The Shinra virus is part of the Proton ransomware family. This type of ransomware encrypts all data on your PC—including photos, text files, spreadsheets, audio, and video files—and adds a unique extension to each file. It also leaves a #SHINRA-Recovery.txt file in every folder that contains encrypted files.
What is the Shinra virus?
The Shinra virus is a type of Proton ransomware. Once infected, your files will be renamed according to the scheme: .SHINRA3. Örneğin, a file named “report.docx” would change to “report.docx.DQ9MBVc09h.SHINRA3”.
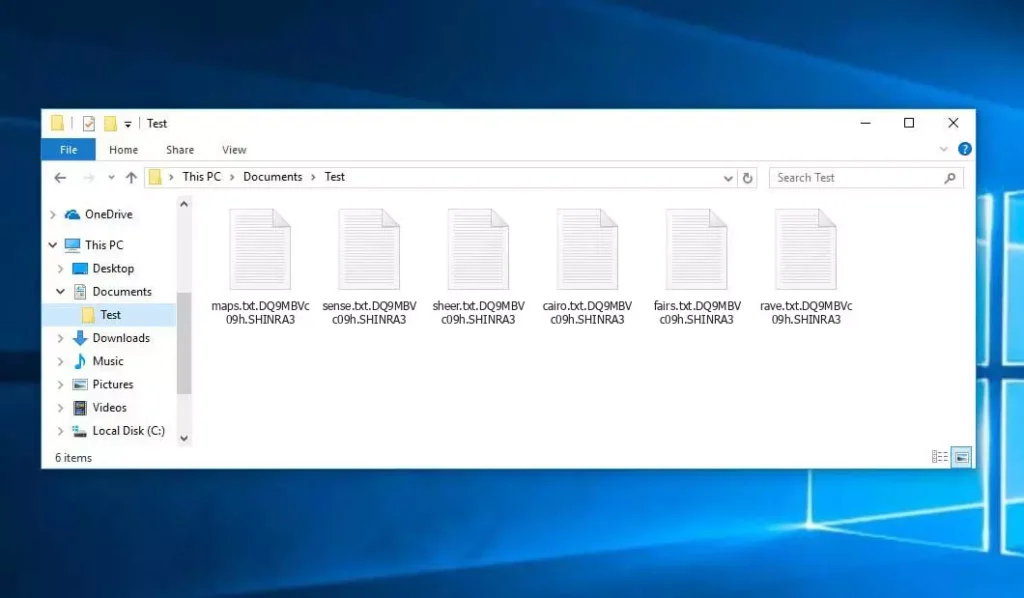
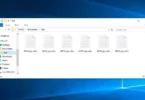
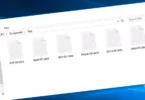
Files encrypted by SHINRA ransomware (.SHINRA3 extension)
In every folder with encrypted files, you’ll find a #SHINRA-Recovery.txt text file. This file is essentially a ransom note that provides instructions on how to pay the ransom and obtain a decryption tool from the virus developers. To get this tool, you need to contact qq.decrypt@gmail.com veya qq.encrypt@gmail.com.
Shinra Summary:
| İsim | Shinra Virus |
| Ransomware family | Proton fidye yazılımı |
| Eklenti | .SHINRA3 |
| Fidye yazılımı notu | #SHINRA-Recovery.txt |
| Temas etmek | qq.decrypt@gmail.com, qq.encrypt@gmail.com |
| Algılama | Fidye:Win64/Akira.CCDR!dağ bisikleti, Ransom.Shinra, Win64:RansomX-gen [Fidye], ML.Attribute.HighConfidence |
| Belirtiler | Your files (fotoğraflar, videolar, belgeler) have a .SHINRA3 extension and you can’t open them. |
| Fix Tool | See If Your System Has Been Affected by Shinra virus |
The #SHINRA-Recovery.txt document accompanying the Shinra malware provides the following dispiriting information:
~~~ SHINRA ~~~ >>> What happened? We encrypted and stole all of your files. We use AES and ECC algorithms. Nobody can recover your files without our decryption service. >>> What guarantees? You can send us an unimportant file less than 1 MG, We decrypt it as guarantee. If we do not send you the decryption software or delete stolen data, no one will pay us in future so we will keep our promise. >>> How to contact us? Our email address: qq.decrypt@gmail.com In case of no answer within 24 saat, contact to this email: qq.encrypt@gmail.com Write your personal ID in the subject of the email. >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>> >>>>>>>>> Your ID: - <<<<<<<<<< >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>> >>> Warnings! - Do not go to recovery companies, they are just middlemen who will make money off you and cheat you. They secretly negotiate with us, buy decryption software, and will sell it to you many times more expensive or they will simply scam you. - Do not hesitate for a long time. The faster you pay, the lower the price. - Do not delete or modify encrypted files, it will lead to problems with decryption of files.
In the screenshot below, you can see what a directory with files encrypted by Shinra looks like. Each filename has the “.SHINRA3” extension appended to it.
How did Shinra ransomware end up on my PC?
There are many possible ways of ransomware injection.
There are currently three most popular ways for evil-doers to have ransomware settled in your digital environment. These are email spam, Trojan infiltration, and peer networks.
- If you access your mailbox and see letters that look just like notifications from utility services providers, postal agencies like FedEx, web-access providers, and whatnot, but whose addresser is strange to you, beware of opening those emails. They are very likely to have a harmful file enclosed in them. So it is even riskier to download any attachments that come with emails like these.
- Another option for ransom hunters is a Trojan virus model. A Trojan is an object that gets into your machine pretending to be something legal. Örneğin, you download an installer of some program you want or an update for some software. But what is unboxed turns out to be a harmful agent that encrypts your data. Since the update package can have any title and any icon, you have to make sure that you can trust the resources of the things you’re downloading. The optimal way is to trust the software developers’ official websites.
- As for the peer file transfer protocols like torrent trackers, the danger is that they are even more trust-based than the rest of the Web. You can never know what you download until you get it. So you’d better be using trustworthy websites. Ayrıca, it is reasonable to scan the folder containing the downloaded files with the anti-malware utility as soon as the downloading is complete.
How do I get rid of ransomware?
It is crucial to note that besides encrypting your files, the Shinra virus will most likely install Vidar Hırsızı on your machine to get access to credentials to different accounts (including cryptocurrency wallets). That program can derive your logins and passwords from your browser’s auto-filling cardfile.
Remove Shinra with Gridinsoft Anti-Malware
O zamandan beri bu yazılımı sistemlerimizde de kullanıyoruz., ve virüsleri tespit etmede her zaman başarılı olmuştur. En yaygın Ransomware'i şu şekilde engelledi: testlerimizde gösterildi yazılım ile, and we assure you that it can remove Shinra as well as other malware hiding on your computer.
Kötü niyetli tehditleri kaldırmak için Gridinsoft'u kullanmak için, Aşağıdaki adımları takip et:
1. Gridinsoft Anti-Malware'i indirerek başlayın, Aşağıdaki mavi düğmeyle veya doğrudan resmi web sitesinden erişilebilir gridinsoft.com.
2.Gridinsoft kurulum dosyası bir kez (setup-gridinsoft-fix.exe) indirildi, dosyaya tıklayarak çalıştırın. Follow the installation setup wizard's instructions diligently.
3. Erişmek "Tarama Sekmesi" on the application's start screen and launch a comprehensive "Tam tarama" tüm bilgisayarınızı incelemek için. Bu kapsamlı tarama hafızayı kapsar, başlangıç öğeleri, kayıt defteri, Hizmetler, sürücüler, ve tüm dosyalar, olası tüm konumlarda gizlenmiş kötü amaçlı yazılımları tespit etmesini sağlamak.
Sabırlı ol, as the scan duration depends on the number of files and your computer's hardware capabilities. Bu zamanı rahatlamak veya diğer görevlere katılmak için kullanın.
4. Bitmesi uzerine, Anti-Malware, PC'nizde tespit edilen tüm kötü amaçlı öğeleri ve tehditleri içeren ayrıntılı bir rapor sunacaktır..
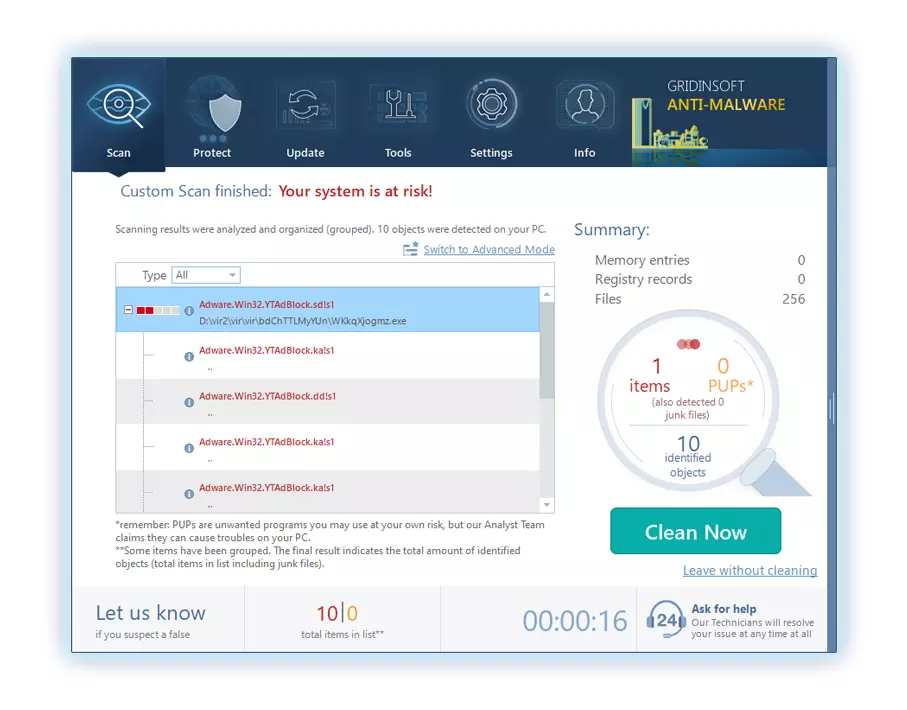
5. Rapordan tanımlanan tüm öğeleri seçin ve güvenle "Şimdi Temizle" düğme. Bu eylem, kötü amaçlı dosyaları bilgisayarınızdan güvenli bir şekilde kaldıracaktır., daha fazla zararlı eylemi önlemek için bunları kötü amaçlı yazılımdan koruma programının güvenli karantina bölgesine aktarmak.
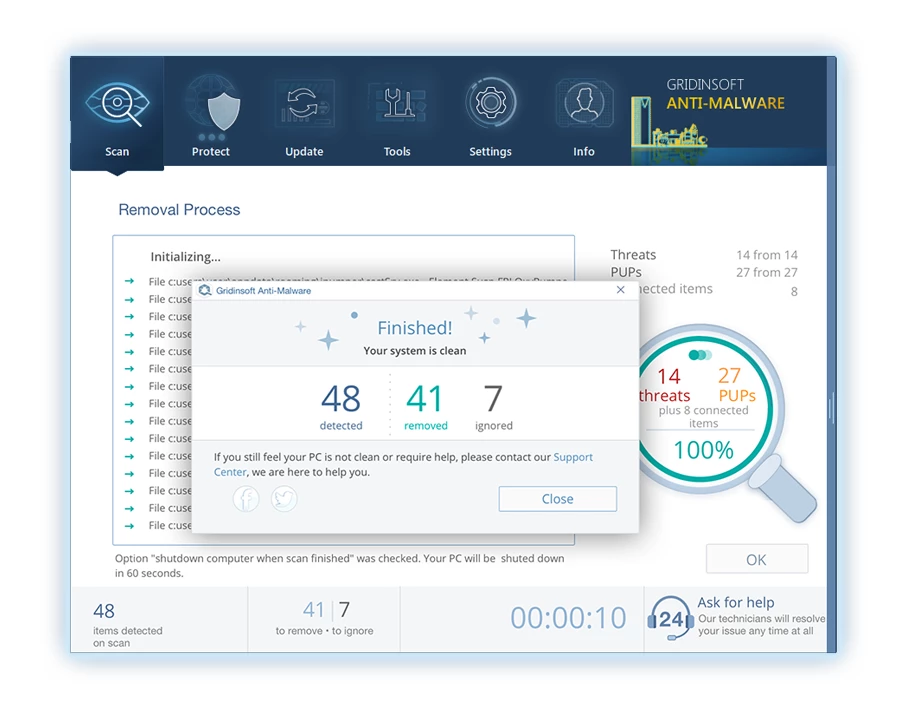
6. İstenirse, Tam sistem tarama prosedürünü tamamlamak için bilgisayarınızı yeniden başlatın. Bu adım, kalan tehditlerin tamamen ortadan kaldırılmasını sağlamak için çok önemlidir.. Yeniden başlatmanın ardından, Gridinsoft Anti-Malware açılacak ve işlemi onaylayan bir mesaj görüntüleyecektir. taramanın tamamlanması.
Gridinsoft'un 6 günlük ücretsiz deneme sunduğunu unutmayın. Bu, yazılımın tüm avantajlarından yararlanmak ve gelecekte sisteminize kötü amaçlı yazılım bulaşmasını önlemek için deneme süresinden ücretsiz olarak yararlanabileceğiniz anlamına gelir.. Embrace this opportunity to fortify your computer's security without any financial commitment.
Often racketeers would decode several of your files to prove that they indeed have the decryption tool. Since the Shinra virus is a relatively recent ransomware, safety measures developers have not yet found a way to undo its work. Fakat, the decryption instruments are frequently updated, so an effective countermeasure may soon arrive.
Understandably, if the criminals succeed in encoding someone’s essential files, the hopeless person will probably comply with their demands. Fakat, paying a ransom gives no guarantee that you’re getting your files back. It is still risky. After receiving the ransom, the racketeers may deliver the wrong decryption code to the victim. There were reports about criminals just disappearing after getting the ransom without even writing back.
The best countermeasure to ransomware is to have a system restore point or the copies of your essential files in the cloud storage or at least on external storage. Of course, that might be not enough. The most important thing could be the one you were working on when it all started. But at least it is something. It is also reasonable to scan your PC for viruses with the antivirus program after the OS restoration.
There are other ransomware products, besides Shinra, that work similarly. Examples of those are BGJS, Ve BGZQ Ransomware. The two basic differences between them and the Shinra are the ransom amount and the method of encryption. The rest is almost identical: files become blocked, their extensions altered, and ransom notes are created in each folder containing encrypted files.
Some fortunate users were able to decrypt the blocked files with the help of the free software provided by anti-ransomware experts. Sometimes the racketeers accidentally send the decoding key to the wronged in the ransom note. Such an epic fail allows the injured part to restore the files. But naturally, one should never rely on such a chance. Hatırlamak, ransomware is a criminal’s tool to pull the money out of their victims.
How to avert ransomware infiltration?
Shinra ransomware doesn’t have a superpower, neither does any similar malware.
You can protect your computer from its injection within several easy steps:
- Ignore any letters from unknown senders with strange addresses, or with content that has nothing to do with something you are expecting (can you win in a money prize draw without even taking part in it?). In case the email subject is more or less something you are expecting, scrutinize all elements of the dubious letter carefully. A hoax letter will always contain a mistake.
- Do not use cracked or untrusted programs. Trojans are often spread as a part of cracked products, possibly under the guise of “patch” preventing the license check. But potentially dangerous programs are very hard to tell from trustworthy ones, because trojans sometimes have the functionality you need. Try searching for information on this software product on the anti-malware forums, but the best solution is not to use such programs at all.
- And finally, to be sure about the safety of the objects you downloaded, check them with GridinSoft Anti-Malware. This program will be a powerful defense for your system.
Sıkça Sorulan Sorular
🤔 Are the “.SHINRA3” files accessible?
Maalesef, no. You need to decipher the “.SHINRA3” files first. Then you will be able to open them.
🤔 What should I do to make my files accessible as fast as possible?
It’s good if you have fаr-sightedly saved copies of these important files elsewhere. If not, there is still a function of System Restore but it needs a Restore Point to be previously saved. All other solutions require time.
🤔 If GridinSoft deletes the Shinra malware, will it also delete my files that were encrypted?
No way! Your encrypted files are no threat to your PC.
GridinSoft Anti-Malware only deals with active viruses. The ransomware that has infiltrated your PC is must be still active and it scans your system periodically to arrest any new files you might create on your PC after the initial attack. As it has been said above, the Shinra malware does not come alone. It installs backdoors and keyloggers that can take your account passwords by trespass and provide malefactors with easy access to your system after some time.
🤔 What to do if the Shinra ransomware has blocked my computer and I can’t get the activation code.
In such an unfortunate situation, you need to prepare a memory stick with a previously installed Trojan Killer. Use Safe Mode to do the cleaning. You see, the ransomware runs automatically as the system launches and encodes any new files created or imported into your PC. To block this function – use Safe Mode, which allows only the essential programs to run automatically. Consider reading our manual on booting Windows in Safe Mode.
🤔 What could help the situation right now?
Some of the encrypted data can be found elsewhere.
- If you sent or received your important files via email, you could still download them from your online mailbox.
- You might have shared images or videos with your friends or family members. Just ask them to send those images back to you.
- If you have initially got any of your files from the Internet, you can try doing it again.
- Your messengers, social networks pages, and cloud drives might have all those files as well.
- Maybe you still have the needed files on your old PC, a laptop, cellphone, flash memory, etc.



Yorum Yap