使用這個軟體, 而且在檢測病毒方面一直很成功. 它阻止了最常見的木馬 從我們的測試中可以看出 與軟體, 我們向您保證,它可以刪除 Wacatac 木馬以及隱藏在您計算機上的其他惡意軟件.
使用 Gridinsoft 刪除惡意威脅, 請依照以下步驟操作:
1. 首先下載 Gridinsoft Anti-Malware, 透過下面的藍色按鈕或直接從官方網站訪問 網格軟體.
2.一旦 Gridinsoft 安裝文件 (安裝-gridinsoft-fix.exe) 已下載, 透過點擊該檔案來執行它. Follow the installation setup wizard's instructions diligently.
3. 訪問 "掃描選項卡" on the application's start screen and launch a comprehensive "全碟掃描" 檢查您的整台計算機. 這種包容性掃描涵蓋了內存, 啟動項, 註冊表, 服務, 司機, 和所有文件, 確保它檢測到隱藏在所有可能位置的惡意軟體.
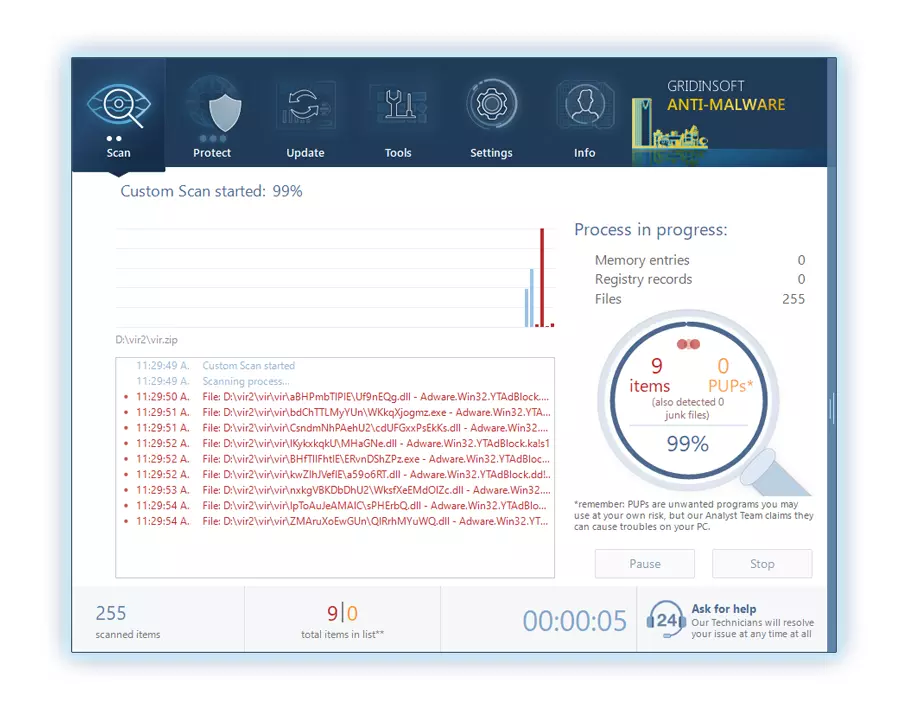
要有耐心, as the scan duration depends on the number of files and your computer's hardware capabilities. 利用這段時間放鬆或處理其他任務.
4. 完成後, 反惡意軟體將提供一份詳細報告,其中包含您 PC 上偵測到的所有惡意專案和威脅.
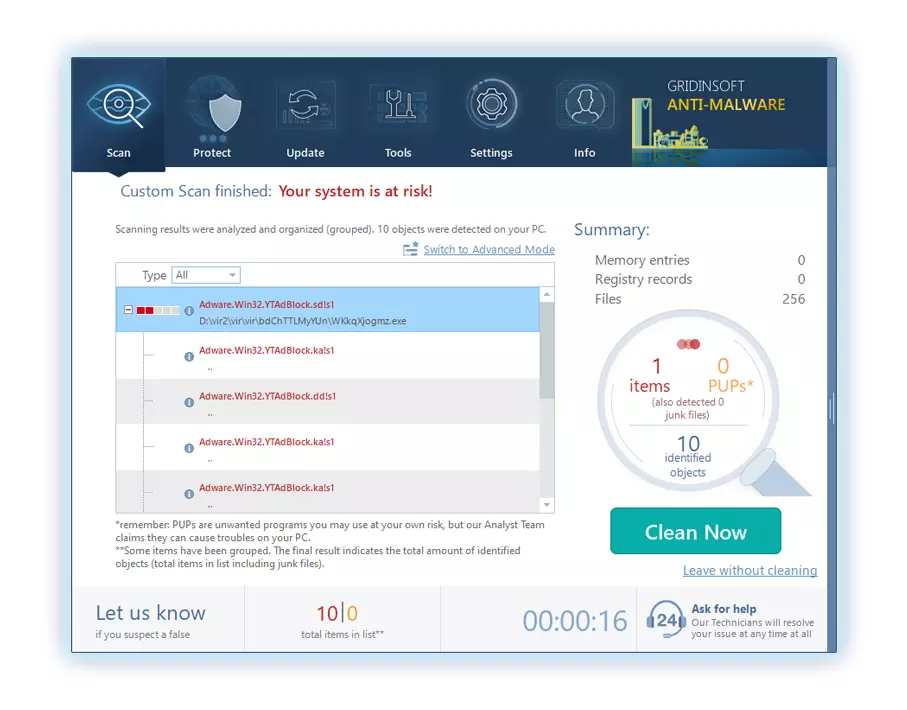
5. 從報告中選擇所有已識別的項目,然後放心地單擊 "立即清潔" 按鈕. 此操作將從您的電腦中安全地刪除惡意文件, 將它們轉移到反惡意軟體程式的安全隔離區,以防止任何進一步的有害行為.
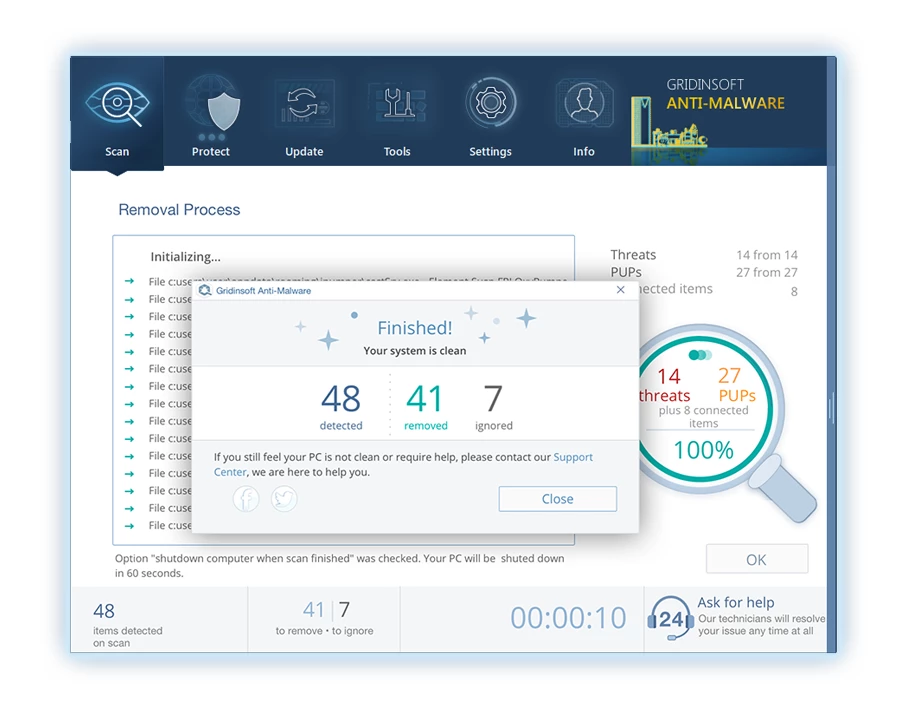
6. 如果出現提示, 重新啟動電腦以完成完整的系統掃描過程. 此步驟對於確保徹底消除任何剩餘威脅至關重要. 重啟後, Gridinsoft Anti-Malware 將會開啟並顯示一則訊息,確認 掃描完成.
請記住 Gridinsoft 提供 6 天免費試用. 這意味著您可以免費利用試用期體驗軟體的全部優勢,並防止您的系統將來受到任何惡意軟體感染. Embrace this opportunity to fortify your computer's security without any financial commitment.
常見問題
🤔 什麼是木馬 Wacatac?
瓦卡塔克, 也稱為木馬:Win32/Wacatac, 是在受感染的計算機上秘密執行惡意活動的惡意軟件.
🤔 Wacatac 是如何傳播的?
它主要通過垃圾郵件和假冒軟件“破解”傳播, 誘騙用戶下載受感染的附件或安裝盜版軟件, 這會導致系統受損.
🤔 Wacatac 會造成什麼危害?
Wacatac 可以顯著擾亂計算機和用戶的數字生活, 竊取登錄憑據和財務數據等敏感信息, 冒著隱私洩露和重大經濟損失的風險.
我需要你的幫助來分享這篇文章.
輪到你幫助別人了. 本文旨在幫助像您這樣的人. 使用下面的按鈕在您喜歡的社交媒體平台(例如 Facebook)上分享此信息, 嘰嘰喳喳, 或Reddit.
布倫丹·史密斯






發表評論