IL Virus Shinra fa parte del Ransomware proton famiglia. Questo tipo di ransomware crittografa tutti i dati sul tuo PC, inclusi le foto, file di testo, fogli di calcolo, audio, e file video, e aggiunge un'estensione univoca a ciascun file. Lascia anche un #Shinra-recovery.txt File in ogni cartella che contiene file crittografati.
Qual è il virus Shinra?
Il virus Shinra è un tipo di ransomware protonico. Una volta infetto, I tuoi file verranno rinominati secondo lo schema: .Shinra3. Per esempio, un file chiamato “report.docx” cambierebbe in “report.docx.dq9mbvc09h.shinra3”.
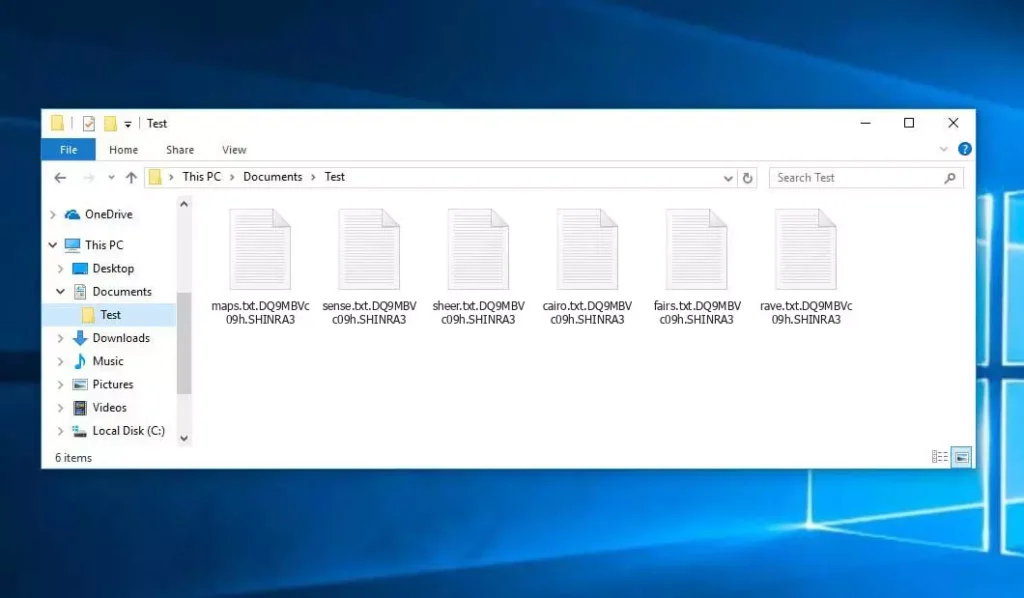
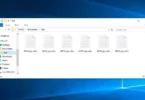
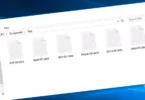
File crittografati da shinra ransomware (.Estensione Shinra3)
In ogni cartella con file crittografati, troverai un #Shinra-recovery.txt File di testo. Questo file è essenzialmente una nota di riscatto che fornisce istruzioni su come pagare il riscatto e ottenere uno strumento di decrittografia dagli sviluppatori di virus. Per ottenere questo strumento, devi contattare qq.decrypt@gmail.com O qq.encrypt@gmail.com.
Riepilogo Shinra:
| Nome | Virus Shinra |
| Famiglia ransomware | Protone ransomware |
| Estensione | .Shinra3 |
| Nota sul ransomware | #Shinra-recovery.txt |
| Contatto | qq.decrypt@gmail.com, qq.encrypt@gmail.com |
| Rilevamento | Riscatto:Win64/akira.ccdr!Mtb, Ransom.shinra, Win64:Ransomx-Gen [Riscatto], Ml.attribute.highconfidence |
| Sintomi | I tuoi file (foto, video, documenti) avere un .Estensione Shinra3 E non puoi aprirli. |
| Strumento di correzione | Vedi se il tuo sistema è stato influenzato dal virus Shinra |
IL #Documento Shinra-Recovery.txt accompagnare il Malware Shinra Fornisce le seguenti informazioni scoraggianti:
~~~ SHINRA ~~~ >>> What happened? Abbiamo crittografato e rubato tutti i tuoi file. Usiamo gli algoritmi AES e ECC. Nessuno può recuperare i tuoi file senza il nostro servizio di decryption. >>> What guarantees? Puoi inviarci un file non importante in meno di 1 Mg, Lo decrittiamo come garanzia. Se non ti inviamo il software di decryption o eliminiamo i dati rubati, Nessuno ci pagherà in futuro, quindi manterremo la nostra promessa. >>> How to contact us? Il nostro indirizzo email: qq.decrypt@gmail.com In caso di nessuna risposta all'interno 24 ore, Contattare questa email: qq.encrypt@gmail.com Scrivi il tuo ID personale nell'oggetto dell'email. >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>> >>>>>>>>> Your ID: - <<<<<<<<<< >>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>> >>> Warnings! - Non andare alle società di recupero, Sono solo intermediari che ti faranno soldi e ti imbrogliano. Negoziano segretamente con noi, Acquista software di decryption, e te lo venderà molte volte più costoso o ti farà semplicemente truffere. - Non esitare a lungo. Più velocemente paghi, Più basso è il prezzo. - Non eliminare o modificare i file crittografati, porterà a problemi con la decrittografia dei file.
Nello screenshot qui sotto, Puoi vedere come appare una directory con file crittografati da Shinra. Ogni nome file ha il “.Shinra3” Estensione aggiunta ad esso.
Come è finito Shinra Ransomware sul mio PC?
Esistono molti modi possibili di iniezione di ransomware.
Attualmente ci sono tre modi più popolari per i malvagi che si stabiliscono ransomware nel tuo ambiente digitale. Questi sono spam e -mail, Infiltrazione di Troia, e reti peer.
- Se accedi alla tua casella di posta e vedi lettere che assomigliano a notifiche dei fornitori di servizi di utilità, agenzie postali come FedEx, Provider di accesso al web, e quant'altro, Ma il cui indifferente è strano per te, Fai attenzione all'apertura di quelle e -mail. È molto probabile che abbiano un file dannoso racchiuso in essi. Quindi è ancora più rischioso scaricare eventuali allegati forniti con e -mail come queste.
- Un'altra opzione per Ransom Hunters è un modello di virus Trojan. Un Trojan è un oggetto che entra nella macchina fingendo di essere qualcosa di legale. Per esempio, scarichi un installatore di alcuni programmi che desideri o un aggiornamento per alcuni software. Ma ciò che è unboxed risulta essere un agente dannoso che crittografa i tuoi dati. Poiché il pacchetto di aggiornamento può avere qualsiasi titolo e qualsiasi icona, Devi assicurarti di poter fidarti delle risorse delle cose che stai scaricando. Il modo ottimale è fidarsi degli sviluppatori di software’ siti Web ufficiali.
- Per quanto riguarda i protocolli di trasferimento di file peer come i tracker torrent, Il pericolo è che sono ancora più basati sulla fiducia rispetto al resto del web. Non puoi mai sapere cosa scarichi finché non lo ottieni. Quindi è meglio utilizzare siti Web affidabili. Anche, È ragionevole scansionare la cartella contenente i file scaricati con l'utilità anti-Malware non appena il download è completo.
Come mi sbarazzo del ransomware?
È fondamentale notare che oltre a crittografare i file, molto probabilmente il virus Shinra si installerà Vidar ruba Sulla tua macchina per accedere alle credenziali su account diversi (compresi i portafogli di criptovaluta). Quel programma può derivare i tuoi accessi e password dal file di schede automatico del browser.
Rimuovi Shinra con Gridinsoft Anti-Malware
Da allora utilizziamo questo software anche sui nostri sistemi, ed è sempre riuscito a rilevare i virus. Ha bloccato il ransomware più comune come mostrato dai nostri test con il software, E ti assicuriamo che può rimuovere Shinra e altri malware che si nascondono sul tuo computer.
Utilizzare Gridinsoft per rimuovere minacce dannose, seguire i passaggi seguenti:
1. Inizia scaricando Gridinsoft Anti-Malware, accessibile tramite il pulsante blu qui sotto o direttamente dal sito ufficiale gridinsoft.com.
2.Una volta che il file di installazione di Gridinsoft (setup-gridinsoft-fix.exe) viene scaricato, eseguirlo facendo clic sul file. Follow the installation setup wizard's instructions diligently.
3. Accedi al "Scheda Scansione" on the application's start screen and launch a comprehensive "Scansione completa" per esaminare l'intero computer. Questa scansione inclusiva abbraccia la memoria, elementi di avvio, il registro, servizi, conducenti, e tutti i file, garantendo che rilevi malware nascosto in tutte le posizioni possibili.
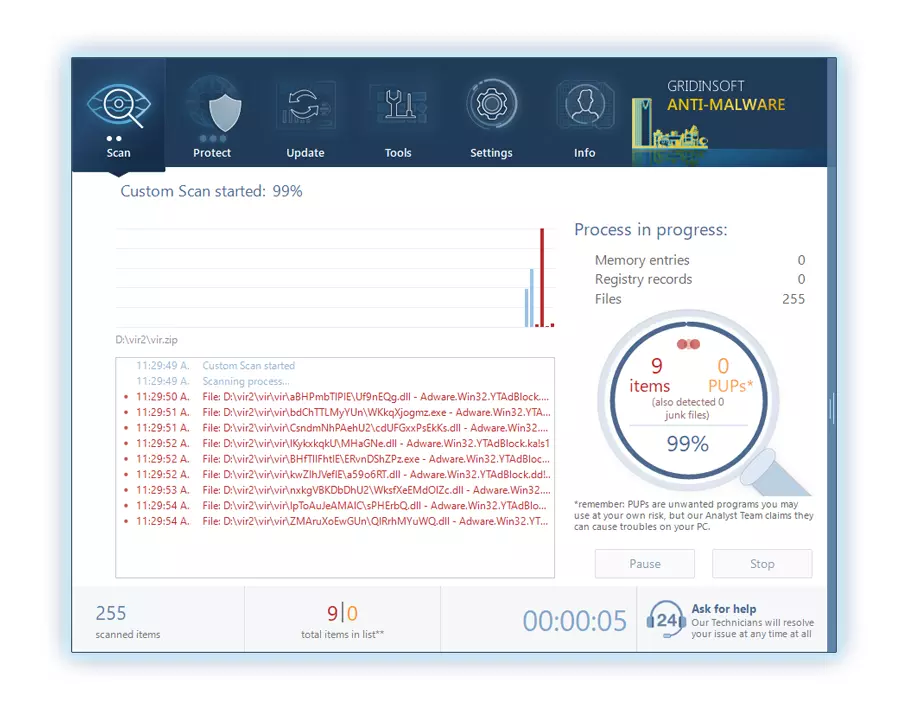
Essere pazientare, as the scan duration depends on the number of files and your computer's hardware capabilities. Usa questo tempo per rilassarti o dedicarti ad altre attività.
4. Al termine, Anti-Malware presenterà un rapporto dettagliato contenente tutti gli elementi dannosi e le minacce rilevati sul tuo PC.
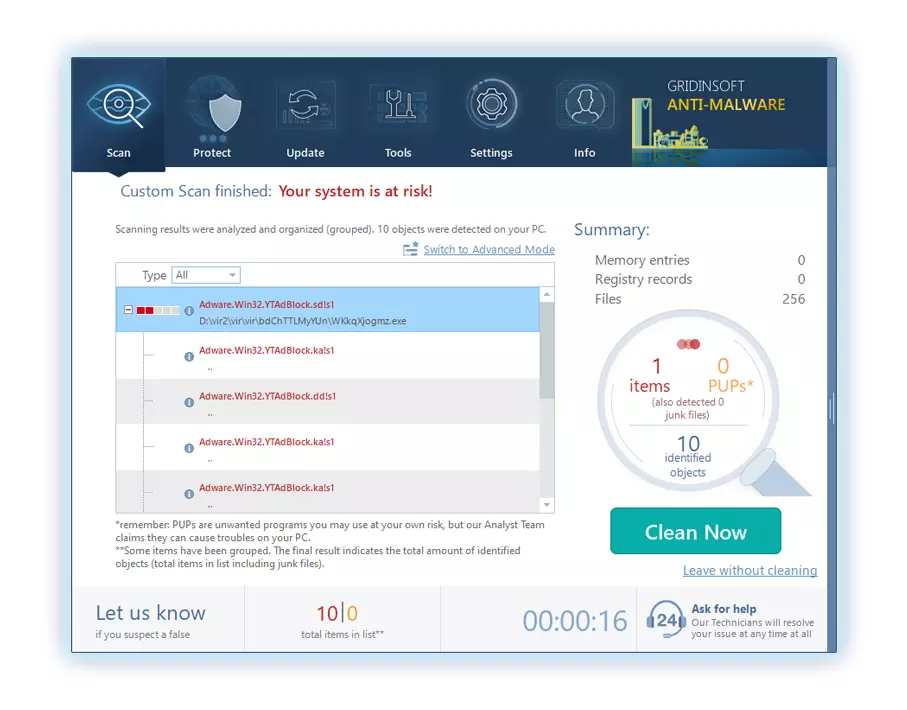
5. Seleziona tutti gli elementi identificati dal rapporto e fai clic con sicurezza su "Pulisci adesso" pulsante. Questa azione rimuoverà in modo sicuro i file dannosi dal tuo computer, trasferendoli nella zona di quarantena sicura del programma anti-malware per prevenire ulteriori azioni dannose.
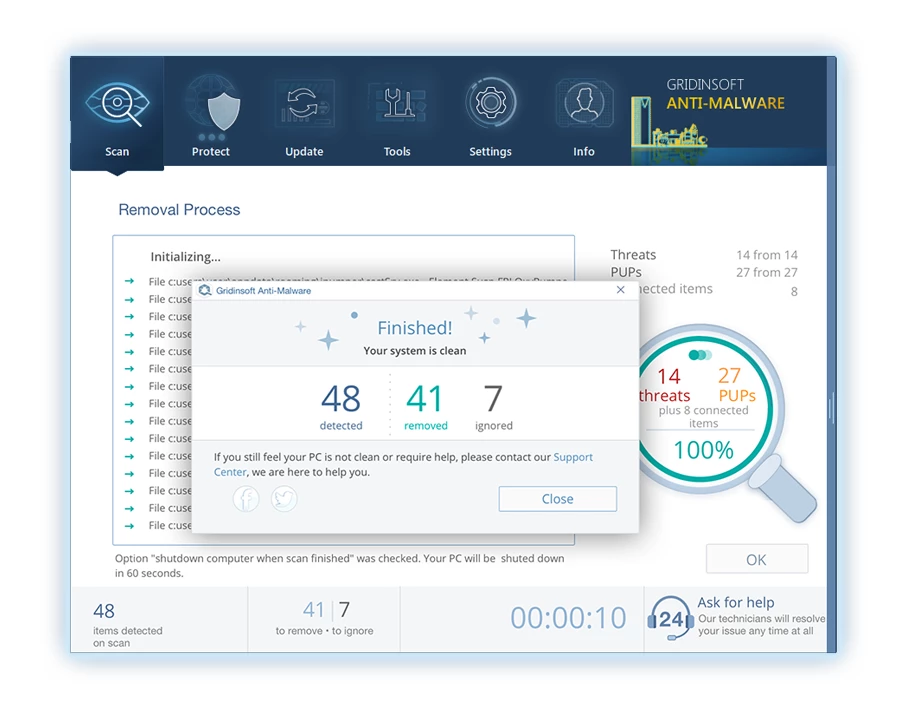
6. Se richiesto, riavviare il computer per finalizzare la procedura di scansione completa del sistema. Questo passaggio è fondamentale per garantire la rimozione completa di eventuali minacce rimanenti. Dopo il riavvio, Gridinsoft Anti-Malware si aprirà e visualizzerà un messaggio di conferma completamento della scansione.
Ricorda che Gridinsoft offre una prova gratuita di 6 giorni. Ciò significa che puoi sfruttare gratuitamente il periodo di prova per sperimentare tutti i vantaggi del software e prevenire eventuali future infezioni da malware sul tuo sistema. Embrace this opportunity to fortify your computer's security without any financial commitment.
Spesso i racketeer decodifichevano molti dei tuoi file per dimostrare che hanno effettivamente lo strumento di decryption. Poiché il virus Shinra è un ransomware relativamente recente, Le misure di sicurezza gli sviluppatori non hanno ancora trovato il modo di annullare il suo lavoro. Tuttavia, Gli strumenti di decrittografia sono spesso aggiornati, Quindi potrebbe presto arrivare una contromisura efficace.
Comprensibilmente, Se i criminali riescono a codificare i file essenziali di qualcuno, La persona senza speranza probabilmente rispetterà le loro richieste. Tuttavia, Pagare un riscatto non dà alcuna garanzia che stai recuperando i tuoi file. È ancora rischioso. Dopo aver ricevuto il riscatto, I racketeer possono fornire il codice di decrittografia errata alla vittima. Ci sono stati notizie sui criminali che sono appena scomparsi dopo aver ottenuto il riscatto senza nemmeno scrivere.
La migliore contromisura per il ransomware è avere un punto di ripristino del sistema o le copie dei file essenziali nell'archiviazione cloud o almeno in memoria esterna. Ovviamente, Potrebbe non essere abbastanza. La cosa più importante potrebbe essere quella su cui stavi lavorando quando tutto è iniziato. Ma almeno è qualcosa. È anche ragionevole scansionare il tuo PC per i virus con il programma antivirus dopo il ripristino del sistema operativo.
Ci sono altri prodotti ransomware, Oltre a Shinra, quel lavoro in modo simile. Esempi di questi sono BGJS, E Ransomware BGZQ. Le due differenze di base tra loro e lo shinra sono la quantità di riscatto e il metodo di crittografia. Il resto è quasi identico: i file vengono bloccati, Le loro estensioni hanno modificato, e le note di riscatto sono create in ogni cartella contenente file crittografati.
Alcuni utenti fortunati sono stati in grado di decrittografare i file bloccati con l'aiuto del software libero fornito dagli esperti anti-ransomware. A volte i racketeers inviano accidentalmente la chiave di decodifica ai torti nella nota di riscatto. Tale Epic Fail consente alla parte ferita di ripristinare i file. Ma naturalmente, non si dovrebbe mai fare affidamento su tale possibilità. Ricordare, Ransomware è uno strumento criminale per estrarre i soldi dalle loro vittime.
Come evitare l'infiltrazione di ransomware?
Shinra Ransomware non ha una superpotenza, Né nessun malware simile.
Puoi proteggere il tuo computer dalla sua iniezione in diversi semplici passaggi:
- Ignora qualsiasi lettere da mittenti sconosciuti con strani indirizzi, o con contenuti che non hanno nulla a che fare con qualcosa che ti aspetti (Puoi vincere in un pareggio per il premio in denaro senza nemmeno prenderne parte?). Nel caso in cui l'argomento e -mail sia più o meno qualcosa che ti aspetti, esaminare con cura tutti gli elementi della dubbia lettera. Una lettera di bufala conterrà sempre un errore.
- Non utilizzare programmi screpolati o non attendibili. I trojan sono spesso diffusi come parte di prodotti crollati, forse sotto il pretesto di "patch" che impedisce il controllo della licenza. Ma i programmi potenzialmente pericolosi sono molto difficili da dire da quelli affidabili, Perché i trojan a volte hanno la funzionalità di cui hai bisogno. Prova a cercare informazioni su questo prodotto software sui forum anti-malware, Ma la soluzione migliore non è affatto utilizzare tali programmi.
- E infine, Per essere sicuri della sicurezza degli oggetti che hai scaricato, Controllali con Gridinsoft Anti-Malware. Questo programma sarà una potente difesa per il tuo sistema.
Domande frequenti
🤔 sono il “.Shinra3” file accessibili?
Purtroppo, NO. Devi decifrare il “.Shinra3” file prima. Allora sarai in grado di aprirli.
🤔 Cosa dovrei fare per rendere i miei file accessibili il più velocemente possibile?
Va bene se hai salvato le copie da miopiate di questi importanti file altrove. Se non, C'è ancora una funzione di ripristino del sistema ma ha bisogno di un punto di ripristino per essere precedentemente salvato. Tutte le altre soluzioni richiedono tempo.
🤔 Se Gridinsoft elimina il malware Shinra, eliminerà anche i miei file crittografati?
Non c'è modo! I tuoi file crittografati non sono una minaccia per il tuo PC.
Gridinsoft Anti-Malware si occupa solo di virus attivi. Il ransomware che si è infiltrato nel PC deve essere ancora attivo e scansiona periodicamente il sistema per arrestare qualsiasi nuovo file che potresti creare sul tuo PC dopo l'attacco iniziale. Come è stato detto sopra, Il malware Shinra non viene da solo. Installa backdoors e keylogger che possono prendere le password del tuo account trasgredito e fornire malfattori un facile accesso al tuo sistema dopo un po 'di tempo.
🤔 Cosa fare se lo shinra ransomware ha bloccato il mio computer e non riesco a ottenere il codice di attivazione.
In una situazione così sfortunata, devi preparare un Memory stick con un killer Trojan precedentemente installato. Usa la modalità provvisoria per eseguire la pulizia. Vedi, Il ransomware viene eseguito automaticamente man mano che il sistema lancia e codifica per qualsiasi nuovo file creato o importato nel PC. Per bloccare questa funzione – Usa la modalità provvisoria, che consente solo ai programmi essenziali di eseguire automaticamente. Prendi in considerazione la lettura del nostro manuale su Windows di avvio in modalità provvisoria.
🤔 Cosa potrebbe aiutare la situazione in questo momento?
Alcuni dei dati crittografati possono essere trovati altrove.
- Se hai inviato o ricevuto i tuoi file importanti via e -mail, Potresti ancora scaricarli dalla tua casella di posta online.
- Potresti avere immagini o video condivisi con i tuoi amici o familiari. Chiedi loro di rimandarti quelle immagini.
- Se inizialmente hai ottenuto uno dei tuoi file da Internet, puoi provare a farlo di nuovo.
- I tuoi messaggeri, pagine dei social network, E le unità cloud potrebbero avere anche tutti quei file.
- Forse hai ancora i file necessari sul tuo vecchio PC, un laptop, cellulare, Memoria flash, ecc.



Lascia un commento