什麼是維札病毒?
The Veza virus is like a bad magic spell that locks up files on computers so you can’t use them. It changes the names of files by adding “.veza” at the end, which means you can’t open them without a special key.
When Veza gets into a computer, it asks for money, paid in Bitcoin, to unlock the files. It leaves a note called “_自述文件.txt” on the desktop and in folders telling you how to pay the money. But even if you pay, there’s no promise your files will be unlocked.
The virus uses a tricky lock called the Salsa20 encryption algorithm that makes it very hard to open the files without the bad guy’s help. But if the Veza virus couldn’t talk to its home base before it locked the files, it uses a simpler lock that might be easier to open.
以下, an image shows what the locked files look like, marked by the “.veza” 擴大:
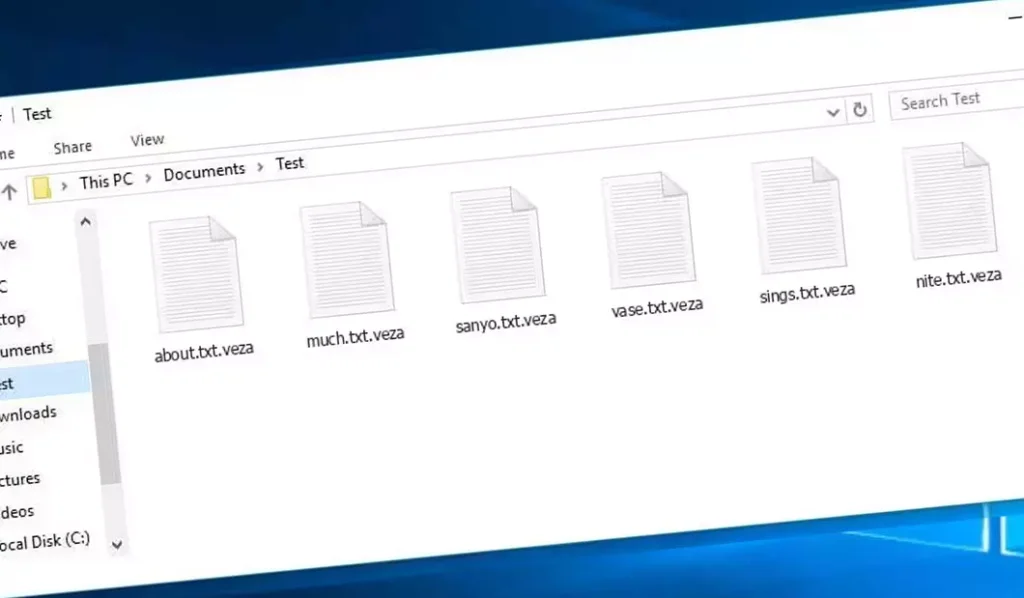
Encrypted Files by Veza Ransomware
| 姓名 | Veza Virus |
| 家庭 1 | STOP/Djvu 勒索軟件 |
| 擴大 | .veza |
| 勒索軟體說明 | _自述文件.txt |
| 贖金 | 從 $499 到 $999 (比特幣) |
| 接觸 | support@freshingmail.top, datarestorehelpyou@airmail.cc |
| 症狀 |
|
| 恢復 | 從全面的恢復開始 防病毒掃描. 雖然並非所有文件都可以恢復, 我們的指南概述了重新獲得加密文件存取權的幾種潛在方法. |
Veza Virus Overview
When the Veza virus gets onto a computer, it starts doing a lot of sneaky things. 第一的, it pretends to be a Windows update with a fake message from a program called winupdate.exe to trick the computer user into thinking everything is normal.
同時, it runs another secret program that starts looking for important files on the computer to lock them up. It also uses a special command:
vssadmin.exe Delete Shadows /All /QuietThis command stops the computer from being able to go back to how it was before the virus, which means you can’t easily fix what the virus changes.
The virus also messes with a list on the computer that helps it find websites. It changes this list so some websites don’t work anymore, especially sites that could help fix the computer or give advice about the virus. It does this by making the computer think these websites are just on your computer and nowhere else, which isn’t true.
The virus also leaves behind two text files on the computer that have secret codes related to the attack – these are called bowsakkdestx.txt 和 PersonalID.txt.
But that’s not all. This virus can also sneak in another bad program called Vidar, which can steal passwords and other private stuff from the computer. Here’s what Vidar can do:
- Put other bad programs on the computer.
- Steal passwords from programs like Steam, Telegram, and Skype.
- Look at and change files without you knowing.
- Steal digital money wallets.
- Let hackers control the computer from far away.
- Take private info like the websites you visit and your saved passwords.
The Veza virus uses a super tough lock called Salsa20 to keep files locked up. If it locks your files with a special key only it knows, it’s really hard to unlock them again. Each key is different for everyone, making it nearly impossible to guess.
If you want to get the key to unlock your files, the hackers ask for $999. They tell you to email them at (support@fishmail.top) to find out how to pay them.
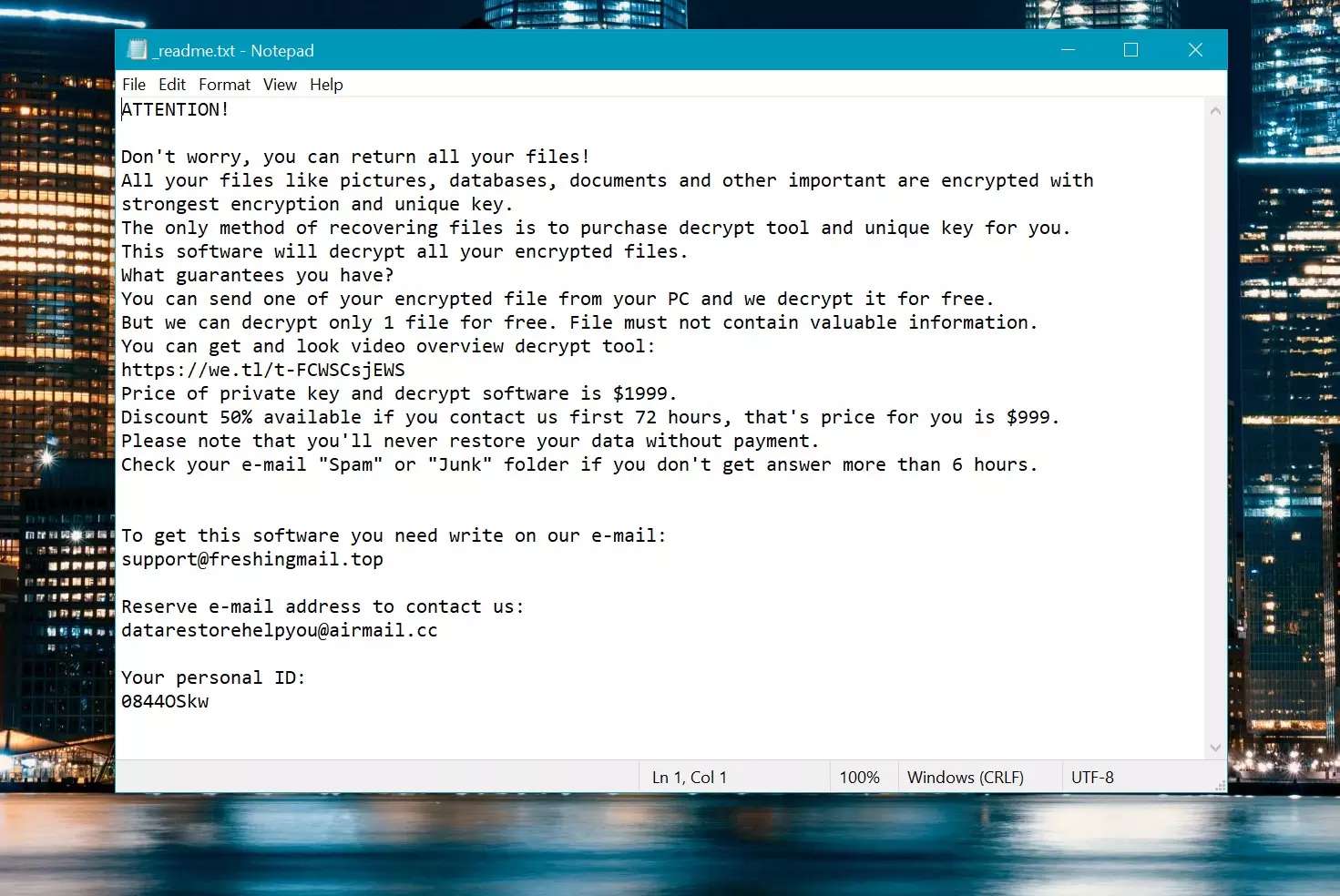
勒索信: _自述文件.txt
如何刪除?
Remove Veza Virus with Gridinsoft Anti-Malware
從那時起我們就一直在我們的系統上使用這個軟體, 而且在檢測病毒方面一直很成功. 它阻止了最常見的勒索軟體: 從我們的測試中可以看出 與軟體, and we assure you that it can remove Veza Virus as well as other malware hiding on your computer.
使用 Gridinsoft 刪除惡意威脅, 請依照以下步驟操作:
1. 首先下載 Gridinsoft Anti-Malware, 透過下面的藍色按鈕或直接從官方網站訪問 網格軟體.
2.一旦 Gridinsoft 安裝文件 (安裝-gridinsoft-fix.exe) 已下載, 透過點擊該檔案來執行它. Follow the installation setup wizard's instructions diligently.
3. 訪問 "掃描選項卡" on the application's start screen and launch a comprehensive "全碟掃描" 檢查您的整台計算機. 這種包容性掃描涵蓋了內存, 啟動項, 註冊表, 服務, 司機, 和所有文件, 確保它檢測到隱藏在所有可能位置的惡意軟體.
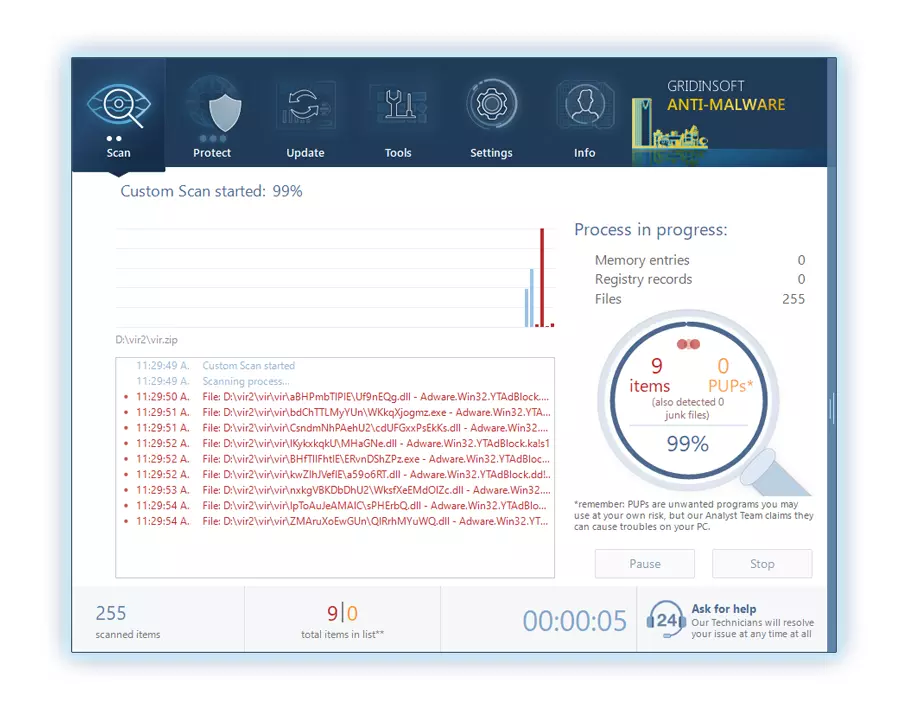
要有耐心, as the scan duration depends on the number of files and your computer's hardware capabilities. 利用這段時間放鬆或處理其他任務.
4. 完成後, 反惡意軟體將提供一份詳細報告,其中包含您 PC 上偵測到的所有惡意專案和威脅.
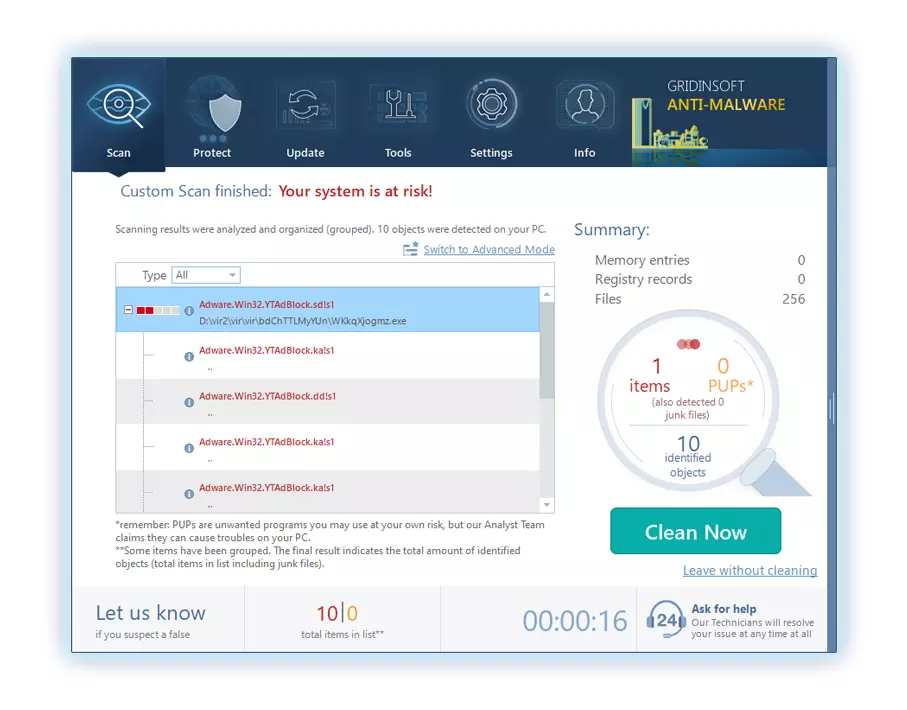
5. 從報告中選擇所有已識別的項目,然後放心地單擊 "立即清潔" 按鈕. 此操作將從您的電腦中安全地刪除惡意文件, 將它們轉移到反惡意軟體程式的安全隔離區,以防止任何進一步的有害行為.
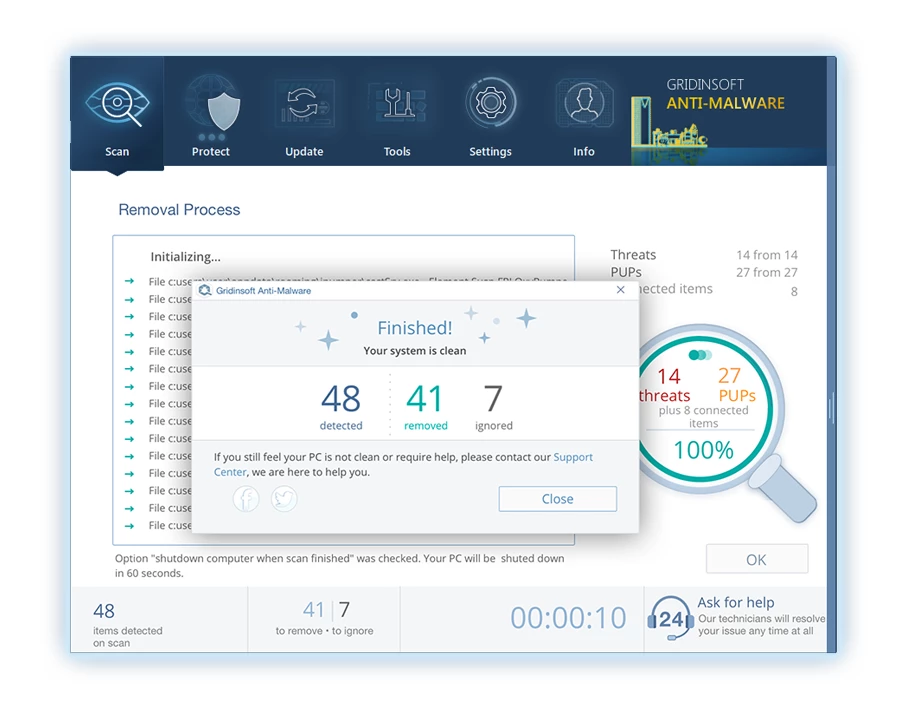
6. 如果出現提示, 重新啟動電腦以完成完整的系統掃描過程. 此步驟對於確保徹底消除任何剩餘威脅至關重要. 重啟後, Gridinsoft Anti-Malware 將會開啟並顯示一則訊息,確認 掃描完成.
請記住 Gridinsoft 提供 6 天免費試用. 這意味著您可以免費利用試用期體驗軟體的全部優勢,並防止您的系統將來受到任何惡意軟體感染. Embrace this opportunity to fortify your computer's security without any financial commitment.
影片指南
How To Decrypt .veza Files?
第一的, 嘗試刪除 “.veza” 幾個大檔案的副檔名,然後打開它們. 該惡意軟體難以加密大文件. The virus either failed to lock the file upon access or encountered a bug and omitted adding the file marker. 如果您的檔案大小超過 2GB, 後一種情況更有可能發生.
犯罪分子在八月底左右發布了最新的擴展 2019 進行多次更改後.
犯罪分子所做的更改使 STOPDecrypter 不再受支持, 導致其被 Emsisoft 開發的 STOP Djvu 勒索軟體 Emsisoft Decryptor 取代.
- 下載並執行解密工具: 下載 解密工具. 確保您以管理員身份執行解密實用程式並同意透過點擊出現的授權條款 “是的” 按鈕. 接受許可條款後.
- 選擇要解密的資料夾: 解密器, 預設情況下, 自動選擇已連接的網路磁碟機上的目錄進行解密. 使用 “添加” 按鈕選擇其他位置. 取決於惡意軟件家族, 解密器提供各種選項, 您可以在“選項”選項卡中打開或關閉它. 以下, 您將找到當前活動選項的詳細列表.
- 單擊開始解密 “解密” 按鈕. 將所有所需位置添加到列表後, 單擊 “解密” 按鈕開始解密過程. 解密器將在完成解密過程後通知您. 如果需要文檔, 您可以通過單擊保存報告 “保存日誌” 按鈕. 還可以將報告複製到剪貼板以粘貼到電子郵件或消息中.
How to Restore .veza Files?
In some case, 勒索軟件無法加密您的文件…
The Veza ransomware encryption process involves encrypting each file byte-by-byte, 創建一個副本, 然後刪除 (不覆蓋) 原始文件. 此刪除意味著物理磁盤不再在其係統中列出該文件, 儘管原始文件仍保留在驅動器上. 保存文件的扇區可能仍然包含它, 但由於系統沒有列出它, 新數據可以覆蓋它. 然而, 特殊軟件可以恢復您的文件.
意識到這是一個在線算法, 我知道恢復我的加密文件是不可能的. 我的備份驅動器, 感染期間連接, 似乎也被感染了. 我的備份驅動器上的每個文件夾都顯示為加密的. 儘管如此, 我幾乎康復了 80% 我的 2TB 存儲空間.
檢查文件夾, 我在每封信中都發現了勒索信. 打開一些發現只有不在子資料夾中的檔案被加密. Delving into subfolders on other folders, 我發現了未加密的文件. 不像我的 C 盤和 D 盤,每個資料夾, 包括子資料夾, 已加密, 我的備份磁碟機的子資料夾已儲存 80% 我的數據.
我認為在我的備份驅動器上發現這個漏洞很幸運. 另外, 我又找回了一個 10% 我的數據來自另一台 PC 上的硬碟. 因此, 我對使用備份磁碟機的建議是建立子資料夾. 部分是運氣, 但不幸的是,在我的備份檔案傳輸過程中病毒襲擊了.
希望這段經歷可以幫助其他有類似困境的人.
傑米紐蘭Recover Your Files with PhotoRec
攝影記錄, 專為從損壞的磁盤或意外刪除中恢復文件而設計, 現在支持恢復 400 文件類型, making it useful after a Veza attack.
第一的, 下載照片記錄. 免費, 但開發商不保證文件恢復. PhotoRec 與 TestDisk 一起打包, 來自同一開發人員的另一個工具, 在 TestDisk 名稱下. 然而, PhotoRec 包含在存檔中.
啟動照片錄製, 打開 “qphotorec_win.exe” 文件. 無需安裝,因為該程式包含所有必需的文件, 允許它從 USB 驅動器運行.



發表評論