troyen:Win32 / wacatac.h!ml est un programme malveillant conçu pour voler vos données personnelles, passwords, and session tokens. En plus, Wacatac H ml can deploy a wide variety of other malware. The name “Wacatac” identifies a group of malware strings that share two main capabilities: data stealing and malware delivery.
Wacatac.H!mlThe Wacatac.H!ml Trojan poses an exceptional threat as it can expose your privacy and infect your system with various other malware. Among its favorites are ransomware and other stealers. The latter will grab various other data from your system, while the former will cipher your files and demand payment for their decryption. Ainsi, Wacatac Trojan’s activity exponentially increases the danger.
Le Troie:Win32 / wacatac.h!ml variant may have its distinctive characteristics, but in general, Trojans like this can serve various malicious purposes, y compris:
- Stealing sensitive information, such as passwords, credit card numbers, or other personal data
- Installing additional malware onto your computer (like a Malagent Trojan)
- Gaining control over your computer and using it to launch attacks on other systems
- Causing damage to or disabling your computer system or files
If your computer becomes infected with Trojan:Win32 / wacatac.h!ml, take immediate action to remove it to prevent further damage or data loss. You can use Microsoft Defender or any reputable anti-malware software to scan your system and eliminate the Trojan.
Qu'est-ce qu'un cheval de Troie:Win32 / wacatac.h!ml?
Le Troie:Win32 / wacatac.h!ml detection you can see in the lower right side is shown to you by Microsoft Defender. That anti-malware application is good at scanning. Cependant, prone to be unstable. It is prone to malware invasions and has a glitchy user interface and bugged malware removal features. Ainsi, the pop-up that says concerning the Wacatac is just an alert that Defender has recognized it. You will likely need to use a separate anti-malware program to remove it.
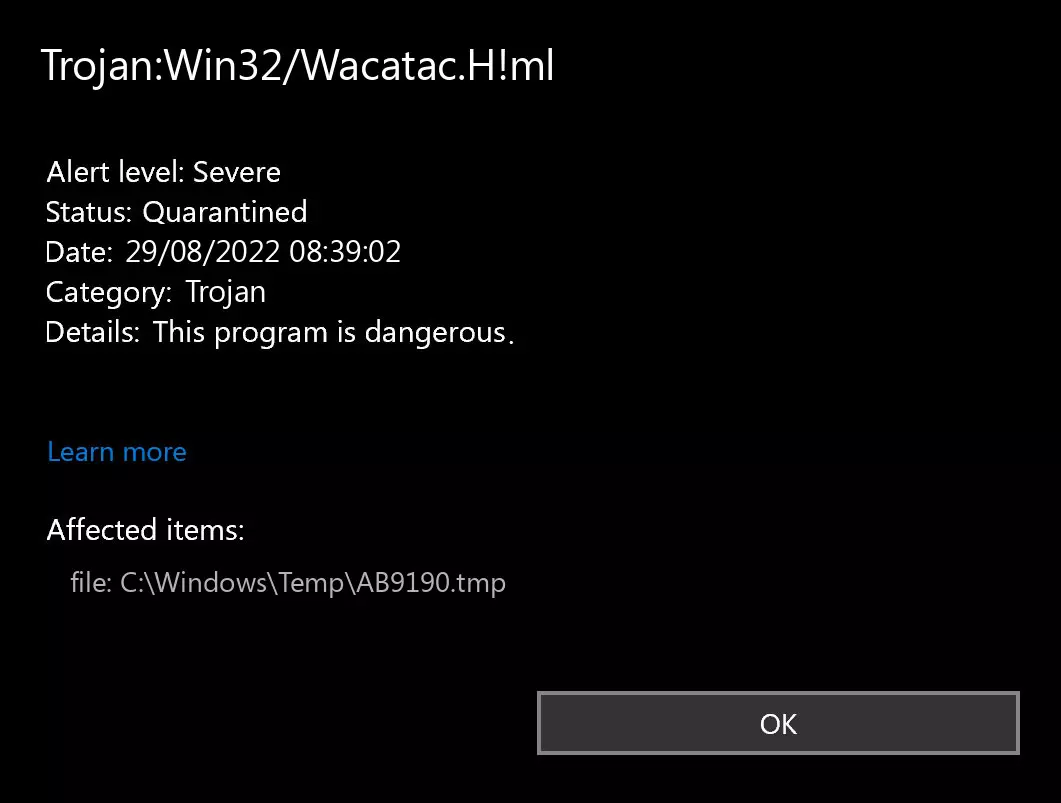
Microsoft Defender: troyen:Win32 / wacatac.h!ml
The exact Trojan:Win32 / wacatac.h!ml virus is a very undesirable thing. It digs inside of your system under the guise of something legitimate, or as a part of the program you downloaded from a forum. Then, it makes all possible steps to weaken your system. At the end of this “party”, it downloads other viruses – ones that are wanted by cybercriminals who control this malware. Hence, it is almost impossible to predict the effects of Wacatac.H!ml actions. And the unpredictability is one of the saddest things when talking about malware. That’s why it is better not to choose at all, and don’t give it even a single chance to complete its task.
| Nom | Wacatac.H!ml Trojan |
| Detection | troyen:Win32 / wacatac.h!ml |
| Details | Wacatac.H!ml tool that looks legitimate but can take control of your computer. |
Is It Dangerous?
Oui, troyen:Win32 / wacatac.h!ml is considered dangerous. It is a type of Trojan malware that can cause harm to your computer system. Trojans like Wacatac.H!ml are designed to carry out various malicious activities, such as stealing sensitive information, installing additional malware, taking control of your computer, or causing damage to your system or files. If your computer is infected with Trojan:Win32 / wacatac.h!ml, it is important to take immediate action to remove it and protect your computer from further damage.
troyen:Win32 / wacatac.h!ml malware modifies system settings and edits the Group Policies and Windows registry. These elements play a crucial role in proper system operation, even when we are not discussing system safety. Therefore, the virus contained in Wacatac.H!ml, or the one it will download later, will exploit you to maximize profits.
Personal information can be stolen by hackers and then sold on the Darknet. By utilizing adware and browser hijacker functionality embedded in the Trojan:Win32 / wacatac.h!ml virus, they can generate revenue by displaying ads to you. Each ad view earns them a penny, and with 100 views per day, they can make $1. A total of 1000 victims who view 100 banners daily could result in $1000. It’s simple math, but the conclusions are disheartening. Being a pawn for criminals is an unwise choice.
To determine the infiltration of Trojan:Win32 / wacatac.h!ml into your PC, consider the following queries:
- Did you download a cracked version of a program or utilize a crack to activate paid software for free?
- Did you download an outdated version of any software or program from a suspicious-looking website?
- Have you received an email in the past few days that seemed authentic (such as a shipment invoice you don’t recall creating), but when you clicked on the email attachment, a script executed and promptly vanished?
- Did you download a movie or song using a torrent file to circumvent payment?
- Have you recently disabled your Windows Defender or antivirus software for a few days, only to subsequently scan your computer and discover this threat?
If you answered affirmatively to any of the aforementioned inquiries, you have identified the pathway through which Trojan:Win32 / wacatac.h!ml infiltrated your computer.
How to remove it from my PC?
Removing the Trojan:Win32 / wacatac.h!ml malware manually is an extremely challenging task. Its files are scattered across various locations on the disk and can regenerate from one of these components. En plus, identifying and reverting the numerous modifications made to the registry, networking configurations, and Group Policies can be quite arduous. It is advisable to employ a dedicated application, specifically an anti-malware app. In this case, GridinSoft Anti-Malware proves to be the most suitable choice for achieving the objective of virus elimination.
Why should you choose GridinSoft Anti-Malware? Firstly, it boasts a lightweight design and receives regular updates to its databases, at nearly hourly intervals. Secondly, it is free from any bugs or vulnerabilities found in Microsoft Defender. The combination of these factors renders GridinSoft Anti-Malware highly effective in eradicating malware of any kind.
Retirer le Troie:Win32 / wacatac.h!ML avec Gridinsoft Anti-Malware
Nous utilisons également ce logiciel sur nos systèmes depuis, et il a toujours réussi à détecter les virus. It has blocked the most common Trojans as montré par nos tests avec le logiciel, Et nous vous assurons qu'il peut supprimer le Troie:Win32 / wacatac.h!ML ainsi que d'autres logiciels malveillants se cachant sur votre ordinateur.
Pour utiliser Gridinsoft pour supprimer les menaces malveillantes, suivez les étapes ci-dessous:
1. Commencez par télécharger Gridinsoft Anti-Malware, accessible via le bouton bleu ci-dessous ou directement depuis le site officiel grilleinsoft.com.
2.Une fois le fichier d'installation de Gridinsoft (setup-gridinsoft-fix.exe) est téléchargé, exécutez-le en cliquant sur le fichier. Follow the installation setup wizard's instructions diligently.
3. Accéder au "Onglet Numérisation" on the application's start screen and launch a comprehensive "Scan complet" pour examiner l'intégralité de votre ordinateur. Cette analyse inclusive englobe la mémoire, éléments de démarrage, le registre, prestations de service, Conducteurs, et tous les fichiers, s'assurer qu'il détecte les logiciels malveillants cachés dans tous les emplacements possibles.
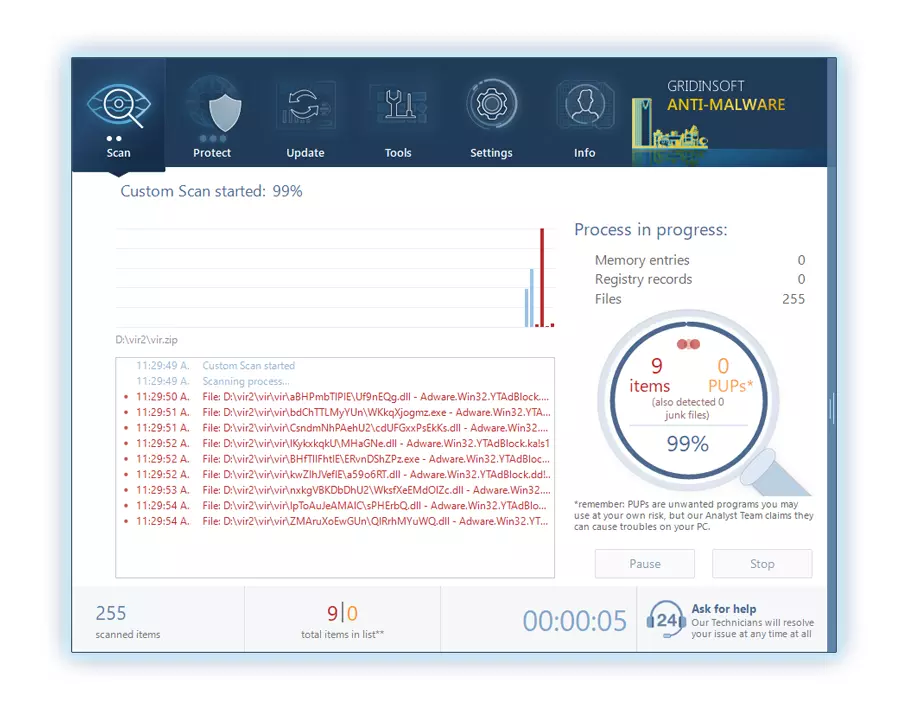
Sois patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Profitez de ce temps pour vous détendre ou vous occuper d'autres tâches.
4. Une fois terminé, Anti-Malware présentera un rapport détaillé contenant tous les éléments malveillants et menaces détectés sur votre PC.
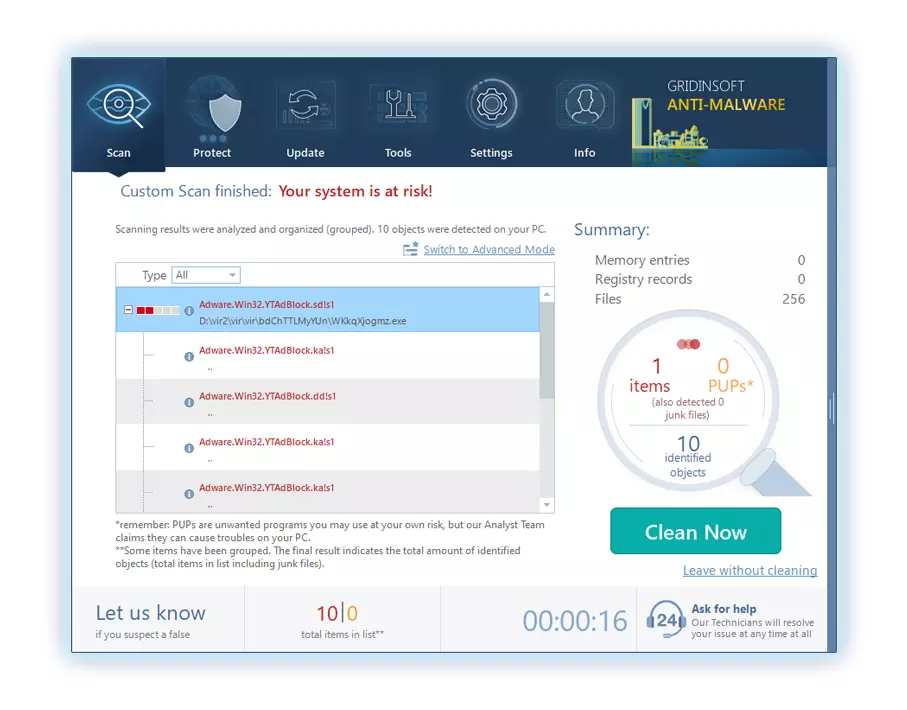
5. Sélectionnez tous les éléments identifiés dans le rapport et cliquez en toute confiance sur le "Nettoie maintenant" bouton. Cette action supprimera en toute sécurité les fichiers malveillants de votre ordinateur, les transférer vers la zone de quarantaine sécurisée du programme anti-malware pour éviter toute autre action nuisible.
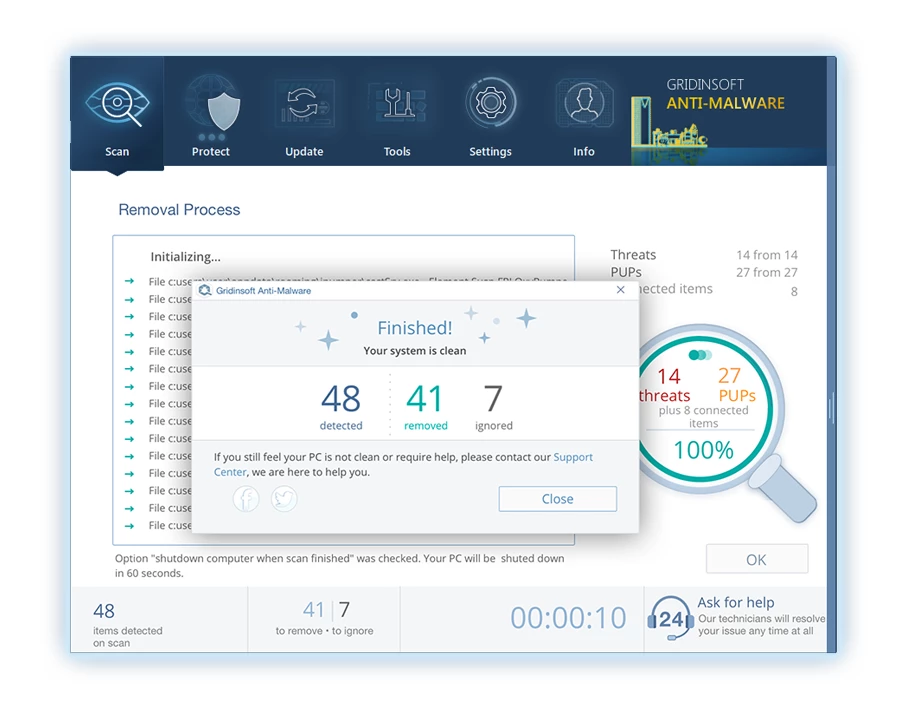
6. Si vous y êtes invité, redémarrez votre ordinateur pour finaliser la procédure d'analyse complète du système. Cette étape est cruciale pour garantir la suppression complète de toutes les menaces restantes.. Après le redémarrage, Gridinsoft Anti-Malware s'ouvrira et affichera un message confirmant le fin de l'analyse.
N'oubliez pas que Gridinsoft propose un essai gratuit de 6 jours. Cela signifie que vous pouvez profiter gratuitement de la période d'essai pour profiter de tous les avantages du logiciel et prévenir toute future infection par des logiciels malveillants sur votre système.. Embrace this opportunity to fortify your computer's security without any financial commitment.







Laissez un commentaire