Trojan Wacatac is identified by Microsoft Defender as encompassing a variety of threats that blend spyware capabilities with the ability to deliver malware. Recognized for its high risk, Wacatac demands cautious handling due to its dangerous nature.
Understanding Wacatac
Wacatac serves as a label for a broad spectrum of malicious software characterized by its spyware functionality and its role as a malware distributor or dropper. This dual functionality is prevalent in many modern malware instances, making Wacatac detections increasingly common.
Occasionally, what is detected might primarily be a dropper rather than spyware or a data stealer. Droppers typically gather system information to identify the targeted device, a behavior Microsoft Defender may interpret as data collection. While this data gathering is less comprehensive, it underscores the rationale behind the detection.
Threat Overview
| Nome | Troiano:Win32/Wacatac |
| Behavior | Data theft, Malware distribution |
| Malware Category | Spyware, Infostealer, Banking Trojan, Dropper |
| Transmission Methods | Malicious email attachments, unauthorized software from non-official sources |
| Variants | Troiano:Win32/Wacatac.B!ml, Troiano:Win32/Wacatac.H!ml, Troiano:Script/Wacatac.H!ml |
The Risks Posed by Trojan:Win32/Wacatac
The primary threats of Wacatac include its spyware capabilities — alarming for user privacy as it captures passwords, cookie files, and session tokens. Its role as a dropper exacerbates the risk by introducing additional malware, thus enhancing the attackers’ gain.
Certain Wacatac variants target specific areas such as cryptocurrency wallets or online banking, trading general theft for the potential of significant financial harm. Nonetheless, attackers can easily couple standard spyware with banking trojans, cryptostealers, or ransomware as a secondary payload.
Malware Families Detected as Trojan Wacatac
Wacatac is not confined to a single malware family but includes several types recognized by their shared characteristics. Microsoft Defender frequently identifies the following families under the Wacatac designation:
| Amadey Dropper | Currently among the most active malwares, used to distribute Vidar, RedLine stealers, and STOP/Djvu ransomware. Occasionally delivers cryptominers while collecting basic system information. |
| Gozi Stealer | Initially a data stealer, Gozi was later enhanced with malware distribution capabilities. It primarily functions as spyware. |
| Emotet (Epoch 4 variants) | A notorious malware known for combining dropper and stealer roles. While Defender typically categorizes it as Sabsik, changes in the Epoch 4 variant likely altered its signature to resemble Wacatac more closely. |
| QakBot | A long-standing malware primarily used in targeted attacks for reconnaissance and lateral movement. Its network was recently dismantled, potentially signaling an imminent resurgence. |
| FormBook | Also known as xLoader, active since 2016, it combines stealer and dropper functions but is less infamous than Emotet. |
Eliminating the Wacatac Trojan
Wacatac establishes deep roots upon infection, making manual removal challenging. This stealthy behavior is typical for malware seeking to avoid detection. As such, utilizing an anti-malware tool is advisable for thorough removal.
Gridinsoft Anti-Malware stands out as an effective solution, thanks to its constantly updated database and sophisticated heuristic detection capabilities, ensuring the identification and elimination of the latest malware threats.
Remove Wacatac Trojan with Gridinsoft Anti-Malware
Da allora utilizziamo questo software anche sui nostri sistemi, ed è sempre riuscito a rilevare i virus. Ha bloccato i trojan più comuni come mostrato dai nostri test con il software, and we assure you that it can remove Wacatac Trojan as well as other malware hiding on your computer.
Utilizzare Gridinsoft per rimuovere minacce dannose, seguire i passaggi seguenti:
1. Inizia scaricando Gridinsoft Anti-Malware, accessibile tramite il pulsante blu qui sotto o direttamente dal sito ufficiale gridinsoft.com.
2.Una volta che il file di installazione di Gridinsoft (setup-gridinsoft-fix.exe) viene scaricato, eseguirlo facendo clic sul file. Follow the installation setup wizard's instructions diligently.
3. Accedi al "Scheda Scansione" on the application's start screen and launch a comprehensive "Scansione completa" per esaminare l'intero computer. Questa scansione inclusiva abbraccia la memoria, elementi di avvio, il registro, servizi, conducenti, e tutti i file, garantendo che rilevi malware nascosto in tutte le posizioni possibili.
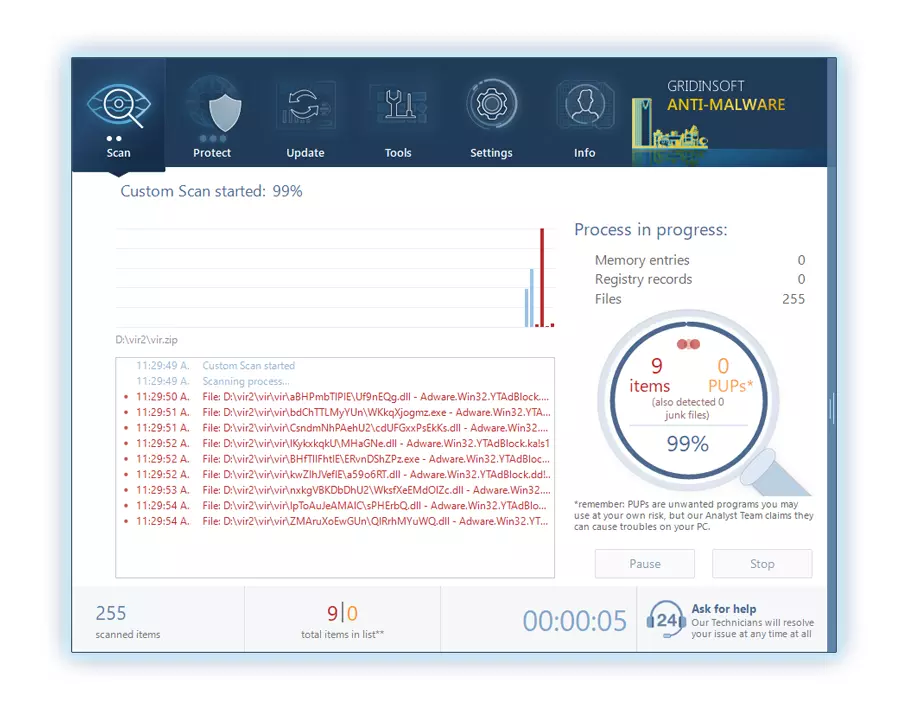
Essere pazientare, as the scan duration depends on the number of files and your computer's hardware capabilities. Usa questo tempo per rilassarti o dedicarti ad altre attività.
4. Al termine, Anti-Malware presenterà un rapporto dettagliato contenente tutti gli elementi dannosi e le minacce rilevati sul tuo PC.
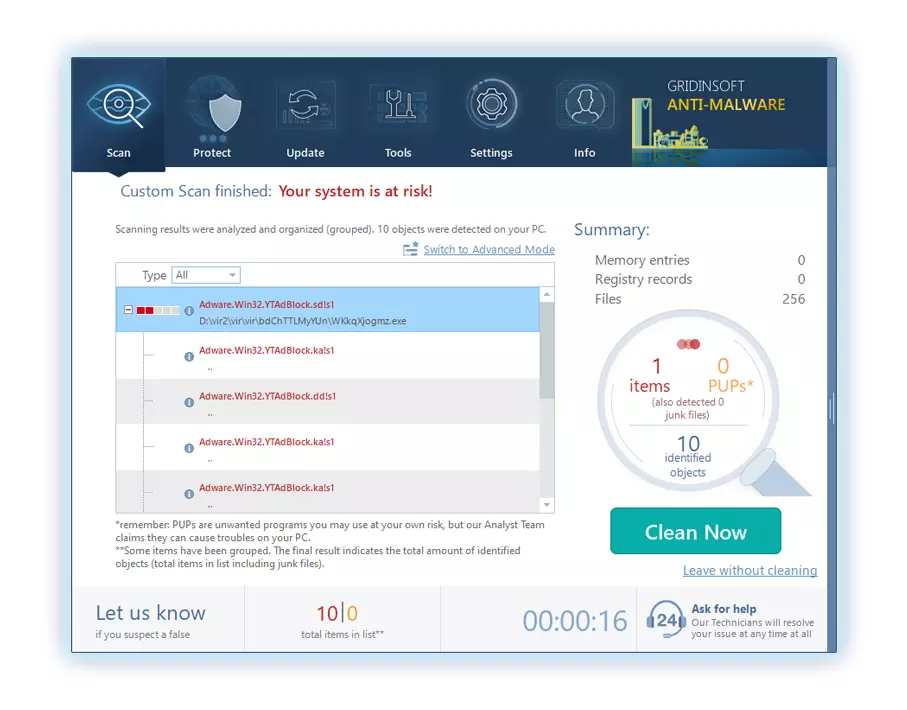
5. Seleziona tutti gli elementi identificati dal rapporto e fai clic con sicurezza su "Pulisci adesso" pulsante. Questa azione rimuoverà in modo sicuro i file dannosi dal tuo computer, trasferendoli nella zona di quarantena sicura del programma anti-malware per prevenire ulteriori azioni dannose.
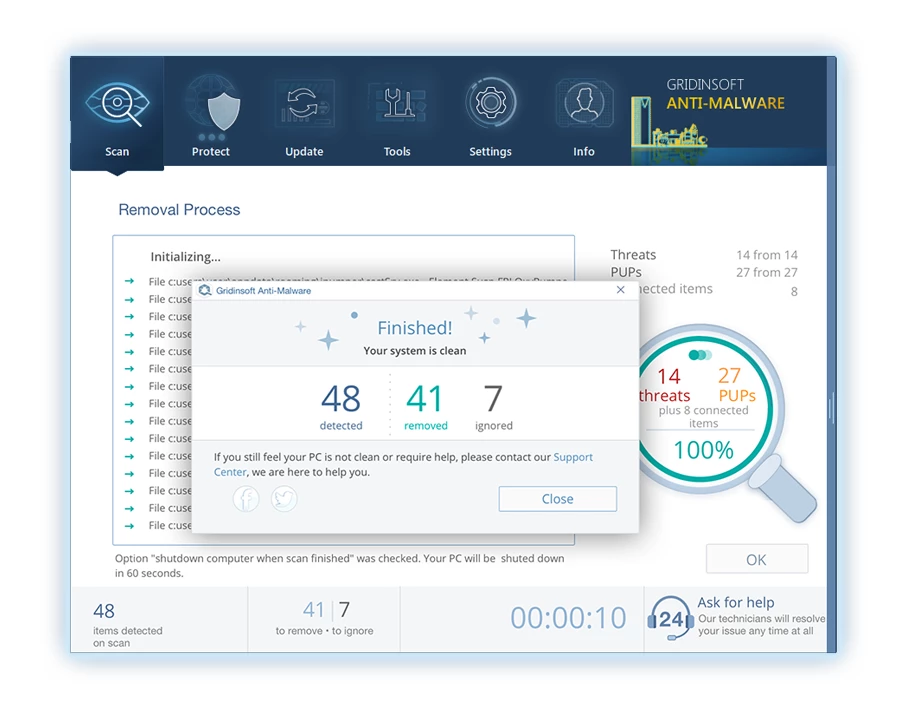
6. Se richiesto, riavviare il computer per finalizzare la procedura di scansione completa del sistema. Questo passaggio è fondamentale per garantire la rimozione completa di eventuali minacce rimanenti. Dopo il riavvio, Gridinsoft Anti-Malware si aprirà e visualizzerà un messaggio di conferma completamento della scansione.
Ricorda che Gridinsoft offre una prova gratuita di 6 giorni. Ciò significa che puoi sfruttare gratuitamente il periodo di prova per sperimentare tutti i vantaggi del software e prevenire eventuali future infezioni da malware sul tuo sistema. Embrace this opportunity to fortify your computer's security without any financial commitment.
Domande frequenti
🤔 What is Trojan Wacatac?
Wacatac, also known as Trojan:Win32/Wacatac, is malware that performs malicious activities covertly on infected computers.
🤔 How does Wacatac spread?
It spreads mainly through spam emails and counterfeit software ‘cracks’, tricking users into downloading infected attachments or installing pirated software, which leads to system compromise.
🤔 What harm can Wacatac cause?
Wacatac can significantly disrupt both the computer and the user’s digital life, stealing sensitive information like login credentials and financial data, risking privacy breaches and substantial financial loss.
Ho bisogno del tuo aiuto per condividere questo articolo.
It’s your turn to assist others. This article was crafted to aid individuals like you. Use the buttons below to share this on your preferred social media platforms like Facebook, Twitter, o Reddit.
Brendan Smith






Lascia un commento