If your computer alerts you with the Trojan:Win32/SmokeLoader!pz detection name, it’s a critical sign of danger. This detection indicates ransomware, which encrypts your files and demands a ransom for their decryption. Immediate action and specific steps are necessary to remove this malware promptly.
特洛伊木馬:Win32/SmokeLoader!pz virus is commonly detected after engaging in risky activities on your computer, such as opening suspicious emails, clicking on online ads, or downloading software from unreliable sources. Once detected, swift action is essential to prevent its harmful effects. Delaying can lead to severe damage, so it’s crucial to act quickly.
Understanding Trojan:Win32/SmokeLoader!pz Virus
This ransomware targets the files on your computer, encrypts them, and then demands a ransom for a decryption key. In addition to locking your files, 木馬:Win32/SmokeLoader!pz significantly damages your system’s functionality. It alters network settings to block access to removal guides and prevent the download of anti-malware solutions. 有時, it may even stop anti-malware programs from launching.
Key Features
The following are some of the primary actions of the Trojan:Win32/SmokeLoader!pz malware on an infected computer:
- Behavioral detection: Executable code extraction – unpacking.
- Unconventional language in binary resources: Punjabi.
- Authenticode signature is invalid.
- Behavioral detection: Code injection techniques like Process Hollowing and Inter-process.
- Encrypts files, making them inaccessible.
- Blocks execution of anti-malware software.
- Prevents the installation of antivirus programs.
Ransomware remains a significant threat, representing one of the most severe types of viruses affecting individuals and businesses alike. The encryption algorithms used (typically RHA-1028 or AES-256) are robust, with decryption through brute force nearly impossible. Despite the power of this malware, it does not execute its actions instantly; it may take several hours to encrypt all your files. 因此, detecting Trojan:Win32/SmokeLoader!pz should be a clear signal to begin the removal process immediately.
木馬:Win32/SmokeLoader!pz Spreads
特洛伊木馬:Win32/SmokeLoader!pz spreads via typical methods shared with other malware types. These include deceptive websites offering free software downloads, phishing emails pretending to be legitimate notifications, and malicious tools. Phishing emails, a newer strategy, may appear as ordinary updates about shipments or bank services but contain harmful attachments or links leading to malicious websites.
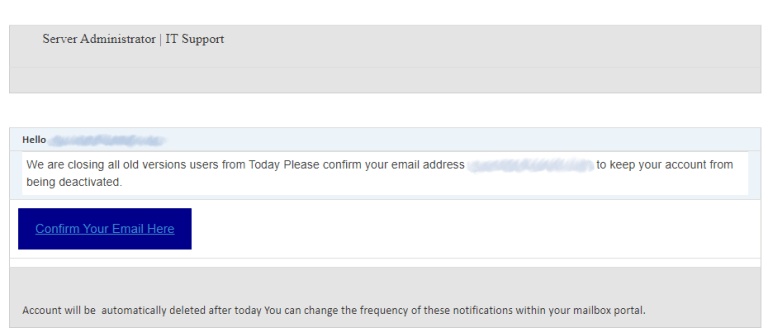
Malicious email message. This one tricks you into opening the phishing website.
Avoiding it looks quite uncomplicated, 然而, still demands a lot of attention. Malware can hide in different places, and it is better to stop it even before it goes into your computer than to trust in an anti-malware program. Simple cybersecurity knowledge is just an important item in the modern world, even if your relationship with a computer remains on YouTube videos. That can keep you a lot of time and money which you would certainly spend while searching for a fix guide.
Technical Details
| 布卡夫 | W32.AIDetectMalware |
| 獅子 | Trojan.Win32.SmokeLoader.4!c |
| tehtris | Generic.Malware |
| 微觀世界電子掃描 | Trojan.GenericKD.70612133 |
| 火眼 | Generic.mg.284ec46a8277bda8 |
| CAT-QuickHeal | Ransom.Stop.P5 |
| Skyhigh | BehavesLike.Win32.Lockbit.dm |
| 阿利亞克 | Trojan.GenericKD.70612133 |
| 賽蘭斯 | unsafe |
| 歌曲為 | 木馬Win32.Save.a |
| K7防毒軟體 | 木馬 ( 005aafe61 ) |
| 阿里巴巴 | 木馬:Win32/SmokeLoader.cfaee45c |
| K7GW | 木馬 ( 005aafe61 ) |
| 網路理性 | malicious.78f4e3 |
| 它將被隱藏 | Trojan.Generic.D43574A5 |
| 賽門鐵克 | ML.屬性.高置信度 |
| 鬆緊帶 | 惡意的 (高置信度) |
| 案例-NOD32 | a variant of Win32/Kryptik.HVKJ |
| 相當 | 惡意的 (分數: 100) |
| 頂點 | 惡意的 |
| 蛤蜊病毒 | Win.Packer.pkr_ce1a-9980177-0 |
| 卡巴斯基 | 赫魯爾:木馬Win32變種gen |
| 比特衛士 | Trojan.GenericKD.70612133 |
| 阿瓦斯特 | Win32:PWSX-gen [特吉] |
| 騰訊 | Trojan.Win32.Obfuscated.gen |
| 索福斯 | Troj/Krypt-VK |
| f-secure | Trojan.TR/Crypt.Agent.kakul |
| 博士網 | Trojan.PWS.Stealer.34727 |
| VIPRE | Trojan.GenericKD.70612133 |
| TrendMicro | Trojan.Win32.SMOKELOADER.YXDK3Z |
| Trapmine | malicious.high.ml.score |
| 艾姆西軟體 | Trojan.GenericKD.70612133 (乙) |
| 哨兵一號 | 靜態人工智慧 – 惡意PE |
| Jiangmin | Trojan.Chapak.rrw |
| Varist | W32/Kryptik.LDY.gen!埃爾多拉多 |
| 阿維拉 | TR/Crypt.Agent.kakul |
| Antiy-AVL | Trojan/Win32.Caynamer |
| 金山軟體 | Win32.Troj.Agent.cks |
| 微軟 | 木馬:Win32/SmokeLoader!普茲 |
| ZoneAlarm | 赫魯爾:木馬Win32變種gen |
| 通用數據 | Trojan.GenericKD.70612133 |
| Detected | |
| 安實驗室-V3 | Malware/Win.RansomX-gen.R625969 |
| 麥克菲 | Artemis!284EC46A8277 |
| 最大限度 | 惡意軟體 (ai score=85) |
| VBA32 | BScope.Trojan.Yakes |
| 惡意軟體位元組 | 惡意包變種GS |
| 貓熊 | Trj/Genetic.gen |
| TrendMicro-HouseCall | Trojan.Win32.SMOKELOADER.YXDK3Z |
| 瑞星 | Trojan.SmokeLoader!1.EB63 (CLASSIC) |
| 伊卡洛斯 | Trojan.Win32.Azorult |
| MaxSecure | Trojan.Malware.73643692.susgen |
| 飛塔 | W32/GenKryptik.ERHN!tr |
| 平均電壓 | IDP.通用 |
| DeepInstinct | MALICIOUS |
| 群眾罷工 | 獲勝/malicious_confidence_100% (瓦) |
How to remove?
木馬:Win32/SmokeLoader!pz malware is very hard to eliminate manually. It stores its data in several places throughout the disk and can get back itself from one of the parts. 另外, Windows 註冊表中的各種更改, 網絡配置, and also Group Policies are pretty hard to discover and return to the initial. It is better to use a specific app – 確切地, an anti-malware tool. GridinSoft 反惡意軟件 will fit the best for malware elimination goals.
刪除木馬:Win32/SmokeLoader!pz with Gridinsoft Anti-Malware
從那時起我們就一直在我們的系統上使用這個軟體, 而且在檢測病毒方面一直很成功. 它阻止了最常見的木馬 從我們的測試中可以看出 與軟體, 我們向您保證它可以刪除木馬:Win32/SmokeLoader!pz as well as other malware hiding on your computer.
使用 Gridinsoft 刪除惡意威脅, 請依照以下步驟操作:
1. 首先下載 Gridinsoft Anti-Malware, 透過下面的藍色按鈕或直接從官方網站訪問 網格軟體.
2.一旦 Gridinsoft 安裝文件 (安裝-gridinsoft-fix.exe) 已下載, 透過點擊該檔案來執行它. Follow the installation setup wizard's instructions diligently.
3. 訪問 "掃描選項卡" on the application's start screen and launch a comprehensive "全碟掃描" 檢查您的整台計算機. 這種包容性掃描涵蓋了內存, 啟動項, 註冊表, 服務, 司機, 和所有文件, 確保它檢測到隱藏在所有可能位置的惡意軟體.
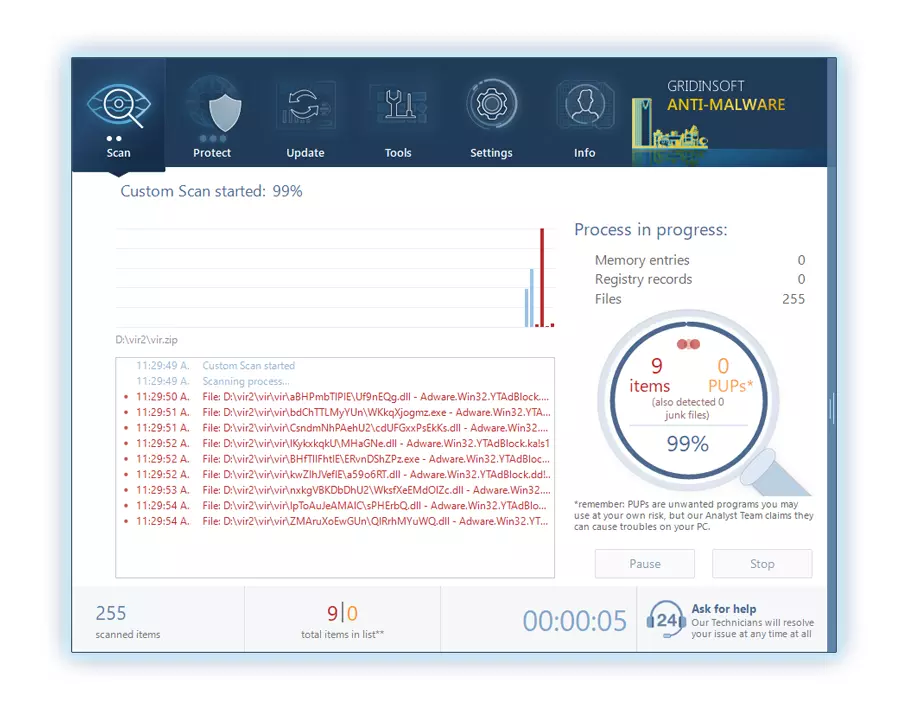
要有耐心, as the scan duration depends on the number of files and your computer's hardware capabilities. 利用這段時間放鬆或處理其他任務.
4. 完成後, 反惡意軟體將提供一份詳細報告,其中包含您 PC 上偵測到的所有惡意專案和威脅.
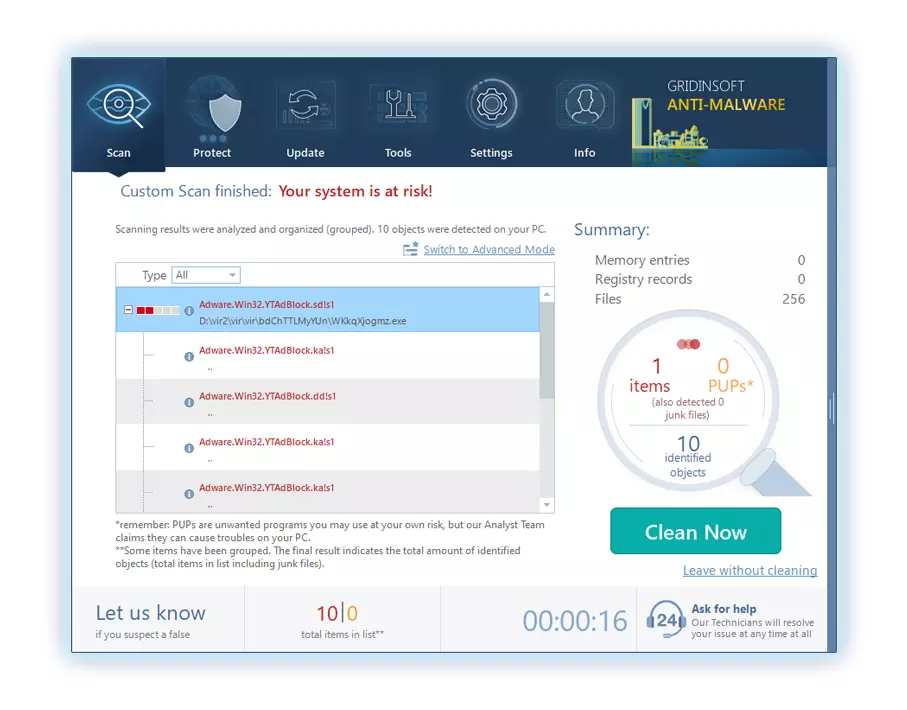
5. 從報告中選擇所有已識別的項目,然後放心地單擊 "立即清潔" 按鈕. 此操作將從您的電腦中安全地刪除惡意文件, 將它們轉移到反惡意軟體程式的安全隔離區,以防止任何進一步的有害行為.
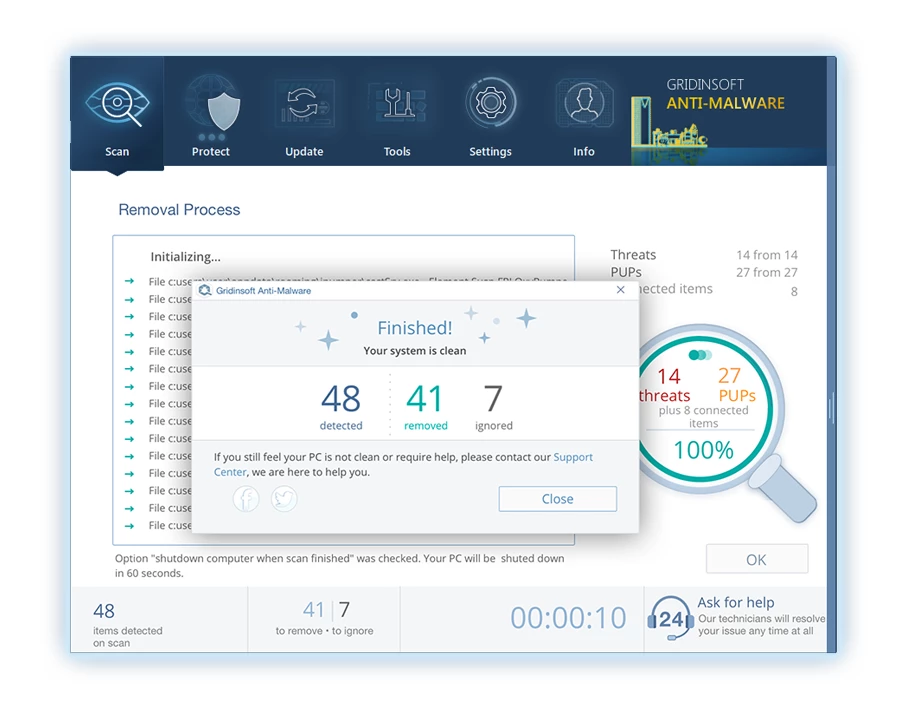
6. 如果出現提示, 重新啟動電腦以完成完整的系統掃描過程. 此步驟對於確保徹底消除任何剩餘威脅至關重要. 重啟後, Gridinsoft Anti-Malware 將會開啟並顯示一則訊息,確認 掃描完成.
請記住 Gridinsoft 提供 6 天免費試用. 這意味著您可以免費利用試用期體驗軟體的全部優勢,並防止您的系統將來受到任何惡意軟體感染. Embrace this opportunity to fortify your computer's security without any financial commitment.







發表評論