I’ve relocated the files to quarantine numerous times, but they keep reappearing. Could this file pose a genuine threat?from Reddit
| Name | IDP.HEUR.26 |
| Details | IDP.HEUR.26 – IDP (Intrusion Detection Protection), HEUR stands for Heuristic, indicating the method of detection. The number 26 represents a specific heuristic detection, with the first two elements of the detection considered more significant. |
The term IDP.HEUR.26 refers to a generic detection used by AVG antivirus to flag files or behaviors that might be harmful. This detection method is crucial as it helps identify patterns similar to those found in various forms of malware, including trojans, viruses, and worms.
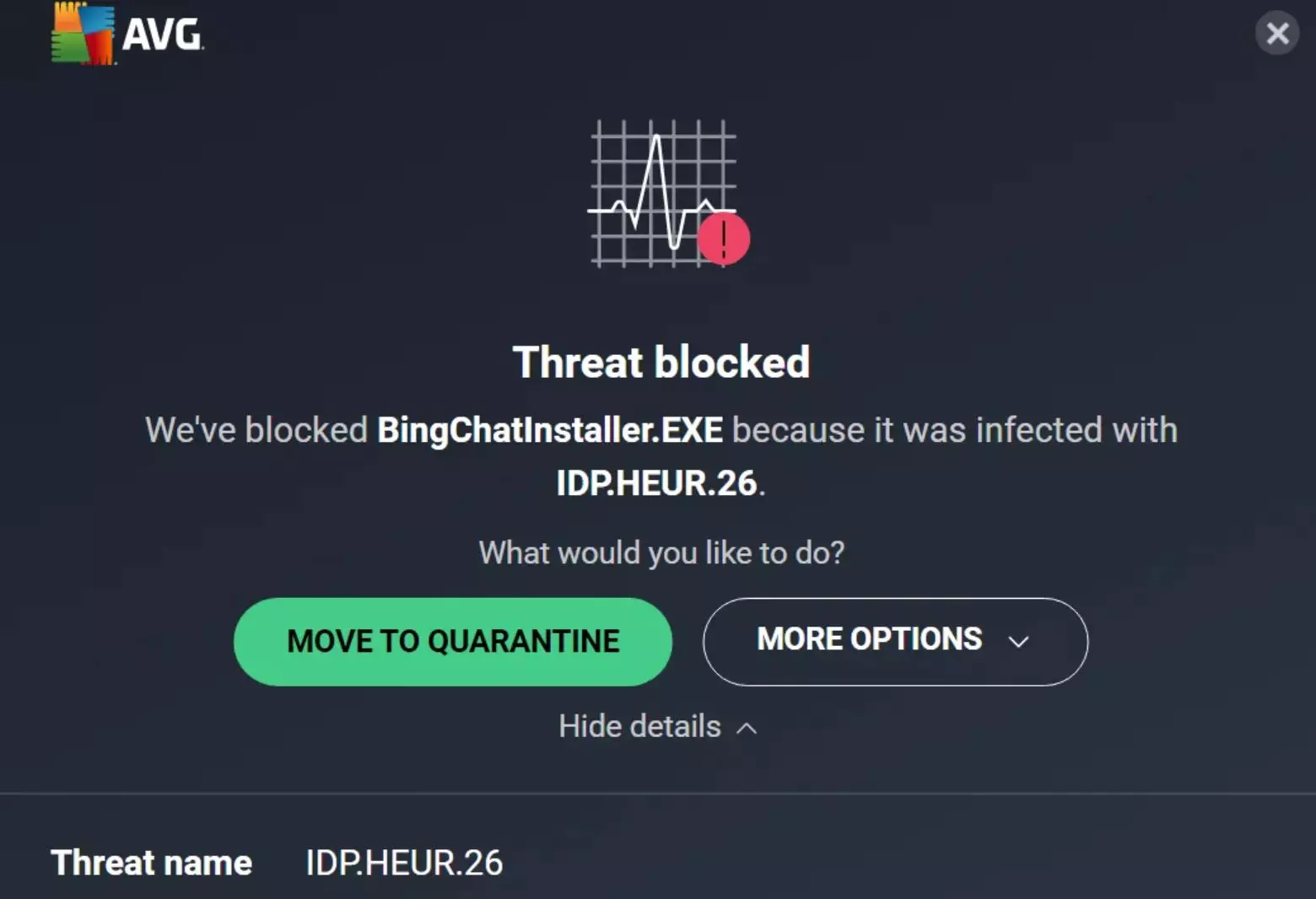
IDP.HEUR.26 AVG Detection
The “IDP” in the name stands for “Identity Protection,” highlighting that AVG detection focuses on the behavior of the file instead of just its known signatures or attributes. Meanwhile, “HEUR” indicates “Heuristic” analysis, which involves a set of rules and algorithms designed to spot potential threats that are new or previously unrecognized.
The number “26” acts as a specific identifier for this type of heuristic detection within AVG’s system. It’s important to recognize that detections are labeled as IDP.HEUR.26 isn’t always indicative of malicious intent; sometimes, legitimate software might exhibit behaviors that trigger these alerts.
Malware aims to exploit users for profit1. Malware developers often disregard ethical considerations, employing numerous tactics to achieve their goals. Whether it’s stealing your data, monetizing the ads you view, or using your device’s processing power to mine cryptocurrency, these are just some of the ways they can exploit your system. Reflect on the implications of such actions on your digital freedom and security.
How to remove the IDP.HEUR.26 from my PC?
IDP.HEUR.26 malware is very difficult to eliminate by hand. It places its data in multiple places throughout the disk and can get back itself from one of the elements. In addition, various alterations in the Windows registry, networking settings, and Group Policies are quite hard to identify and change to the initial. It is better to use a special program – exactly, an anti-malware app. GridinSoft Anti-Malware will fit the most ideal for virus elimination purposes.
Remove IDP.HEUR.26 with Gridinsoft Anti-Malware
We have also been using this software on our systems ever since, and it has always been successful in detecting viruses. It has blocked the most common Trojans as shown from our tests with the software, and we assure you that it can remove IDP.HEUR.26 as well as other malware hiding on your computer.
To use Gridinsoft for remove malicious threats, follow the steps below:
1. Begin by downloading Gridinsoft Anti-Malware, accessible via the blue button below or directly from the official website gridinsoft.com.
2.Once the Gridinsoft setup file (setup-gridinsoft-fix.exe) is downloaded, execute it by clicking on the file. Follow the installation setup wizard's instructions diligently.
3. Access the "Scan Tab" on the application's start screen and launch a comprehensive "Full Scan" to examine your entire computer. This inclusive scan encompasses the memory, startup items, the registry, services, drivers, and all files, ensuring that it detects malware hidden in all possible locations.
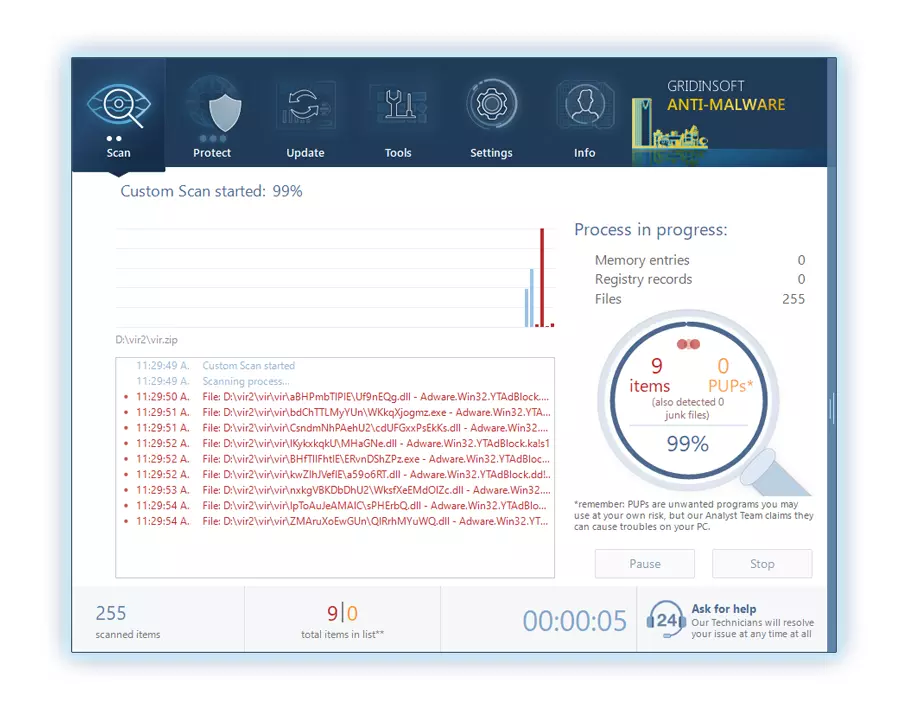
Be patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Use this time to relax or attend to other tasks.
4. Upon completion, Anti-Malware will present a detailed report containing all the detected malicious items and threats on your PC.
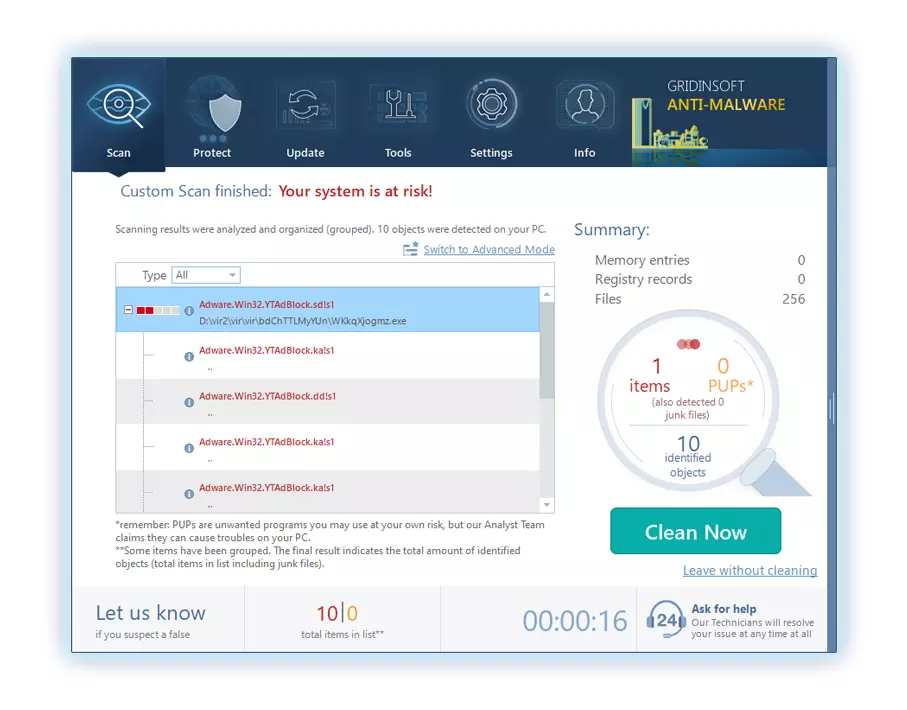
5. Select all the identified items from the report and confidently click the "Clean Now" button. This action will safely remove the malicious files from your computer, transferring them to the secure quarantine zone of the anti-malware program to prevent any further harmful actions.
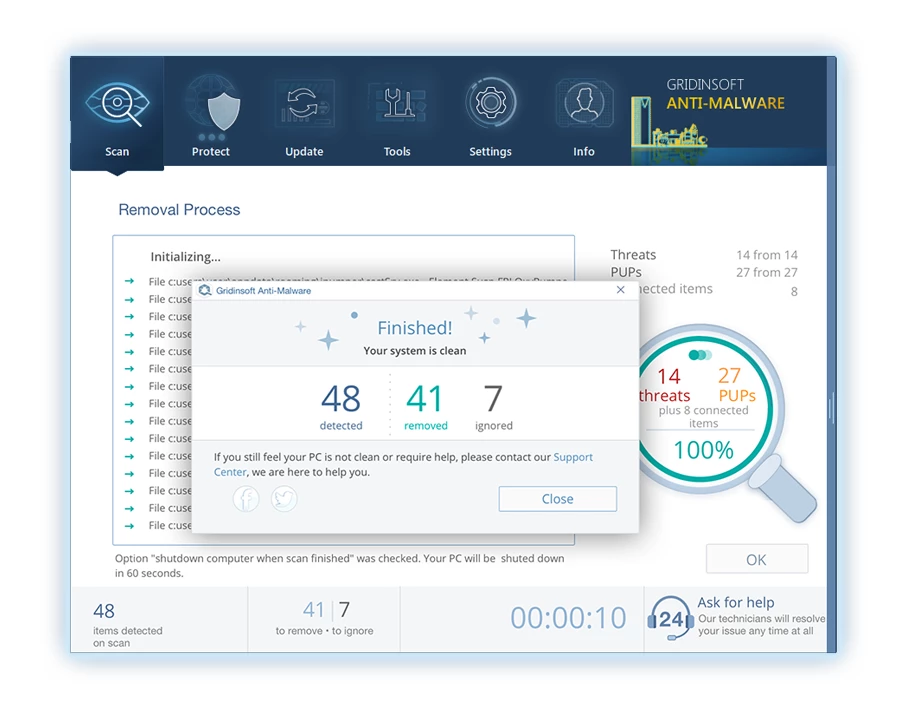
6. If prompted, restart your computer to finalize the full system scan procedure. This step is crucial to ensure thorough removal of any remaining threats. After the restart, Gridinsoft Anti-Malware will open and display a message confirming the completion of the scan.
Remember Gridinsoft offers a 6-day free trial. This means you can take advantage of the trial period at no cost to experience the full benefits of the software and prevent any future malware infections on your system. Embrace this opportunity to fortify your computer's security without any financial commitment.
- Discover more about different malware types at Cybersecurity Glossary.






Leave a Comment