This article introduces you to the latest and popular trojan, Win64:Malware-Gen. Avast and AVG antivirus systems have been named for identifying suspicious but undefined files. While Win64:Malware-Gen shares traits with other trojans or viruses, it also stands out in several ways. Read on for more details.
Avast Keeps Catching Virus: Win64:Malware-gen
What Is Win64 Malware Gen?
Win64:Malware-Gen
Avast Antivirus specifically designed and utilizes Win64:Malware-gen as a heuristic detection to generically identify a trojan horse. The executable of Win64 Malware gen can function as ransomware, hijacking and encrypting files on the infected computer and demanding payment for their release.
In many cases, the Win64:Malware-gen ransomware advises its victims to transfer money, aiming to mitigate the risks the trojan poses to the affected device.
Typically, the modifications Malware-gen executes on infected computers include:
- Opening, editing, modifying, renaming, encrypting, moving, distributing, deleting, or destroying files.
- Conducting network activity undetected, as it evades the Microsoft API designed to monitor such activity in Windows operating systems over the last 30 days.
- Blocking routine access to the target’s workstation, a common virus behavior known as a locker. This virus type restricts access to the computer until the victim pays a ransom.
How Does Win64:Malware-gen Infect a Computer?
Win64 Malware-gen can infiltrate your machine through phishing emails or if you visit a malicious website. Additionally, it spreads via pirated software installers, cracked programs, software loaders, keygens, downloads from dubious sites, torrent websites, strange links, fake updates, and other unsafe sources.
How Does Win64 Malware Gen Work?
Upon successful infection, this virus encrypts data or disrupts program functionality. It also generates a ransom note demanding payment from the victim for data decryption or tool unblocking. Victims usually encounter this ransom note upon restarting their computers after the hijack becomes apparent.
Globally, Win64 Malware-Gen is rapidly spreading. The ransom demand and the note’s presentation, however, can vary by region.
For instance, in some areas, it may send false alerts about unlicensed software on the victim’s computer, demanding ransom. Alternatively, in places with less emphasis on app privacy, it might impersonate a law enforcement body, falsely alleging illegal content on the victim’s device and demanding payment.
What Are the Negative Effects Caused by Win64:Malware-gen?
Win64:Malware may lead to the following adverse effects on infected computers:
- Downloading and installing other malware.
- Sending fake program updates or installation pop-ups.
- Conducting click fraud.
- Repurposing your computer for spamming or botnet inclusion.
- Recording and sending your computer activities, like website visits, chats, and keystrokes, to a remote hacker.
- Taking screenshots and hacking your webcam to record videos.
- Allowing remote access for a hacker to steal login credentials by modifying and creating registry entries.
- Displaying ads and turning webpage text into hyperlinks.
- Using your sensitive data for fraudulent transactions, identity theft, illegal gambling, borrowing money, and other illicit activities, leading to significant financial loss once your privacy is breached.
Win64:Malware-gen Variants in Security Apps
| Antivirus Software | Detection Name |
|---|---|
| Alibaba Cloud Security Center | TrojanDropper:Win64/LaZagne.8fcc6442 |
| Avast | Win64:Malware-gen |
| AVG | Win64:Malware-gen |
| Avira | HEUR/AGEN.1046641 |
| Bitdefender | Trojan.PasswordStealer.GenericKDS.33544129 |
| Web | Trojan.Siggen9.20767 |
| Emsisoft | Trojan.GenericKD.33545160 (B) |
| FireEye | Generic.mg.d08c3a2f1f530dcb |
| F-Secure | Heuristic.HEUR/AGEN.1046641 |
| GridinSoft | Trojan.Ransom.Gen |
| K7GW | Riskware ( 0040eff71 ) |
| Kaspersky | not-a-virus:HEUR:PSWTool.Python.LaZagne.gen |
| McAfee | Artemis!D08C3A2F1F53 |
| McAfee GW Edition | BehavesLike.Win32.Backdoor.vc |
| Microsoft | Trojan:Win32/Wacatac.B!ml |
| Qihoo 360 | HEUR/QVM10.1.E9CF.Malware.Gen |
| Sophos | Generic PUA KE (PUA) |
| Symantec | Trojan.Gen.MBT |
| Trend Micro Apex One | Malicious |
| TrendMicro HouseCall | TROJ_GEN.R002H07CE20 |
Remove Win64:Malware-Gen with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Trojan viruses as shown from our tests with the software, and we assure you that it can remove Win64:Malware-Gen as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file. Follow the installation setup wizard's instructions diligently.
3. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
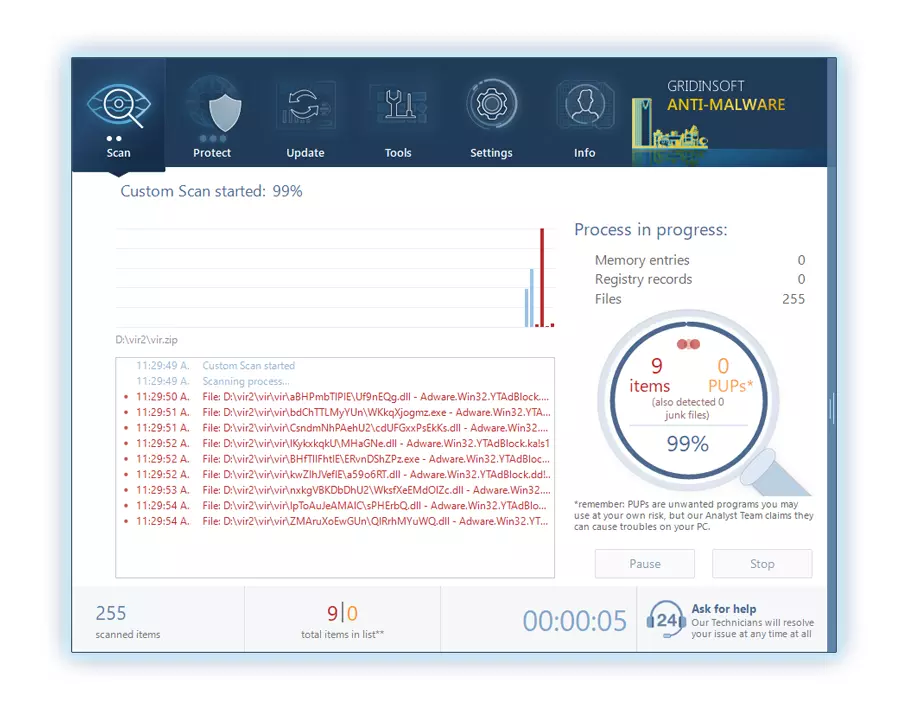
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
4. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
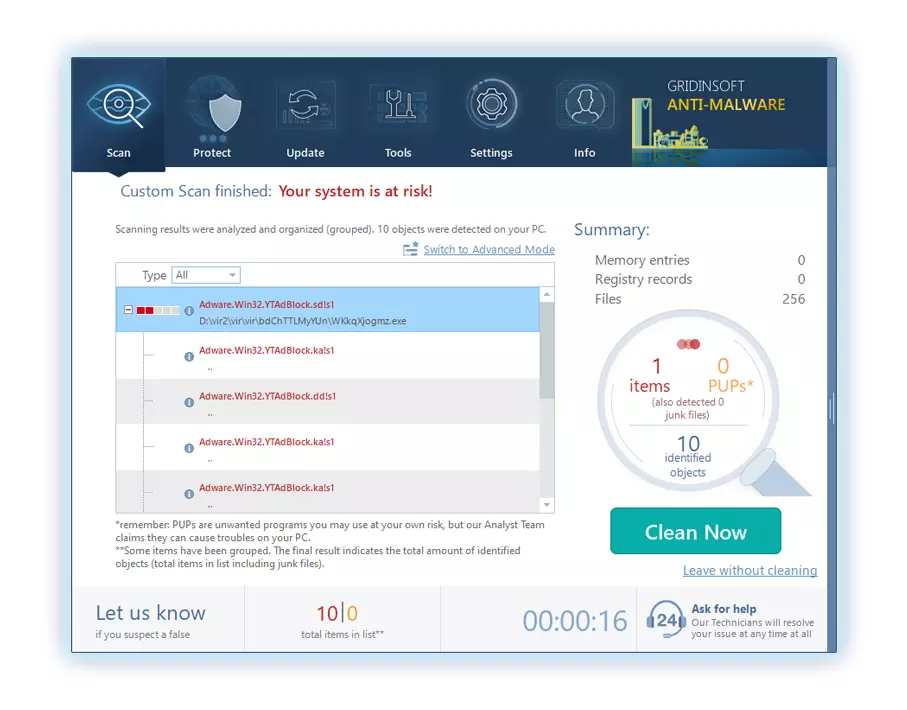
5. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
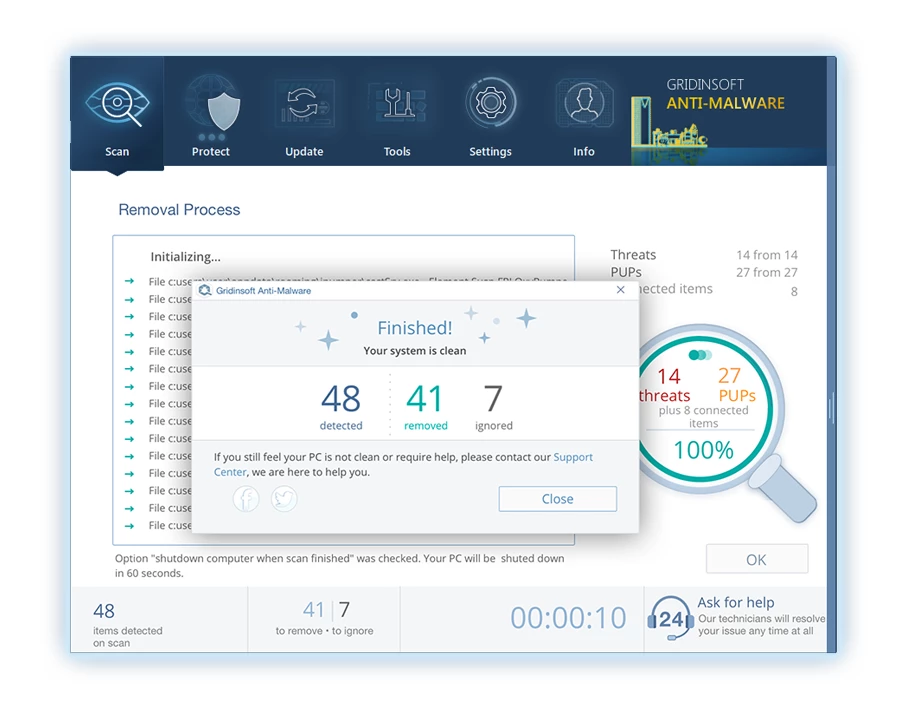
6. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.







Leave a Comment