Vehu는 어떤 악성코드인가??
Vehu는 제출 된 샘플 분석 중에 발견 한 DJVU 제품군의 랜섬웨어 변형입니다. virustotal. 랜섬웨어는 파일을 암호화하고 해독에 대한 지불을 요구하는 맬웨어 유형입니다.. 파일을 암호화하는 것 외에도, 차량은 확장을 추가합니다 (“.차량”) 파일 이름 및 몸값 메모를 제공합니다 (“_readme.txt“).
Vehu로 암호화 된 파일의 이름이 바뀌는 방법의 예: “1.JPG” 변경됩니다 “1.jpg.vehu“, “2.PNG” 에게 “2.png.vehu“, 등. Vehu는 DJVU 가족의 일부이기 때문에, Vidar 및 Redline과 같은 정보 도용가와 함께 배포 될 수 있습니다..
Vehu Ransomware로 암호화 된 파일 스크린 샷:
감염된 PC: VEHU 파일
Vehu Ransom Note 개요
Vehu 's Ransom Note는 피해자에게 파일을 암호화하고 복구하는 유일한 방법은 암호 해독 도구와 고유 한 키를 구매하는 것입니다.. 또한 공격자는 하나의 파일을 해독하도록 제안한다고 말합니다. (귀중한 정보를 포함하지 않습니다) 무료로. 이 노트는 두 개의 연락처 이메일을 제공합니다: support@freshingmail.top 및 datarestorehelpyou@airmail.cc.
암호 해독 가격을 제공합니다 $999 그리고 그것이 줄어들 수 있다고 말합니다 $499 피해자가 위협 행위자에게 연락하는 경우 72 시간. 마지막으로, 피해자가 결제하지 않고 데이터를 복원 할 수 없도록합니다..
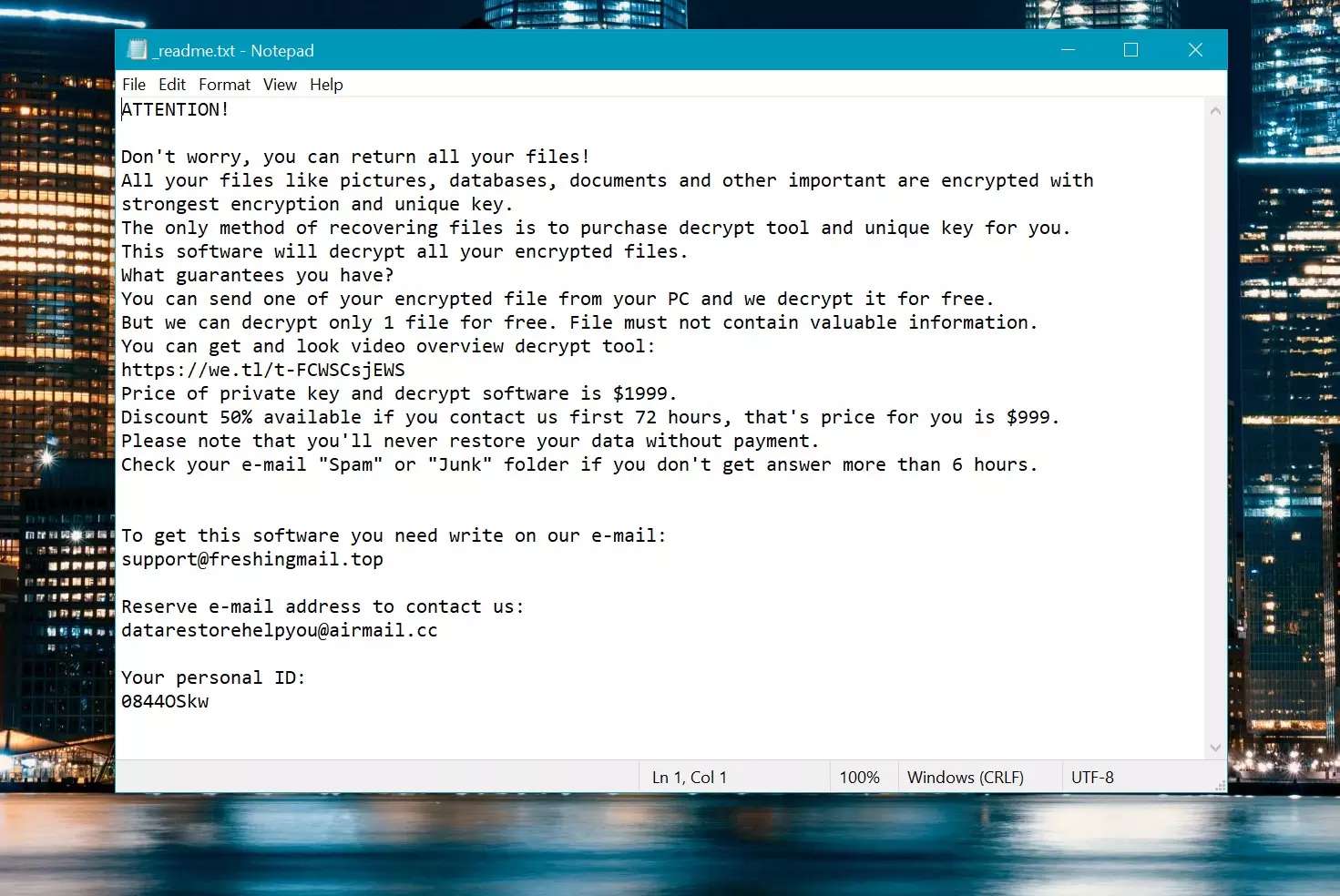
몸값 메모: _readme.txt
| 이름 | 차량 바이러스 |
| 가족 1 | 정지 / DJVU 랜섬웨어 |
| 확대 | .차량 |
| 랜섬웨어 참고 | _readme.txt |
| 몸값 | 에서 $499 에게 $999 (비트 코인에서) |
| 연락하다 | support@freshingmail.top, datarestorehelpyou@airmail.cc |
| 증상 |
|
| 회복 | 포괄적으로 복구를 시작하십시오 바이러스 백신 스캔. 모든 파일을 복구 할 수있는 것은 아니지만, 우리 가이드는 암호화 된 파일에 대한 액세스를 되 찾는 몇 가지 잠재적 방법을 설명합니다.. |
DJVU 랜섬웨어는 다단계 쉘 코드를 사용하여 활동을 시작합니다, 파일 암호화로 이어집니다. 또한, 맬웨어는 루프를 통합하여 실행 기간을 연장합니다, 보안 시스템이 맬웨어를 식별하기가 더 어려워집니다..
또한, DJVU Ransomware. 나중에, 프로세스 중공을 사용합니다, 진정한 의도를 감추기 위해 다른 과정으로 마스킹 된 복제품 만들기.
차량 랜섬웨어가 내 PC를 감염시키는 방법?
사이버 범죄자는 다양한 방식으로 랜섬웨어를 배포합니다. DJVU 랜섬웨어는 일반적으로 불법 복제 소프트웨어를 통해 제공됩니다 (또는 크래킹 도구 및 키 생성기) 그리고 YouTube에서 비디오를 다운로드하기위한 플랫폼으로 포즈를 취하는 그늘진 페이지. 악성 첨부 파일 및 링크가 포함 된 이메일도 맬웨어 배포 채널로 사용됩니다..
또한, 컴퓨터 감염은 소프트웨어 취약점을 통해 발생할 수 있습니다, 악의적 인 광고, 타협 된 웹 사이트, 드라이브 바이 다운로드, USB 드라이브가 손상되었습니다, P2P 네트워크, 비공식 페이지, 그리고 비슷한 채널. 전반적인, 대부분의 사이버 범죄자들은 사용자가 컴퓨터 감염을 초래하는 작업을 수행하는 데 유혹하는 것을 목표로합니다..
제거하는 방법?
Gridinsoft Anti-Malware로 Vehu 바이러스를 제거하십시오
우리는 또한이 소프트웨어 에서이 소프트웨어를 우리 시스템에서 사용하고 있습니다., 그리고 그것은 항상 바이러스를 감지하는 데 성공했습니다. 가장 일반적인 랜섬웨어를 차단했습니다 우리의 테스트에서 보여 주었다 소프트웨어와 함께, 그리고 우리는 그것이 당신의 컴퓨터에 숨어있는 다른 맬웨어뿐만 아니라 차량 바이러스를 제거 할 수 있음을 보증합니다..
악의적 인 위협을 제거하기 위해 Gridinsoft를 사용합니다, 아래 단계를 따르십시오:
1. Gridinsoft anti-malware를 다운로드하여 시작하십시오, 아래 또는 공식 웹 사이트에서 직접 파란색 버튼을 통해 액세스 할 수 있습니다. gridinsoft.com.
2.GridInsoft 설정 파일이되면 (Setup-gridinsoft-fix.exe) 다운로드됩니다, 파일을 클릭하여 실행하십시오. Follow the installation setup wizard's instructions diligently.
3. 액세스 "스캔 탭" on the application's start screen and launch a comprehensive "전체 스캔" 전체 컴퓨터를 검사합니다. 이 포괄적 인 스캔은 메모리를 포함합니다, 스타트 업 항목, 레지스트리, 서비스, 드라이버, 그리고 모든 파일, 가능한 모든 위치에 숨겨진 맬웨어를 감지하는지 확인.
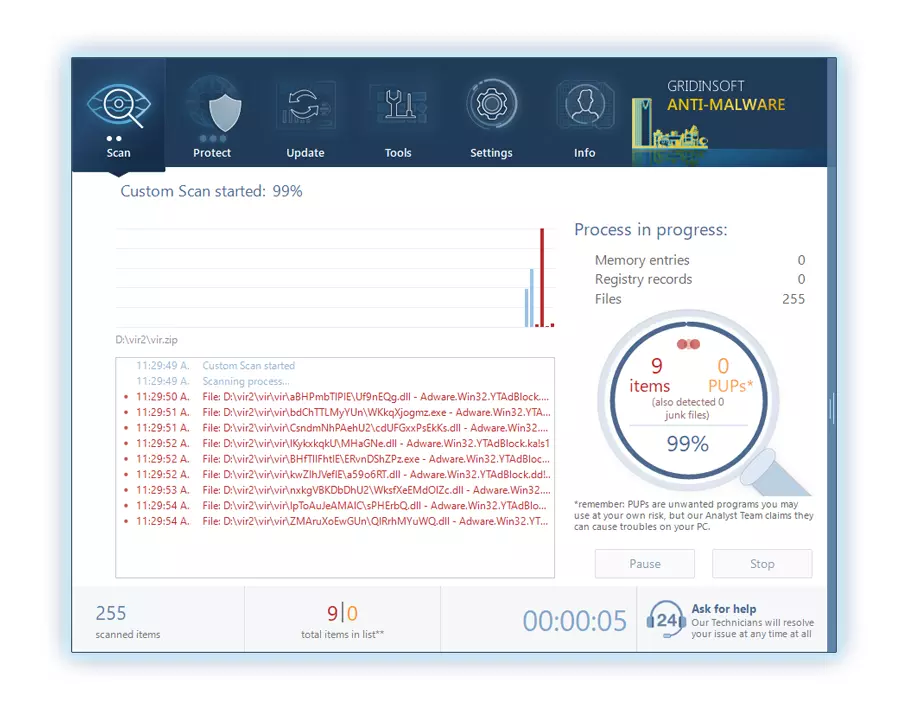
인내하십시오, as the scan duration depends on the number of files and your computer's hardware capabilities. 이 시간을 사용하여 휴식을 취하거나 다른 작업에 참석하십시오..
4. 완료되면, 방지 방지는 PC에 감지 된 모든 악성 품목 및 위협이 포함 된 자세한 보고서를 제시합니다..
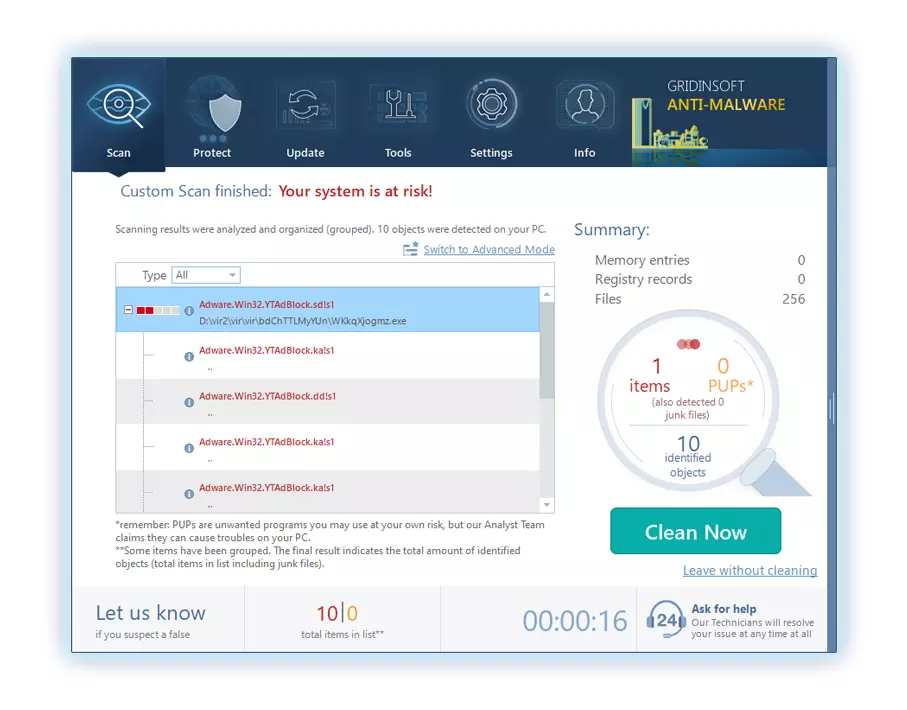
5. 보고서에서 식별 된 모든 항목을 선택하고 자신있게 "지금 청소" 단추. 이 작업은 컴퓨터에서 악의적 인 파일을 안전하게 제거합니다., 더 이상의 유해한 행동을 방지하기 위해 말장 방지 프로그램의 안전한 검역 구역으로 전송.
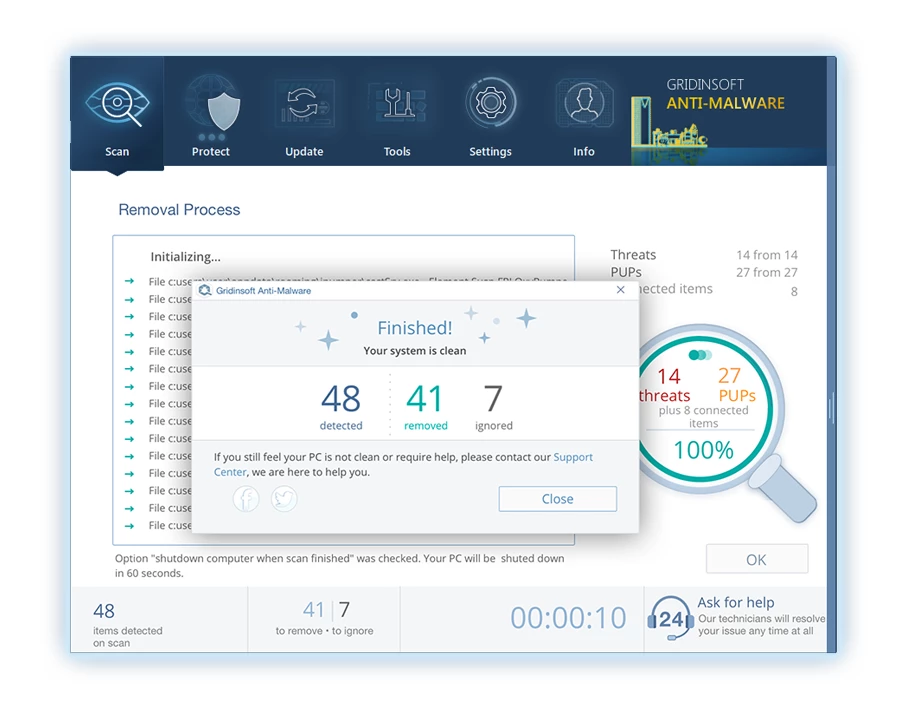
6. 프롬프트가있는 경우, 전체 시스템 스캔 절차를 마무리하려면 컴퓨터를 다시 시작하십시오.. 이 단계는 남은 위협을 철저히 제거하는 데 중요합니다.. 재시작 후, Gridinsoft anti-malware가 열리고 메시지를 표시합니다. 스캔 완료.
Gridinsoft는 6 일 무료 평가판을 제공합니다. 즉, 소프트웨어의 모든 이점을 경험하고 시스템의 향후 악성 코드 감염을 예방하기 위해 무료로 시험 기간을 이용할 수 있습니다.. Embrace this opportunity to fortify your computer's security without any financial commitment.
비디오 가이드
.vehu 파일을 해독하는 방법?
첫 번째, 삭제해보십시오 “.차량” 몇 개의 큰 파일에서 확장 한 다음 열기. 이 맬웨어는 큰 파일의 암호화로 어려움을 겪고 있습니다. 바이러스는 액세스시 파일을 잠그지 않았거나 버그가 발생하여 파일 마커를 추가하기 위해 생략했습니다.. 파일의 크기가 2GB를 초과하는 경우, 후자의 시나리오는 더 가능성이 높습니다.
범죄자들은 8 월 말경에 최신 확장을 발표했습니다. 2019 몇 가지 변경 후.
범죄자들의 변화는 스톱 드릴드를지지하지 않았다, Emsisoft가 개발 한 STOP DJVU Ransomware 용 Emsisoft 해독자로 교체합니다..
- 암호 해독 도구를 다운로드하여 실행하십시오: 다운로드 암호 해독 도구. 암호 해독 유틸리티를 관리자로 실행하고 “예” 단추. 라이센스 조건을 수락하면.
- 암호 해독을 위해 폴더를 선택하십시오: 해독자, 기본적으로, Connected 및 네트워크 드라이브에서 디렉토리를 자동으로 선택합니다.. 사용하십시오 “추가하다” 추가 위치를 선택하는 버튼. 맬웨어 패밀리에 따라, 해독제는 다양한 옵션을 제공합니다, 옵션 탭에서 켜거나 끌 수있는 것. 아래에, 현재 활성화 된 옵션의 자세한 목록을 찾을 수 있습니다..
- 클릭하여 암호 해독을 시작하십시오 “해독” 단추. 원하는 모든 위치를 목록에 추가 한 후, 클릭하십시오 “해독” 암호 해독 프로세스를 시작하려면 버튼. 해독자는 암호 해독 과정을 완료하면 알려줄 것입니다.. 문서에 필요한 경우, 클릭하여 보고서를 저장할 수 있습니다 “로그를 저장하십시오” 단추. 이메일이나 메시지에 붙여 넣기 위해 보고서를 클립 보드에 복사 할 수도 있습니다..
.vehu 파일을 복원하는 방법?
어떤 경우에는, 랜섬웨어는 파일을 암호화하지 못합니다…
Vehu Ransomware 암호화 프로세스에는 각 파일을 바이트별로 암호화하는 것이 포함됩니다., 중복을 만듭니다, 그런 다음 삭제합니다 (덮어 쓰지 않습니다) 원본 파일. 이 삭제는 물리적 디스크가 더 이상 시스템에 파일을 나열하지 않음을 의미합니다., 원래 파일은 드라이브에 남아 있지만. 파일을 보유한 부문에는 여전히이를 포함 할 수 있습니다., 그러나 시스템이 나열되지 않기 때문에, 새로운 데이터가이를 덮어 쓸 수 있습니다. 하지만, 특수 소프트웨어는 파일을 복구 할 수 있습니다.
온라인 알고리즘이라는 것을 깨달았습니다, 암호화 된 파일을 복구하는 것이 불가능하다는 것을 알았습니다. 내 백업 드라이브, 감염 중에 연결되었습니다, 감염된 것처럼 보였다. 백업 드라이브의 모든 폴더가 암호화 된 것으로 나타났습니다. 그럼에도 불구하고, 나는 거의 회복했다 80% 내 2TB 스토리지의.
폴더 검사, 각각에서 몸값 노트를 찾았습니다. 일부는 서브 폴더에없는 파일 만 암호화 된 것으로 밝혀졌습니다.. 다른 폴더의 하위 폴더를 탐구합니다, 암호화되지 않은 파일을 발견했습니다. 내 C 및 D는 모든 폴더에서 운전하는 것과 달리, 서브 폴더 포함, 암호화되었습니다, 백업 드라이브의 하위 폴더가 저장되었습니다 80% 내 데이터의.
백업 드라이브 에서이 허점을 찾는 것이 좋습니다.. 또한, 나는 다른 것을 회복했다 10% 다른 PC의 하드 드라이브에서 내 데이터 중. 따라서, 백업 드라이브 사용에 대한 조언은 Subfolders를 만드는 것입니다.. 그것은 부분적으로 운이었다, 그러나 내 백업에서 파일 전송 중에 바이러스가 닥친다는 불행.
이 경험이 비슷한 곤경에서 다른 사람들을 도울 수 있기를 바랍니다..
제이미 뉴 랜드Phathorec으로 Vehu 파일을 복구하십시오
Photorec, 손상된 디스크 또는 우발적 인 삭제로부터 파일 복구를 위해 설계, 이제 복원을 지원합니다 400 파일 유형, 차량 공격 후 유용하게 만듭니다.
첫 번째, Photorec를 다운로드하십시오. 무료입니다, 그러나 개발자는 파일 복원을 보장하지 않습니다. Photorec에는 TestDisk가 포장되어 있습니다, 같은 개발자의 또 다른 도구, TestDisk 이름 아래. 하지만, Photorec은 아카이브 내에 포함되어 있습니다.
Photorec을 시작합니다, 열기 “qphotorec_win.exe” 파일. 프로그램에 필요한 모든 파일이 포함되어 있으므로 설치가 필요하지 않습니다., USB 드라이브에서 실행할 수 있습니다.



의견을 남겨주세요