Verification.exe is a malicious process found on Windows systems. It may serve as a miner or pose as legitimate while being malicious. This malicious software is designed to execute various harmful operations on compromised systems. Such actions encompass data theft, deployment of further malware, and facilitation of unauthorized access and control by attackers.
Verification.exe Overview
The Verification.exe Trojan is a harmful program that can cause various issues on your compromised computer. It can be used to steal personal data, install other malware, and provide unauthorized access to attackers. This Trojan carries out various malicious activities, such as downloading and installing other malware, exploiting your computer for click fraud, logging keystrokes, and tracking visited sites.
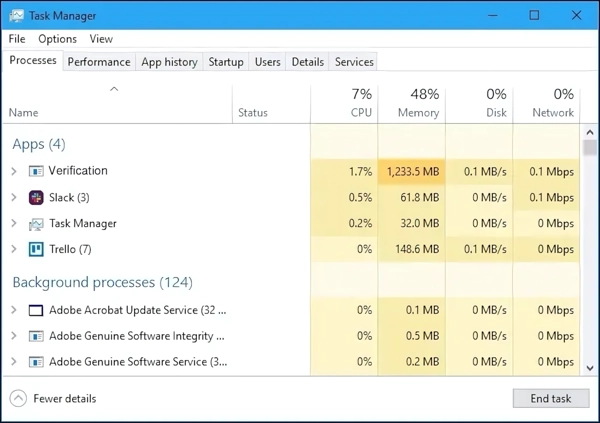
Verification.exe process in the Task manager
It can also transmit your PC information, like usernames and browsing history, to remote malicious entities, grant remote access to your PC, display advertisements, and redirect browser search queries. 另外, it can utilize your computer resources for cryptocurrency mining. It is crucial to be aware of this Trojan’s potential threats and take steps to protect your computer from such attacks.
威脅摘要
| 姓名 | Verification.exe |
| 威脅類型 | 木馬病毒 |
| 細節 | Steals personal data, brings other malicious programs, mangles system security, can mine cryptocurrencies. |
The reason why this malware has picked the Verification.exe name is rather simple – to blend in with other background process. This typically makes the user think it is legit. 然而, when it takes too much system resources, or runs regardless of what program is running, then it’s time for raising the alarm.
How did I get infected?
The Verification.exe can infiltrate your system in various ways. One standard method is through malicious ads that may appear while browsing the internet. These ads can trick you into clicking on a link or downloading an attachment that contains the Trojan. Another way the malware can spread is through spam emails, which may contain infected attachments. It can also take advantage of your operating system or software vulnerabilities to gain access to your system.
Another distribution method is through pirated software or illegal downloads. Most pirated software requires mandatory disabling of the security software on the device. This is because the mechanics of hacking tools are similar to those of malware, making it ideal for spreading it. So, supposeå you are downloading software from an untrusted source or engaging in software piracy. In that case, you are putting your system at risk.
Remove Verification.exe with Gridinsoft Anti-Malware
從那時起我們就一直在我們的系統上使用這個軟體, 而且在檢測病毒方面一直很成功. 它阻止了最常見的木馬 從我們的測試中可以看出 與軟體, and we assure you that it can remove Verification.exe as well as other malware hiding on your computer.
使用 Gridinsoft 刪除惡意威脅, 請依照以下步驟操作:
1. 首先下載 Gridinsoft Anti-Malware, 透過下面的藍色按鈕或直接從官方網站訪問 網格軟體.
2.一旦 Gridinsoft 安裝文件 (安裝-gridinsoft-fix.exe) 已下載, 透過點擊該檔案來執行它. Follow the installation setup wizard's instructions diligently.
3. 訪問 "掃描選項卡" on the application's start screen and launch a comprehensive "全碟掃描" 檢查您的整台計算機. 這種包容性掃描涵蓋了內存, 啟動項, 註冊表, 服務, 司機, 和所有文件, 確保它檢測到隱藏在所有可能位置的惡意軟體.
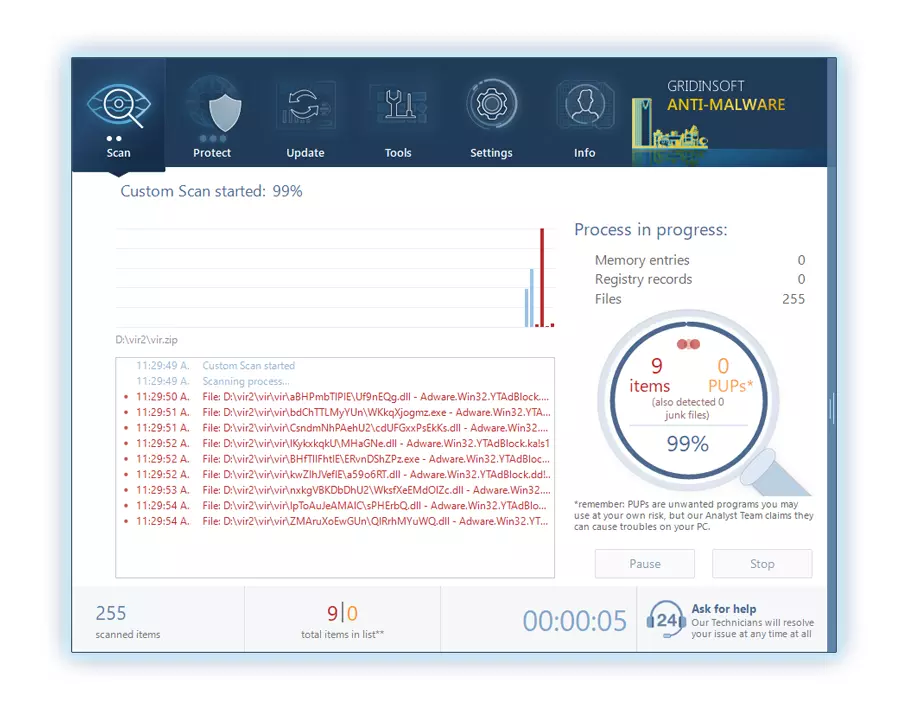
要有耐心, as the scan duration depends on the number of files and your computer's hardware capabilities. 利用這段時間放鬆或處理其他任務.
4. 完成後, 反惡意軟體將提供一份詳細報告,其中包含您 PC 上偵測到的所有惡意專案和威脅.
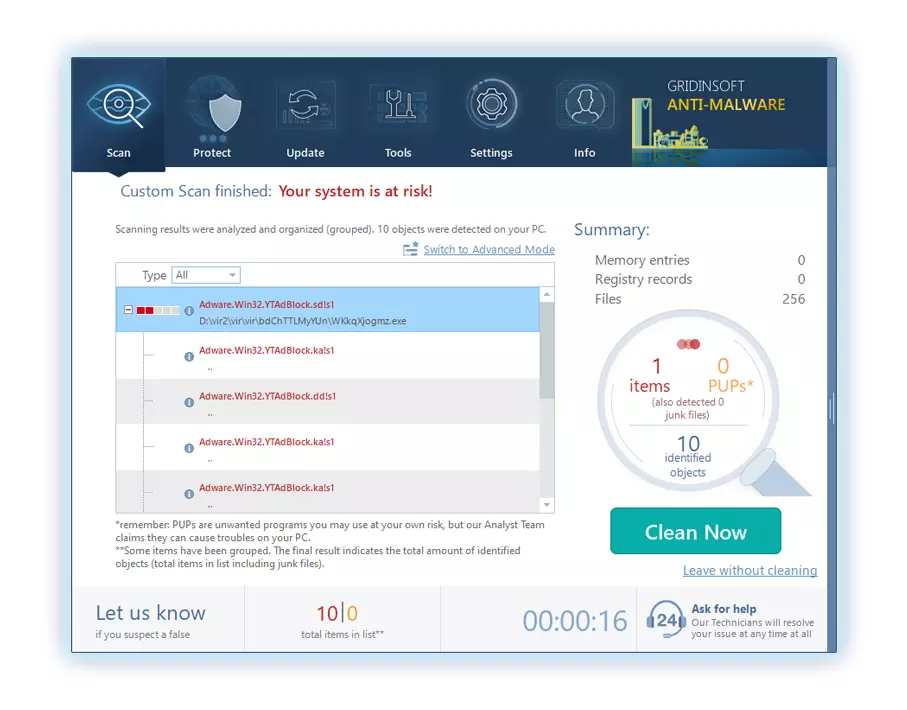
5. 從報告中選擇所有已識別的項目,然後放心地單擊 "立即清潔" 按鈕. 此操作將從您的電腦中安全地刪除惡意文件, 將它們轉移到反惡意軟體程式的安全隔離區,以防止任何進一步的有害行為.
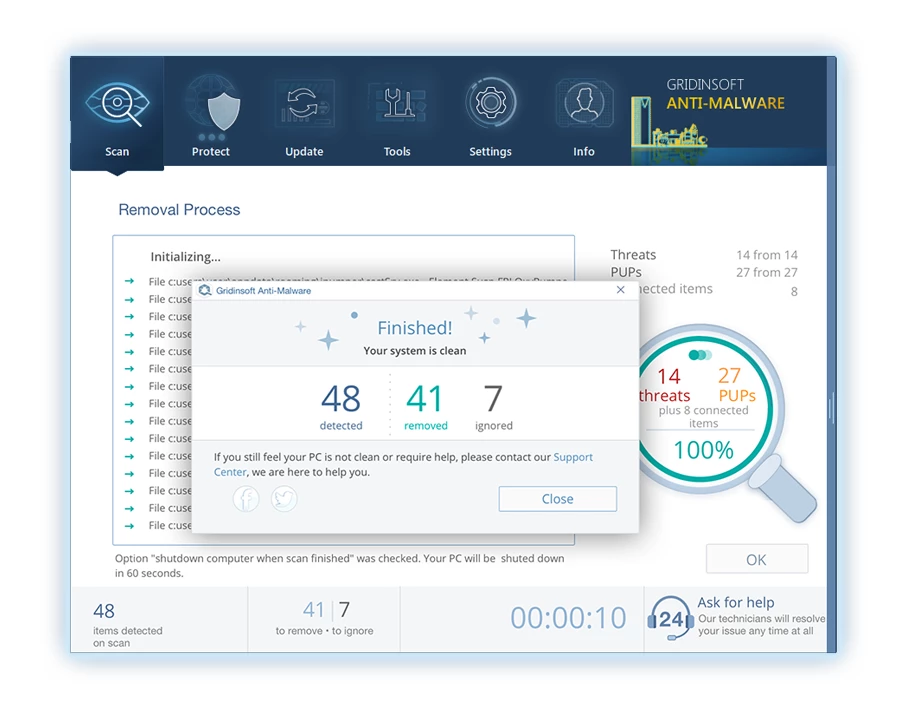
6. 如果出現提示, 重新啟動電腦以完成完整的系統掃描過程. 此步驟對於確保徹底消除任何剩餘威脅至關重要. 重啟後, Gridinsoft Anti-Malware 將會開啟並顯示一則訊息,確認 掃描完成.
請記住 Gridinsoft 提供 6 天免費試用. 這意味著您可以免費利用試用期體驗軟體的全部優勢,並防止您的系統將來受到任何惡意軟體感染. Embrace this opportunity to fortify your computer's security without any financial commitment.






發表評論