Vepi is a ransomware variant from the Djvu family that we discovered during an analysis of samples submitted to VirusTotal. Ransomware is a type of malware that encrypts files and demands payment for their decryption. In addition to encrypting files, Vepi appends its extension (“.vepi”) to filenames and provides a ransom note (“_README.txt“).
An example of how files encrypted by Vepi are renamed: “1.jpg” is changed to “1.jpg.vepi“, “2.png” to “2.png.vepi“, and so on. Since Vepi is part of the Djvu family, it may be distributed alongside information stealers like Vidar and RedLine.
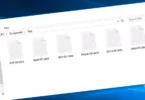
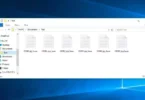
Screenshot of files encrypted by Vepi ransomware:
Vepi Files
Vepi ransom note overview
Vepi’s ransom note informs victims that their files are encrypted and that purchasing a decryption tool and a unique key is the only way to recover them. It also says that the attackers offer to decrypt one file (not containing valuable information) for free. The note provides two contact emails: support@freshingmail.top and datarestorehelpyou@airmail.cc.
It provides the price of decryption $999 and says it can be reduced to $499 if victims contact threat actors within 72 時間. Lastly, it ensures victims that data cannot be restored without payment.
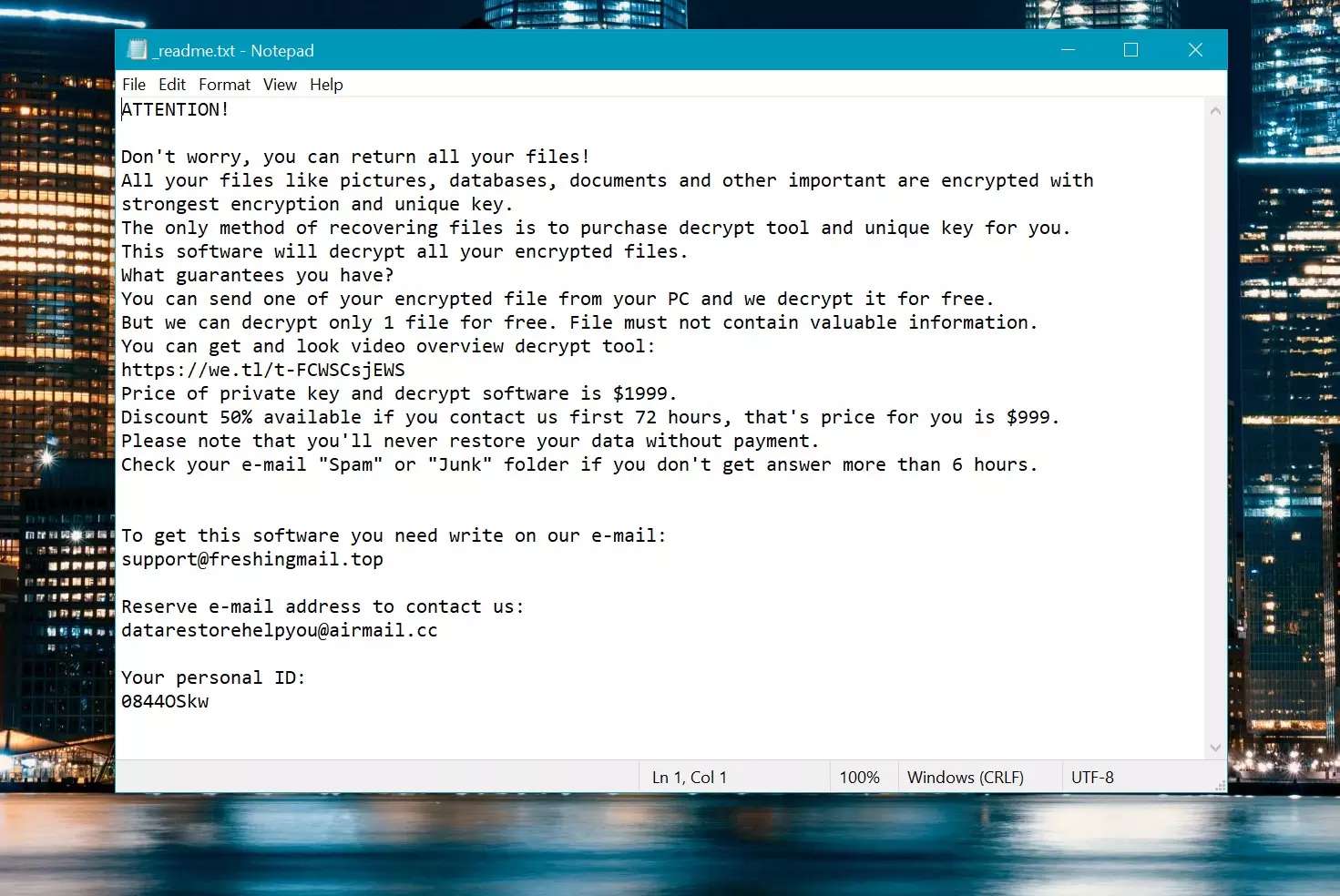
Ransom Note: _readme.txt
| 名前 | Vepi Virus |
| Family 1 | STOP/Djvu Ransomware |
| 拡大 | .vepi |
| ランサムウェアに関するメモ | _readme.txt |
| 身代金 | From $499 to $999 (in Bitcoins) |
| 接触 | support@freshingmail.top, datarestorehelpyou@airmail.cc |
| 症状 |
|
| Recovery | Start recovery with a comprehensive antivirus scan. Although not all files may be recoverable, our guide outlines several potential methods to regain access to encrypted files. |
Djvu ransomware initiates its activities by utilizing multi-stage shellcodes, leading to file encryption. さらに, the malware integrates loops to extend its execution duration, making it harder for security systems to identify the malware.
また, Djvu ransomware employs dynamic API resolution to access vital tools covertly. Later, it utilizes process hollowing, creating a replica of itself masked as another process to conceal its true intent.
How Vepi ransomware infect my PC?
Cybercriminals distribute ransomware in various ways. Djvu ransomware is commonly delivered via pirated software (or cracking tools and key generators) and shady pages posing as platforms for downloading videos from YouTube. Emails containing malicious attachments and links are also used as malware distribution channels.
さらに, computer infections can occur through software vulnerabilities, malicious advertisements, compromised websites, drive-by downloads, compromised USB drives, P2P networks, unofficial pages, and similar channels. Overall, most cybercriminals aim to lure users into performing actions resulting in computer infections.
How To Remove?
Remove Vepi Virus with Gridinsoft Anti-Malware
それ以来、当社のシステムでもこのソフトウェアを使用しています。, ウイルスの検出には常に成功しています. 最も一般的なランサムウェアをブロックしました。 私たちのテストから示された ソフトウェアを使って, and we assure you that it can remove Vepi Virus as well as other malware hiding on your computer.
Gridinsoft を使用して悪意のある脅威を削除するには, 以下の手順に従ってください:
1. まずは Gridinsoft Anti-Malware をダウンロードしてください, 下の青いボタンから、または公式ウェブサイトから直接アクセスできます グリディンソフト.com.
2.Gridinsoft セットアップ ファイルが完成したら (setup-gridinsoft-fix.exe) ダウンロードされています, ファイルをクリックして実行します. Follow the installation setup wizard's instructions diligently.
3. にアクセスしてください "スキャンタブ" on the application's start screen and launch a comprehensive "フルスキャン" コンピュータ全体を調べるには. この包括的なスキャンはメモリを網羅します。, スタートアップアイテム, レジストリ, サービス, 運転手, そしてすべてのファイル, 考えられるすべての場所に隠されたマルウェアを確実に検出する.
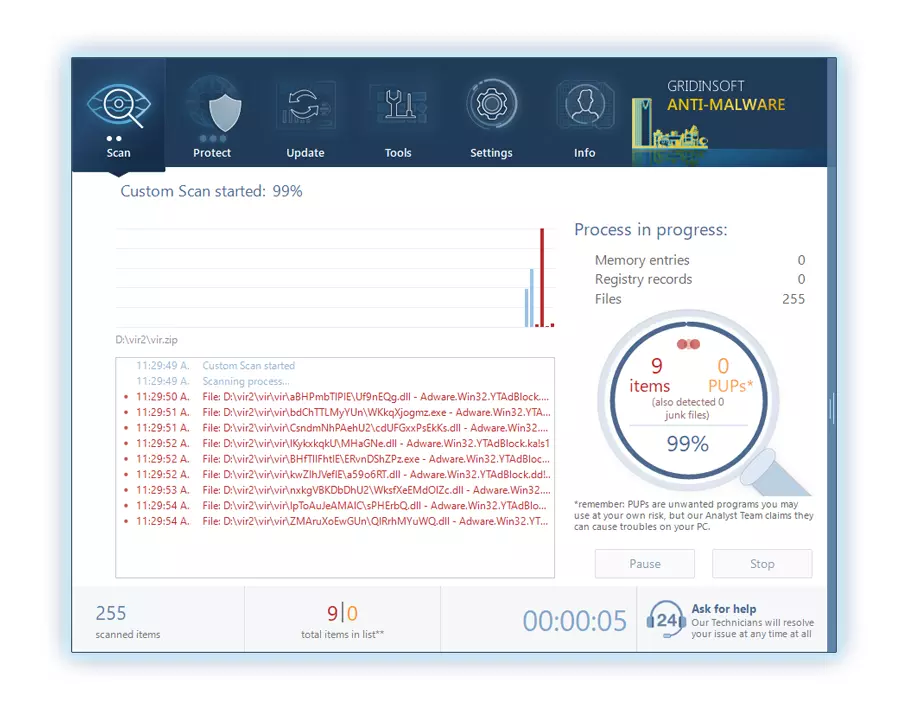
我慢して, as the scan duration depends on the number of files and your computer's hardware capabilities. この時間をリラックスしたり、他のタスクに集中したりするために使用してください.
4. 完了時に, マルウェア対策は、PC 上で検出されたすべての悪意のあるアイテムと脅威を含む詳細なレポートを表示します。.
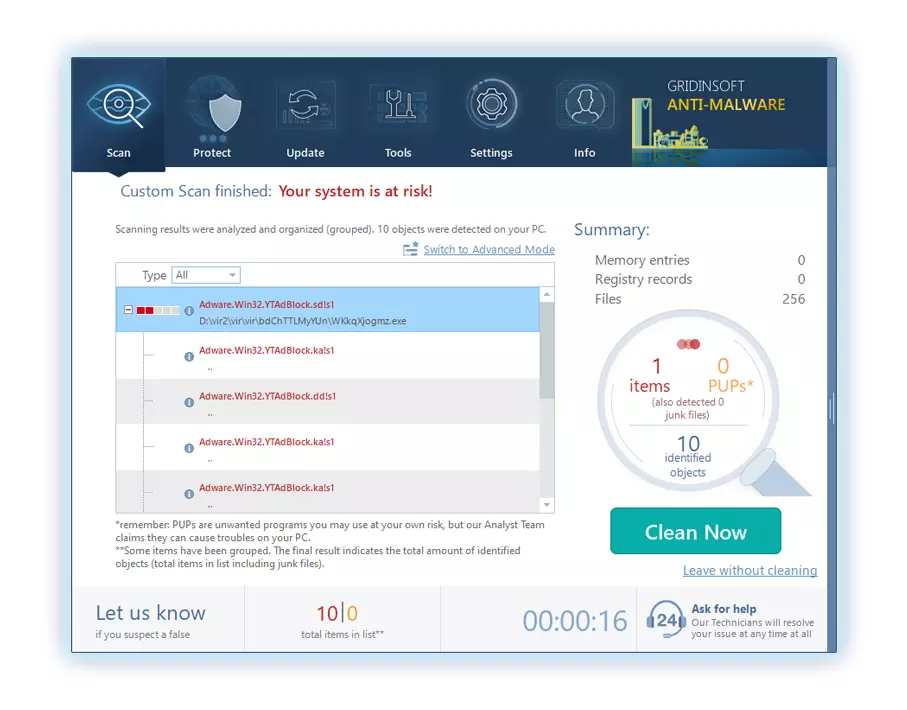
5. レポートから特定された項目をすべて選択し、自信を持って "今すぐ掃除してください" ボタン. この操作により、悪意のあるファイルがコンピュータから安全に削除されます, さらなる有害な行為を防ぐために、それらをマルウェア対策プログラムの安全な隔離ゾーンに転送します。.
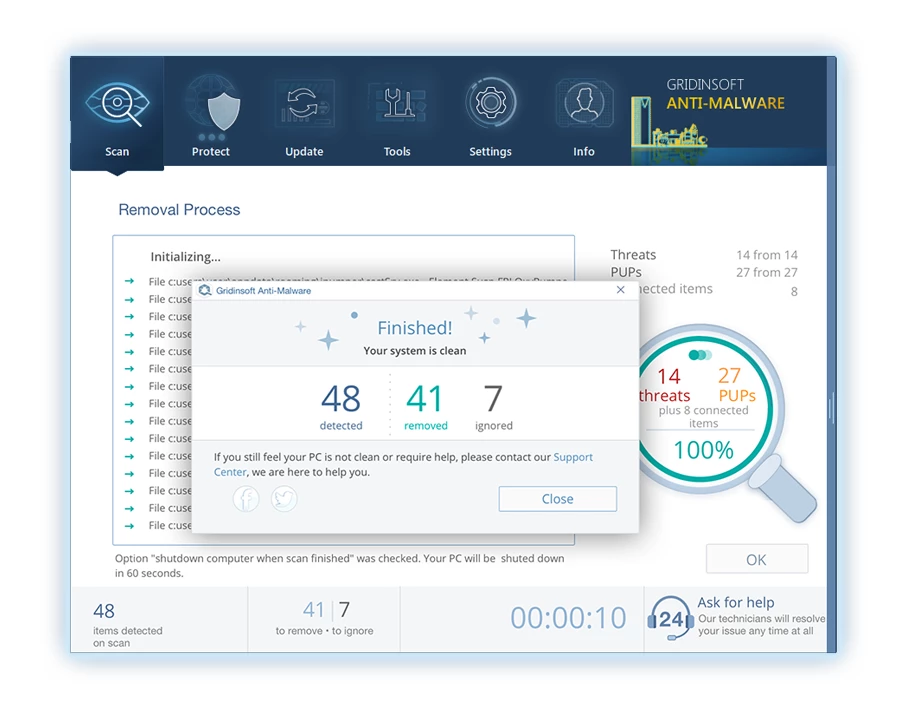
6. プロンプトが表示された場合, コンピュータを再起動して、システム全体のスキャン手順を完了します。. このステップは、残っている脅威を確実に完全に除去するために重要です。. 再起動後, Gridinsoft Anti-Malware が開き、次のことを確認するメッセージが表示されます。 スキャンの完了.
Gridinsoft は 6 日間の無料トライアルを提供していることを忘れないでください. つまり、無料の試用期間を利用してソフトウェアの利点を最大限に体験し、システムでの今後のマルウェア感染を防ぐことができます。. Embrace this opportunity to fortify your computer's security without any financial commitment.
Video Guide
How To Decrypt .vepi Files?
First, try deleting the “.vepi” extension from a few big files and then opening them. This malware struggles with the encryption of large files. The virus either failed to lock the file upon access or encountered a bug and omitted to add the file marker. If your files exceed 2GB in size, the latter scenario is more probable.
Criminals released the newest extensions around the end of August 2019 after making several changes.
The changes by the criminals rendered STOPDecrypter unsupported, leading to its replacement with the Emsisoft Decryptor for STOP Djvu Ransomware developed by Emsisoft.
- Download and Run the Decryption Tool: Download decryption tool. Ensure you run the decryption utility as an administrator and agree to the license terms that appear by clicking the “Yes” ボタン. Upon accepting the license terms.
- Select Folders for Decryption: The decryptor, by default, automatically selects directories on connected and network drives for decryption. Use the “Add” button to select additional locations. Depending on the malware family, decryptors offer various options, which you can toggle on or off in the Options tab. Below, you will find a detailed list of the currently active options.
- Initiate Decryption by Clicking on the “Decrypt” Button. After adding all desired locations to the list, click the “Decrypt” button to start the decryption process. The decryptor will inform you upon completing the decryption process. If needed for documentation, you can save the report by clicking the “Save log” ボタン. It’s also possible to copy the report to your clipboard for pasting into emails or messages.
How to Restore .vepi Files?
場合によっては, ransomware fails to encrypt your files…
The Vepi ransomware encryption process involves encrypting each file byte-by-byte, creating a duplicate, and then deleting (not overwriting) the original file. This deletion means the physical disk no longer lists the file in its system, although the original file remains on the drive. The sector that held the file might still contain it, but since the system does not list it, new data can overwrite it. しかし, special software can recover your files.
Realizing it was an online algorithm, I knew recovering my encrypted files was impossible. My backup drive, connected during the infection, seemed infected as well. Every folder on my backup drive appeared encrypted. Despite this, I managed to recover nearly 80% of my 2TB storage.
Examining the folders, I found ransom notes in each. Opening some revealed that only files not in subfolders were encrypted. Delving into subfolders in other folders, I discovered unencrypted files. Unlike my C and D drives where every folder, including subfolders, was encrypted, my backup drive’s subfolders saved 80% of my data.
I consider finding this loophole on my backup drive fortunate. さらに, I recovered another 10% of my data from a hard drive on a different PC. Thus, my advice for using a backup drive is to create subfolders. It was partly luck, but also misfortune that the virus struck during file transfers from my backup.
I hope this experience can assist others in similar predicaments.
Jamie NewlandRecover Vepi Files with PhotoRec
フォトレック, designed for file recovery from damaged disks or accidental deletion, now supports restoring 400 file types, making it useful after a Vepi attack.
First, download PhotoRec. It’s free, but the developer offers no guarantee for file restoration. PhotoRec comes packaged with TestDisk, another tool from the same developer, under the TestDisk name. しかし, PhotoRec is included within the archive.
To start PhotoRec, open the “qphotorec_win.exe” file. No installation is necessary as the program contains all required files, allowing it to run from a USB drive.




コメントを残す