If your computer alerts you with the Trojan:Win32/Smokeloader!pz detection name, it’s a critical sign of danger. This detection indicates ransomware, which encrypts your files and demands a ransom for their decryption. Immediate action and specific steps are necessary to remove this malware promptly.
Il Trojan:Win32/Smokeloader!pz virus is commonly detected after engaging in risky activities on your computer, such as opening suspicious emails, clicking on online ads, or downloading software from unreliable sources. Once detected, swift action is essential to prevent its harmful effects. Delaying can lead to severe damage, so it’s crucial to act quickly.
Understanding Trojan:Win32/Smokeloader!pz Virus
This ransomware targets the files on your computer, encrypts them, and then demands a ransom for a decryption key. In addition to locking your files, Troiano:Win32/Smokeloader!pz significantly damages your system’s functionality. It alters network settings to block access to removal guides and prevent the download of anti-malware solutions. A volte, it may even stop anti-malware programs from launching.
Key Features
The following are some of the primary actions of the Trojan:Win32/Smokeloader!pz malware on an infected computer:
- Behavioral detection: Executable code extraction – unpacking.
- Unconventional language in binary resources: Punjabi.
- Authenticode signature is invalid.
- Behavioral detection: Code injection techniques like Process Hollowing and Inter-process.
- Encrypts files, rendendoli inaccessibili.
- Blocks execution of anti-malware software.
- Prevents the installation of antivirus programs.
Ransomware remains a significant threat, representing one of the most severe types of viruses affecting individuals and businesses alike. The encryption algorithms used (typically RHA-1028 or AES-256) are robust, with decryption through brute force nearly impossible. Despite the power of this malware, it does not execute its actions instantly; it may take several hours to encrypt all your files. Così, detecting Trojan:Win32/Smokeloader!pz should be a clear signal to begin the removal process immediately.
Troiano:Win32/Smokeloader!pz Spreads
Il Trojan:Win32/Smokeloader!pz spreads via typical methods shared with other malware types. These include deceptive websites offering free software downloads, phishing emails pretending to be legitimate notifications, and malicious tools. Phishing emails, a newer strategy, may appear as ordinary updates about shipments or bank services but contain harmful attachments or links leading to malicious websites.
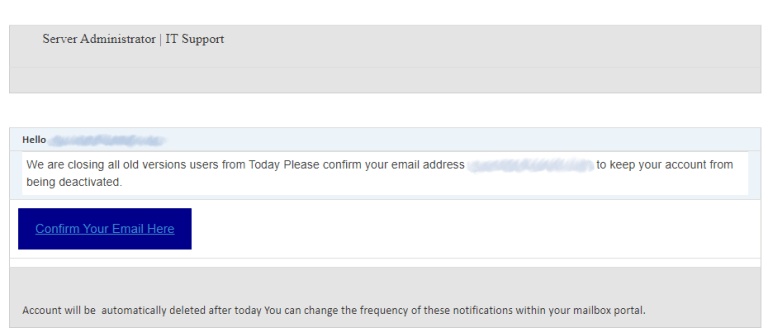
Malicious email message. This one tricks you into opening the phishing website.
Avoiding it looks quite uncomplicated, Tuttavia, still demands a lot of attention. Malware can hide in different places, and it is better to stop it even before it goes into your computer than to trust in an anti-malware program. Simple cybersecurity knowledge is just an important item in the modern world, even if your relationship with a computer remains on YouTube videos. That can keep you a lot of time and money which you would certainly spend while searching for a fix guide.
Technical Details
| Bkav | W32.AIDetectMalware |
| Lionic | Trojan.Win32.SmokeLoader.4!C |
| tehtris | Generic.Malware |
| MicroWorld-eScan | Trojan.GenericKD.70612133 |
| Fireeye | Generic.mg.284ec46a8277bda8 |
| CAT-QuickHeal | Ransom.Stop.P5 |
| Skyhigh | BehavesLike.Win32.Lockbit.dm |
| ALYac | Trojan.GenericKD.70612133 |
| Cylance | unsafe |
| Sangfor | Trojan.Win32.Save.a |
| K7AntiVirus | Troiano ( 005aafe61 ) |
| Alibaba | Troiano:Win32/SmokeLoader.cfaee45c |
| K7GW | Troiano ( 005aafe61 ) |
| Cybereason | malicious.78f4e3 |
| Arcabit | Trojan.Generic.D43574A5 |
| Symantec | Ml.attribute.highconfidence |
| Elastic | malicious (high confidence) |
| ESET-NOD32 | a variant of Win32/Kryptik.HVKJ |
| Cynet | Dannoso (score: 100) |
| APEX | Dannoso |
| ClamAV | Win.Packer.pkr_ce1a-9980177-0 |
| Kaspersky | Heur:Trojan.Win32.Chapak.gen |
| BitDefender | Trojan.GenericKD.70612133 |
| Avast | Win32:PWSX-gen [Trj] |
| Tencent | Trojan.Win32.Obfuscated.gen |
| Sophos | Troj/Krypt-VK |
| F-Secure | Trojan.TR/Crypt.Agent.kakul |
| DrWeb | Trojan.PWS.Stealer.34727 |
| VIPRE | Trojan.GenericKD.70612133 |
| TrendMicro | Trojan.Win32.SMOKELOADER.YXDK3Z |
| Trapmine | malicious.high.ml.score |
| Emsisoft | Trojan.GenericKD.70612133 (B) |
| SentinelOne | Static AI – Malicious PE |
| Jiangmin | Trojan.Chapak.rrw |
| Varist | W32/Kryptik.LDY.gen!Eldorado |
| Avira | TR/Crypt.Agent.kakul |
| Antiy-AVL | Trojan/Win32.Caynamer |
| Kingsoft | Win32.Troj.Agent.cks |
| Microsoft | Troiano:Win32/Smokeloader!Pz |
| ZoneAlarm | Heur:Trojan.Win32.Chapak.gen |
| GData | Trojan.GenericKD.70612133 |
| Detected | |
| AhnLab-V3 | Malware/Win.RansomX-gen.R625969 |
| McAfee | Artemide!284EC46A8277 |
| MAX | malware (ai score=85) |
| VBA32 | BScope.Trojan.Yakes |
| Malwarebytes | Trojan.MalPack.GS |
| Panda | Trj/Genetic.gen |
| TrendMicro-HouseCall | Trojan.Win32.SMOKELOADER.YXDK3Z |
| Rising | Trojan.SmokeLoader!1.EB63 (CLASSIC) |
| Ikarus | Trojan.Win32.Azorult |
| MaxSecure | Trojan.Malware.73643692.susgen |
| Fortinet | W32/GenKryptik.ERHN!tr |
| Avg | IDP.Generic |
| DeepInstinct | MALICIOUS |
| CrowdStrike | win/malicious_confidence_100% (W) |
How to remove?
Troiano:Win32/Smokeloader!pz malware is very hard to eliminate manually. It stores its data in several places throughout the disk and can get back itself from one of the parts. Inoltre, Varie modifiche nel registro di Windows, networking configurations, and also Group Policies are pretty hard to discover and return to the initial. It is better to use a specific app – esattamente, an anti-malware tool. Gridinsoft Anti-Malware will fit the best for malware elimination goals.
Rimuovi Trojan:Win32/Smokeloader!pz with Gridinsoft Anti-Malware
Da allora utilizziamo questo software anche sui nostri sistemi, ed è sempre riuscito a rilevare i virus. Ha bloccato i trojan più comuni come mostrato dai nostri test con il software, E ti assicuriamo che può rimuovere Trojan:Win32/Smokeloader!pz as well as other malware hiding on your computer.
Utilizzare Gridinsoft per rimuovere minacce dannose, seguire i passaggi seguenti:
1. Inizia scaricando Gridinsoft Anti-Malware, accessibile tramite il pulsante blu qui sotto o direttamente dal sito ufficiale gridinsoft.com.
2.Una volta che il file di installazione di Gridinsoft (setup-gridinsoft-fix.exe) viene scaricato, eseguirlo facendo clic sul file. Follow the installation setup wizard's instructions diligently.
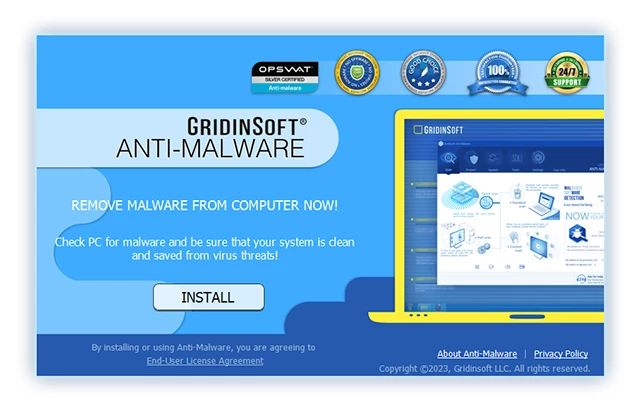
3. Accedi al "Scheda Scansione" on the application's start screen and launch a comprehensive "Scansione completa" per esaminare l'intero computer. Questa scansione inclusiva abbraccia la memoria, elementi di avvio, il registro, servizi, conducenti, e tutti i file, garantendo che rilevi malware nascosto in tutte le posizioni possibili.
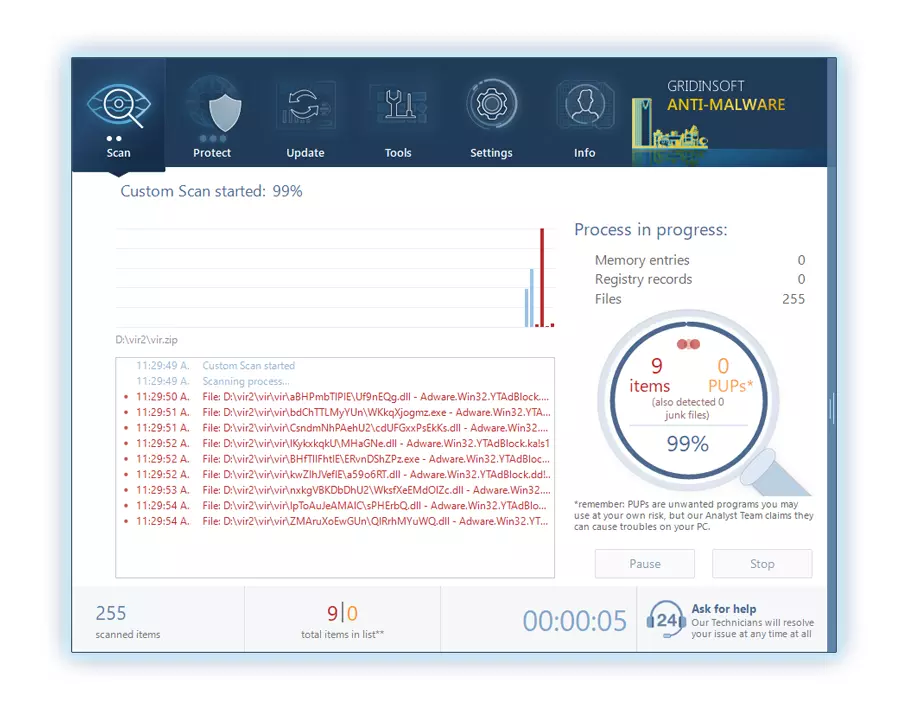
Essere pazientare, as the scan duration depends on the number of files and your computer's hardware capabilities. Usa questo tempo per rilassarti o dedicarti ad altre attività.
4. Al termine, Anti-Malware presenterà un rapporto dettagliato contenente tutti gli elementi dannosi e le minacce rilevati sul tuo PC.
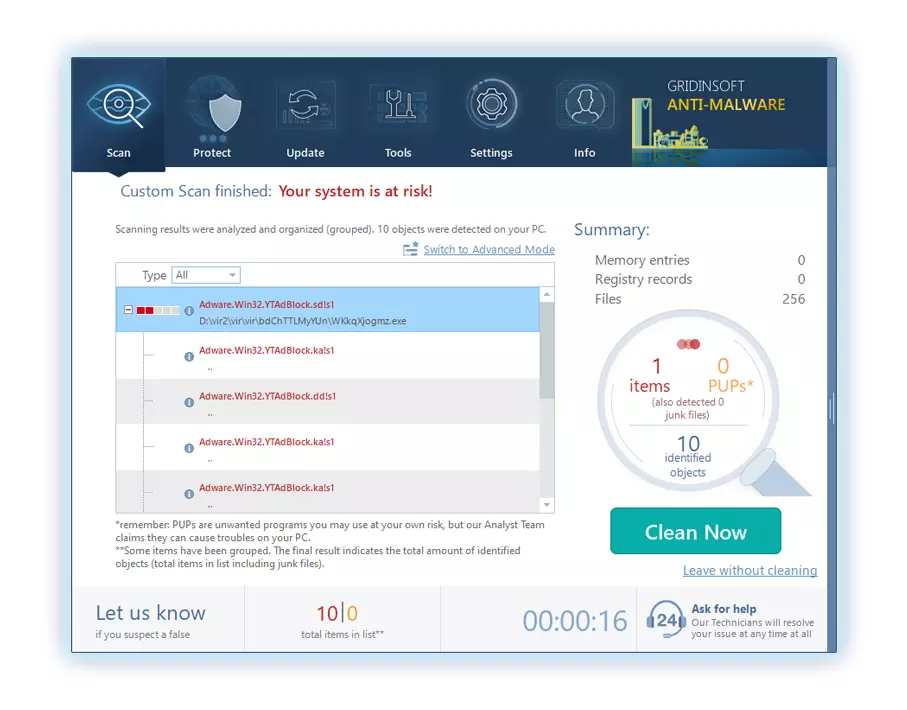
5. Seleziona tutti gli elementi identificati dal rapporto e fai clic con sicurezza su "Pulisci adesso" pulsante. Questa azione rimuoverà in modo sicuro i file dannosi dal tuo computer, trasferendoli nella zona di quarantena sicura del programma anti-malware per prevenire ulteriori azioni dannose.
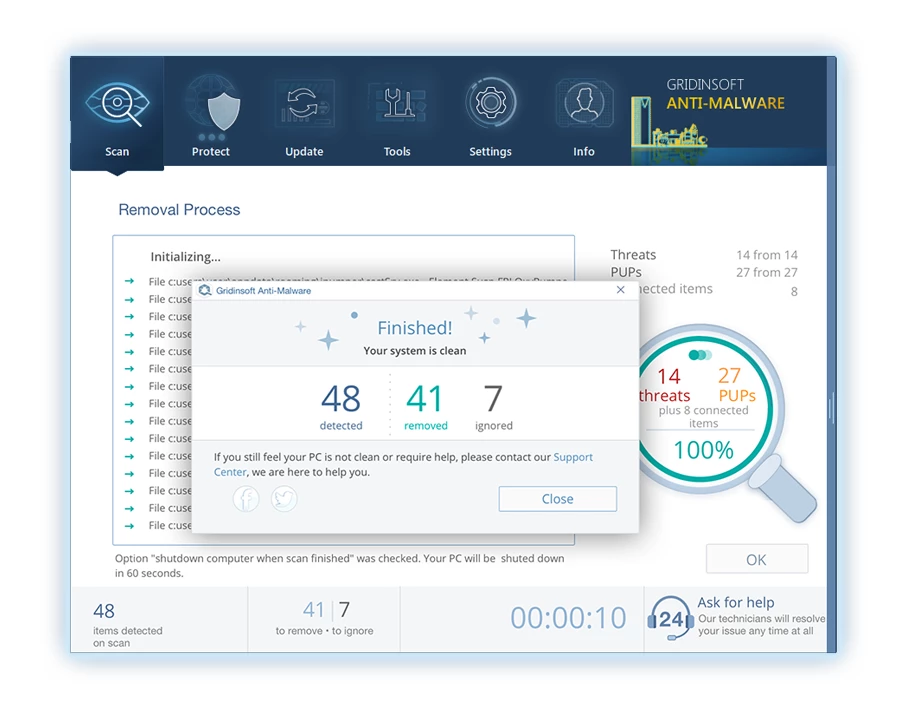
6. Se richiesto, riavviare il computer per finalizzare la procedura di scansione completa del sistema. Questo passaggio è fondamentale per garantire la rimozione completa di eventuali minacce rimanenti. Dopo il riavvio, Gridinsoft Anti-Malware si aprirà e visualizzerà un messaggio di conferma completamento della scansione.
Ricorda che Gridinsoft offre una prova gratuita di 6 giorni. Ciò significa che puoi sfruttare gratuitamente il periodo di prova per sperimentare tutti i vantaggi del software e prevenire eventuali future infezioni da malware sul tuo sistema. Embrace this opportunity to fortify your computer's security without any financial commitment.







Lascia un commento