這 神羅病毒 是的一部分 質子勒索軟件 家庭. 此類勒索軟件會加密您電腦上的所有數據,包括照片, 文本文件, 試算表, 聲音的, 和視頻文件 - 並為每個文件添加唯一的擴展名. 它還留下了一個 #SHINRA-Recovery.txt 每個包含加密文件的文件夾中的文件.
什麼是新羅病毒?
Shinra 病毒是 Proton 勒索軟件的一種. 一旦感染, 您的文件將根據方案重命名: .神羅3. 例如, 一個名為 “報告.docx” 會變成 “報告.docx.DQ9MBVc09h.SHINRA3”.
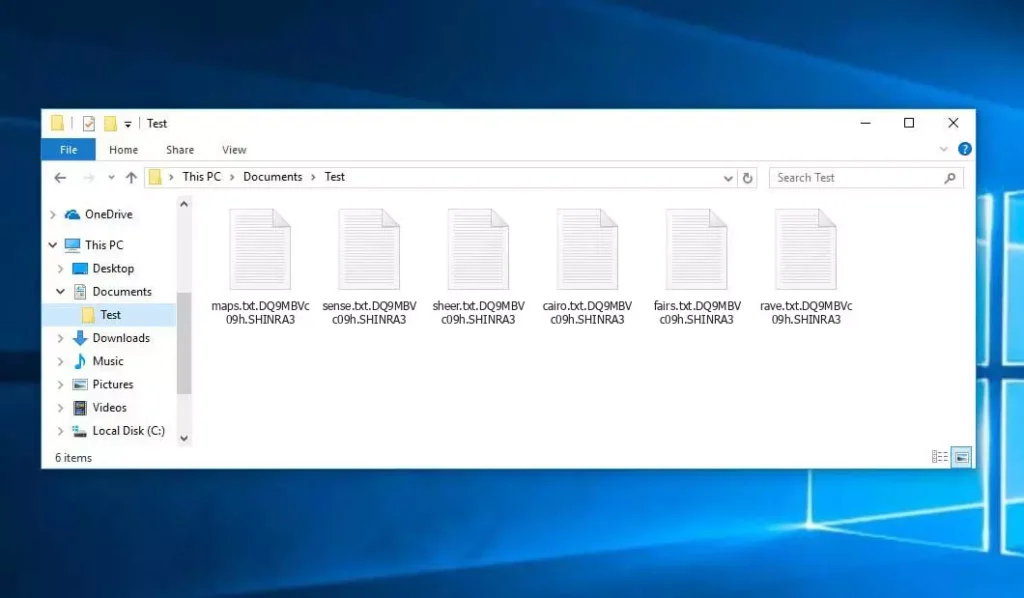
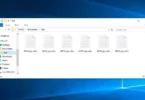
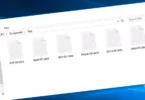
被 SHINRA 勒索軟件加密的文件 (.SHINRA3 擴展)
在每個包含加密文件的文件夾中, 你會發現一個 #SHINRA-Recovery.txt 文本文件. 該文件本質上是一張勒索信,其中提供瞭如何支付贖金並從病毒開發者那裡獲取解密工具的說明. 要獲得這個工具, 你需要聯繫 qq.decrypt@gmail.com 或者 qq.encrypt@gmail.com.
神羅總結:
| 姓名 | 神羅病毒 |
| 勒索軟件家族 | 質子 勒索軟體 |
| 擴大 | .神羅3 |
| 勒索軟體說明 | #SHINRA-Recovery.txt |
| 接觸 | qq.decrypt@gmail.com, qq.encrypt@gmail.com |
| 偵測 | 贖金:Win64/Akira.CCDR!MTB, 贖金。神羅, Win64:RansomX-gen [贖金], ML.屬性.高置信度 |
| 症狀 | 你的文件 (相片, 影片, 文件) 有一個 .SHINRA3 擴展 並且你無法打開它們. |
| 修復工具 | 查看您的系統是否已受到 Shinra 病毒的影響 |
這 #SHINRA-Recovery.txt 文檔 伴隨著 Shinra 惡意軟件 提供以下令人沮喪的信息:
~~~ SHINRA ~~~ >>> What happened? 我們加密並竊取了您的所有文件. 我們使用 AES 和 ECC 算法. 如果沒有我們的解密服務,沒有人可以恢復您的文件. >>> What guarantees? 您可以向我們發送一個不重要的文件,少於 1 MG, 我們解密它作為保證. 如果我們沒有向您發送解密軟件或刪除被盜數據, 將來沒有人付錢給我們,所以我們會信守承諾. >>> How to contact us? 我們的電子郵件地址: qq.decrypt@gmail.com 如果期限內沒有答复 24 小時, 聯繫此電子郵件: qq.encrypt@gmail.com 在電子郵件主題中寫下您的個人 ID. >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>> >>>>>>>>> Your ID: - <<<<<<<<<< >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>> >>> Warnings! - 不要去回收公司, 他們只是中間人,會從你身上賺錢並欺騙你. 他們秘密地與我們談判, 購買解密軟件, 並且會以高很多倍的價格賣給你,或者他們會簡單地欺騙你. - 不要猶豫很久. 付款速度越快, 價格越低. - 請勿刪除或修改加密文件, 這會導致文件解密出現問題.
在下面的截圖中, 你可以看到包含 Shinra 加密文件的目錄是什麼樣子的. 每個文件名都有 “.神羅3” 附加到它的擴展名.
Shinra 勒索軟件是如何出現在我的電腦上的?
勒索軟件注入的可能方式有很多種.
目前,作惡者可以通過三種最流行的方式將勒索軟件植入您的數字環境中. 這些是垃圾郵件, 木馬滲透, 和對等網絡.
- 如果您訪問郵箱並看到類似於公用事業服務提供商的通知的信件, 聯邦快遞等郵政機構, 網絡訪問提供商, 還有諸如此類的, 但你對誰的發件人感到陌生, 小心打開這些電子郵件. 它們很可能包含有害文件. 因此,下載此類電子郵件附帶的任何附件的風險更大.
- 勒索者的另一個選擇是木馬病毒模型. 特洛伊木馬是一種偽裝成合法的東西進入您的計算機的對象. 例如, 您下載了所需程序的安裝程序或某些軟件的更新. 但拆箱後發現是一種有害代理,會加密您的數據. 由於更新包可以有任何標題和任何圖標, 你必須確保你可以信任你正在下載的東西的資源. 最好的方法是信任軟件開發人員’ 官方網站.
- 至於對等文件傳輸協議,例如 torrent tracker, 危險在於它們比網絡的其他部分更加基於信任. 在獲得之前,您永遠無法知道自己下載了什麼. 所以你最好使用值得信賴的網站. 也, 下載完成後,使用反惡意軟件實用程序掃描包含下載文件的文件夾是合理的.
如何擺脫勒索軟件?
值得注意的是,除了加密您的文件之外, Shinra 病毒很可能會安裝 維達爾偷竊者 在您的計算機上訪問不同帳戶的憑據 (包括加密貨幣錢包). 該程序可以從瀏覽器的自動填充卡文件中獲取您的登錄名和密碼.
使用 Gridinsoft 反惡意軟件刪除 Shinra
從那時起我們就一直在我們的系統上使用這個軟體, 而且在檢測病毒方面一直很成功. 它阻止了最常見的勒索軟體: 從我們的測試中可以看出 與軟體, 我們向您保證,它可以刪除 Shinra 以及隱藏在您計算機上的其他惡意軟件.
使用 Gridinsoft 刪除惡意威脅, 請依照以下步驟操作:
1. 首先下載 Gridinsoft Anti-Malware, 透過下面的藍色按鈕或直接從官方網站訪問 網格軟體.
2.一旦 Gridinsoft 安裝文件 (安裝-gridinsoft-fix.exe) 已下載, 透過點擊該檔案來執行它. Follow the installation setup wizard's instructions diligently.
3. 訪問 "掃描選項卡" on the application's start screen and launch a comprehensive "全碟掃描" 檢查您的整台計算機. 這種包容性掃描涵蓋了內存, 啟動項, 註冊表, 服務, 司機, 和所有文件, 確保它檢測到隱藏在所有可能位置的惡意軟體.
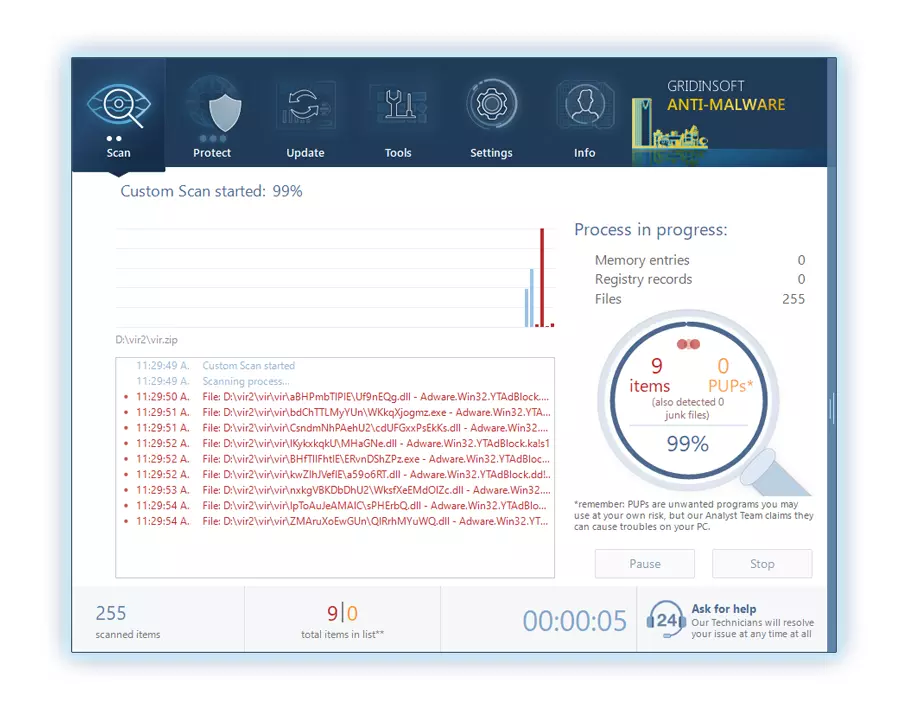
要有耐心, as the scan duration depends on the number of files and your computer's hardware capabilities. 利用這段時間放鬆或處理其他任務.
4. 完成後, 反惡意軟體將提供一份詳細報告,其中包含您 PC 上偵測到的所有惡意專案和威脅.
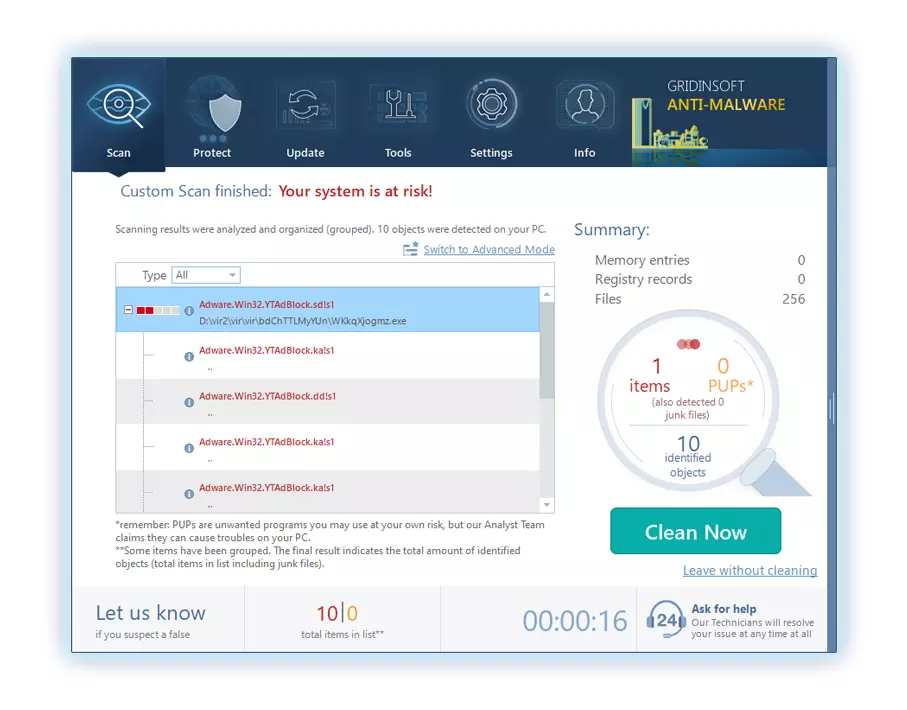
5. 從報告中選擇所有已識別的項目,然後放心地單擊 "立即清潔" 按鈕. 此操作將從您的電腦中安全地刪除惡意文件, 將它們轉移到反惡意軟體程式的安全隔離區,以防止任何進一步的有害行為.
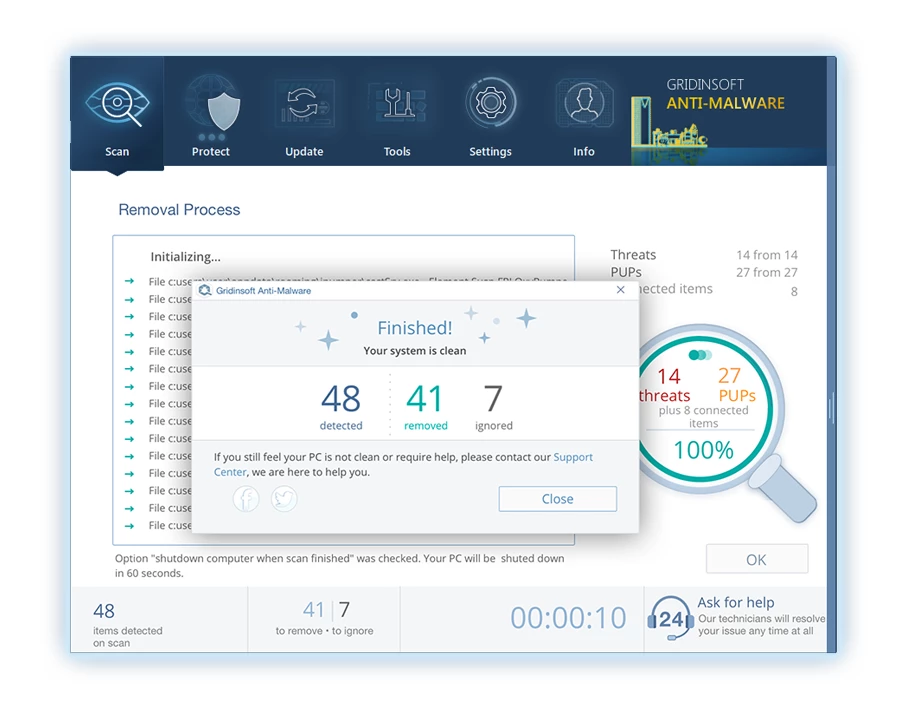
6. 如果出現提示, 重新啟動電腦以完成完整的系統掃描過程. 此步驟對於確保徹底消除任何剩餘威脅至關重要. 重啟後, Gridinsoft Anti-Malware 將會開啟並顯示一則訊息,確認 掃描完成.
請記住 Gridinsoft 提供 6 天免費試用. 這意味著您可以免費利用試用期體驗軟體的全部優勢,並防止您的系統將來受到任何惡意軟體感染. Embrace this opportunity to fortify your computer's security without any financial commitment.
通常,詐騙分子會解碼您的多個文件,以證明他們確實擁有解密工具. 由於 Shinra 病毒是一種相對較新的勒索軟件, 安全措施 開發人員尚未找到撤銷其工作的方法. 然而, 解密工具經常更新, 因此有效的對策可能很快就會到來.
可以理解, 如果犯罪分子成功對某人的重要文件進行編碼, 絕望的人可能會滿足他們的要求. 然而, 支付贖金並不能保證您能取回文件. 還是有風險的. 收到贖金後, 詐騙者可能會向受害者提供錯誤的解密代碼. 有報導稱,犯罪分子在收到贖金後就消失了,甚至沒有回信.
對付勒索軟件的最佳對策是在雲存儲或至少外部存儲中擁有系統還原點或重要文件的副本. 當然, 這可能還不夠. 最重要的事情可能是一切開始時你正在做的事情. 但至少它是一些東西. 在操作系統恢復後,使用防病毒程序掃描您的電腦是否有病毒也是合理的.
還有其他勒索軟件產品, 除了神羅, 其工作原理類似. 這些例子是 BGJS, 和 BGZQ 勒索軟件. 它們與神羅的兩個基本區別是贖金金額和加密方法. 其餘部分幾乎相同: 文件被阻止, 他們的擴展名改變了, 並在每個包含加密文件的文件夾中創建勒索字條.
一些幸運的用戶能夠在反勒索軟件專家提供的免費軟件的幫助下解密被阻止的文件. 有時,詐騙分子會無意中將勒索信中的解密密鑰發送給受害人. 如此史詩般的失敗讓受傷的部分恢復了文件. 但自然地, 永遠不應該依賴這樣的機會. 記住, 勒索軟件是犯罪分子從受害者身上騙取金錢的工具.
如何避免勒索軟件滲透?
Shinra 勒索軟件沒有超能力, 任何類似的惡意軟件也沒有.
您可以通過幾個簡單的步驟來保護您的計算機免受注入:
- 忽略來自未知發件人且地址奇怪的任何信件, 或者與您期望的內容無關的內容 (你能在不參加抽獎的情況下中獎嗎?). 如果電子郵件主題或多或少符合您的預期, 仔細檢查可疑信件的所有內容. 惡作劇信中總會有錯誤.
- 不要使用破解或不受信任的程序. 木馬經常作為破解產品的一部分傳播, 可能以“補丁”為幌子阻止許可證檢查. 但很難區分潛在危險的程序和值得信賴的程序, 因為木馬有時具有您需要的功能. 嘗試在反惡意軟件論壇上搜索有關此軟件產品的信息, 但最好的解決方案是根本不使用此類程序.
- 最後, 確保您下載的對象的安全性, 使用 GridinSoft 反惡意軟件檢查它們. 該程序將為您的系統提供強大的防禦.
常見問題
🤔 是 “.神羅3” 文件可訪問?
很遺憾, 不. 你需要破譯 “.神羅3” 文件優先. 然後你就可以打開它們.
🤔 我應該怎樣做才能讓我的文件盡快被訪問?
如果您有遠見地在其他地方保存了這些重要文件的副本,那就太好了. 如果不, 仍有系統還原功能,但需要預先保存還原點. 所有其他解決方案都需要時間.
🤔 如果 GridinSoft 刪除了 Shinra 惡意軟件, 它還會刪除我的加密文件嗎?
決不! 您的加密文件不會對您的電腦構成威脅.
GridinSoft Anti-Malware 僅處理活動病毒. 已滲透到您 PC 的勒索軟件必須仍然處於活動狀態,並且它會定期掃描您的系統,以捕獲您在初次攻擊後可能在 PC 上創建的任何新文件. 正如上面所說, Shinra 惡意軟件並不是單獨出現的. 它會安裝後門和鍵盤記錄程序,可以通過侵入的方式獲取您的帳戶密碼,並在一段時間後讓犯罪分子輕鬆訪問您的系統.
🤔 如果 Shinra 勒索軟件封鎖了我的電腦並且我無法獲取激活碼該怎麼辦.
在如此不幸的情況下, 你需要準備一個 之前安裝過特洛伊木馬殺手的記憶棒. 使用安全模式進行清理. 你看, 勒索軟件會在系統啟動時自動運行,並對創建或導入電腦的任何新文件進行編碼. 阻止此功能 – 使用安全模式, 僅允許基本程序自動運行. 考慮閱讀我們有關以安全模式啟動 Windows 的手冊.
🤔 什麼可以幫助解決現在的情況?
一些加密數據可以在其他地方找到.
- 如果您通過電子郵件發送或接收重要文件, 您仍然可以從您的在線郵箱下載它們.
- 您可能與朋友或家人分享過圖像或視頻. 只需要求他們將這些圖像發回給您即可.
- 如果您最初是從 Internet 獲取任何文件, 你可以再嘗試一次.
- 你的使者, 社交網絡頁面, 雲驅動器可能也有所有這些文件.
- 也許您的舊電腦上仍然有所需的文件, 一台筆記本電腦, 智慧型手機, 快閃記憶體, ETC.



發表評論