If your computer alerts you with the Trojan:Win32/SmokeLoader!pz detection name, it’s a critical sign of danger. This detection indicates ransomware, which encrypts your files and demands a ransom for their decryption. Immediate action and specific steps are necessary to remove this malware promptly.
Le Troie:Win32/SmokeLoader!pz virus is commonly detected after engaging in risky activities on your computer, such as opening suspicious emails, clicking on online ads, or downloading software from unreliable sources. Once detected, swift action is essential to prevent its harmful effects. Delaying can lead to severe damage, so it’s crucial to act quickly.
Understanding Trojan:Win32/SmokeLoader!pz Virus
This ransomware targets the files on your computer, encrypts them, and then demands a ransom for a decryption key. In addition to locking your files, troyen:Win32/SmokeLoader!pz significantly damages your system’s functionality. It alters network settings to block access to removal guides and prevent the download of anti-malware solutions. Sometimes, it may even stop anti-malware programs from launching.
Key Features
The following are some of the primary actions of the Trojan:Win32/SmokeLoader!pz malware on an infected computer:
- Behavioral detection: Executable code extraction – unpacking.
- Unconventional language in binary resources: Punjabi.
- Authenticode signature is invalid.
- Behavioral detection: Code injection techniques like Process Hollowing and Inter-process.
- Encrypts files, les rendre inaccessibles.
- Blocks execution of anti-malware software.
- Prevents the installation of antivirus programs.
Ransomware remains a significant threat, representing one of the most severe types of viruses affecting individuals and businesses alike. The encryption algorithms used (typically RHA-1028 or AES-256) are robust, with decryption through brute force nearly impossible. Despite the power of this malware, it does not execute its actions instantly; it may take several hours to encrypt all your files. Ainsi, detecting Trojan:Win32/SmokeLoader!pz should be a clear signal to begin the removal process immediately.
troyen:Win32/SmokeLoader!pz Spreads
Le Troie:Win32/SmokeLoader!pz spreads via typical methods shared with other malware types. These include deceptive websites offering free software downloads, phishing emails pretending to be legitimate notifications, and malicious tools. Phishing emails, a newer strategy, may appear as ordinary updates about shipments or bank services but contain harmful attachments or links leading to malicious websites.
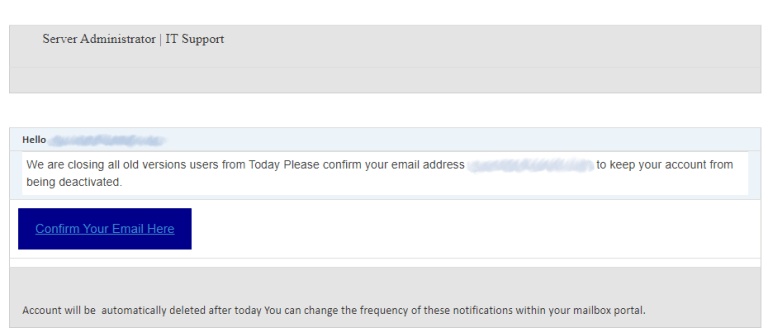
Malicious email message. This one tricks you into opening the phishing website.
Avoiding it looks quite uncomplicated, cependant, still demands a lot of attention. Malware can hide in different places, and it is better to stop it even before it goes into your computer than to trust in an anti-malware program. Simple cybersecurity knowledge is just an important item in the modern world, even if your relationship with a computer remains on YouTube videos. That can keep you a lot of time and money which you would certainly spend while searching for a fix guide.
Technical Details
| Bkav | W32.AIDetectMalware |
| Lionic | Trojan.Win32.SmokeLoader.4!c |
| tehtris | Generic.Malware |
| MicroWorld-eScan | Trojan.GenericKD.70612133 |
| FireEye | Generic.mg.284ec46a8277bda8 |
| CAT-QuickHeal | Ransom.Stop.P5 |
| Skyhigh | BehavesLike.Win32.Lockbit.dm |
| ALYac | Trojan.GenericKD.70612133 |
| Cylance | unsafe |
| Sangfor | Trojan.Win32.Save.a |
| K7AntiVirus | troyen ( 005aafe61 ) |
| Alibaba | troyen:Win32/SmokeLoader.cfaee45c |
| K7GW | troyen ( 005aafe61 ) |
| Cybereason | malicious.78f4e3 |
| Arcabit | Trojan.Generic.D43574A5 |
| Symantec | ML.Attribute.HighConfidence |
| Elastic | malicious (high confidence) |
| ESET-NOD32 | a variant of Win32/Kryptik.HVKJ |
| Cynet | Malveillant (score: 100) |
| APEX | Malveillant |
| ClamAV | Win.Packer.pkr_ce1a-9980177-0 |
| Kaspersky | HEUR:Trojan.Win32.Chapak.gen |
| BitDefender | Trojan.GenericKD.70612133 |
| Avast | Win32:PWSX-gen [Trj] |
| Tencent | Trojan.Win32.Obfuscated.gen |
| Sophos | Troj/Krypt-VK |
| F-Secure | Trojan.TR/Crypt.Agent.kakul |
| DrWeb | Trojan.PWS.Stealer.34727 |
| VIPRE | Trojan.GenericKD.70612133 |
| TrendMicro | Trojan.Win32.SMOKELOADER.YXDK3Z |
| Trapmine | malicious.high.ml.score |
| Emsisoft | Trojan.GenericKD.70612133 (B) |
| SentinelOne | Static AI – Malicious PE |
| Jiangmin | Trojan.Chapak.rrw |
| Varist | W32/Kryptik.LDY.gen!Eldorado |
| Avira | TR/Crypt.Agent.kakul |
| Antiy-AVL | Trojan/Win32.Caynamer |
| Kingsoft | Win32.Troj.Agent.cks |
| Microsoft | troyen:Win32/SmokeLoader!pz |
| ZoneAlarm | HEUR:Trojan.Win32.Chapak.gen |
| GData | Trojan.GenericKD.70612133 |
| Detected | |
| AhnLab-V3 | Malware/Win.RansomX-gen.R625969 |
| McAfee | Artemis!284EC46A8277 |
| MAX | malware (ai score=85) |
| VBA32 | BScope.Trojan.Yakes |
| Malwarebytes | Trojan.MalPack.GS |
| Panda | Trj/Genetic.gen |
| TrendMicro-HouseCall | Trojan.Win32.SMOKELOADER.YXDK3Z |
| Rising | Trojan.SmokeLoader!1.EB63 (CLASSIC) |
| Ikarus | Trojan.Win32.Azorult |
| MaxSecure | Trojan.Malware.73643692.susgen |
| Fortinet | W32/GenKryptik.ERHN!tr |
| MOYENNE | IDP.Generic |
| DeepInstinct | MALICIOUS |
| CrowdStrike | win/malicious_confidence_100% (W) |
How to remove?
troyen:Win32/SmokeLoader!pz malware is very hard to eliminate manually. It stores its data in several places throughout the disk and can get back itself from one of the parts. En plus, various alterations in the Windows registry, networking configurations, and also Group Policies are pretty hard to discover and return to the initial. It is better to use a specific app – exactly, an anti-malware tool. Gridinsoft anti-malware will fit the best for malware elimination goals.
Retirer le Troie:Win32/SmokeLoader!pz with Gridinsoft Anti-Malware
Nous utilisons également ce logiciel sur nos systèmes depuis, et il a toujours réussi à détecter les virus. It has blocked the most common Trojans as montré par nos tests avec le logiciel, Et nous vous assurons qu'il peut supprimer le Troie:Win32/SmokeLoader!pz as well as other malware hiding on your computer.
Pour utiliser Gridinsoft pour supprimer les menaces malveillantes, suivez les étapes ci-dessous:
1. Commencez par télécharger Gridinsoft Anti-Malware, accessible via le bouton bleu ci-dessous ou directement depuis le site officiel grilleinsoft.com.
2.Une fois le fichier d'installation de Gridinsoft (setup-gridinsoft-fix.exe) est téléchargé, exécutez-le en cliquant sur le fichier. Follow the installation setup wizard's instructions diligently.
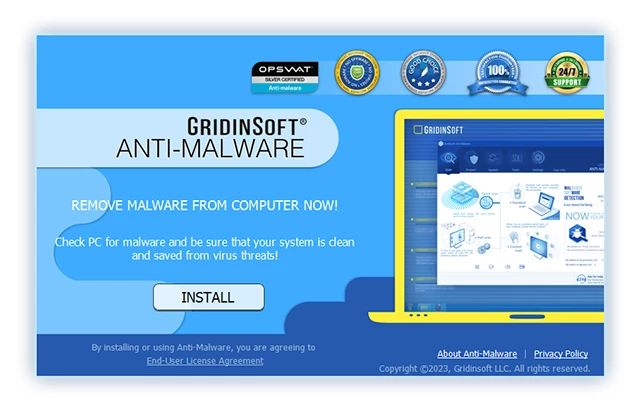
3. Accéder au "Onglet Numérisation" on the application's start screen and launch a comprehensive "Scan complet" pour examiner l'intégralité de votre ordinateur. Cette analyse inclusive englobe la mémoire, éléments de démarrage, le registre, prestations de service, Conducteurs, et tous les fichiers, s'assurer qu'il détecte les logiciels malveillants cachés dans tous les emplacements possibles.
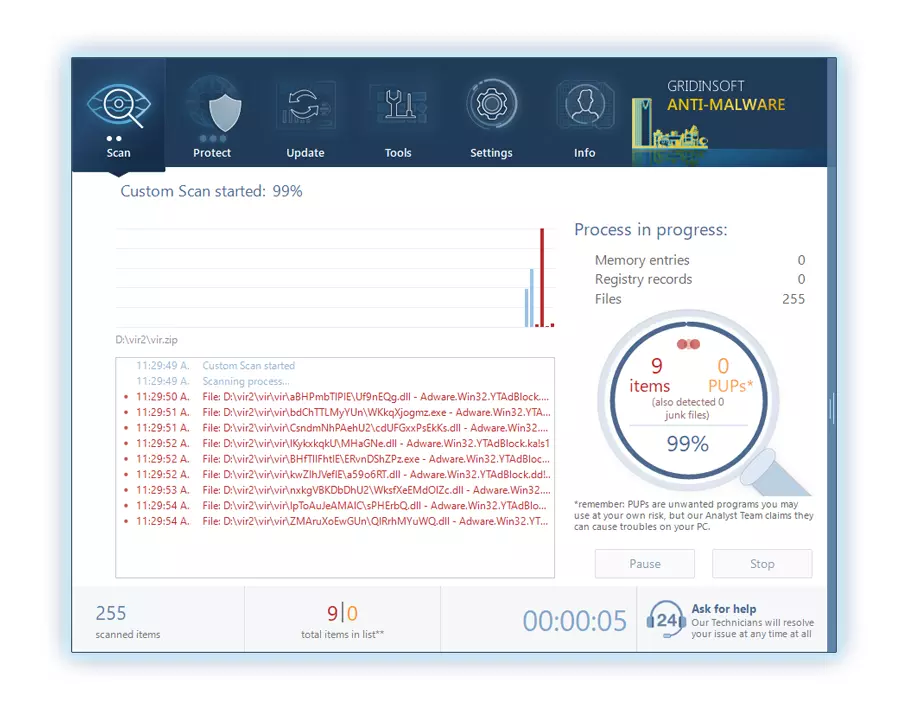
Sois patient, as the scan duration depends on the number of files and your computer's hardware capabilities. Profitez de ce temps pour vous détendre ou vous occuper d'autres tâches.
4. Une fois terminé, Anti-Malware présentera un rapport détaillé contenant tous les éléments malveillants et menaces détectés sur votre PC.
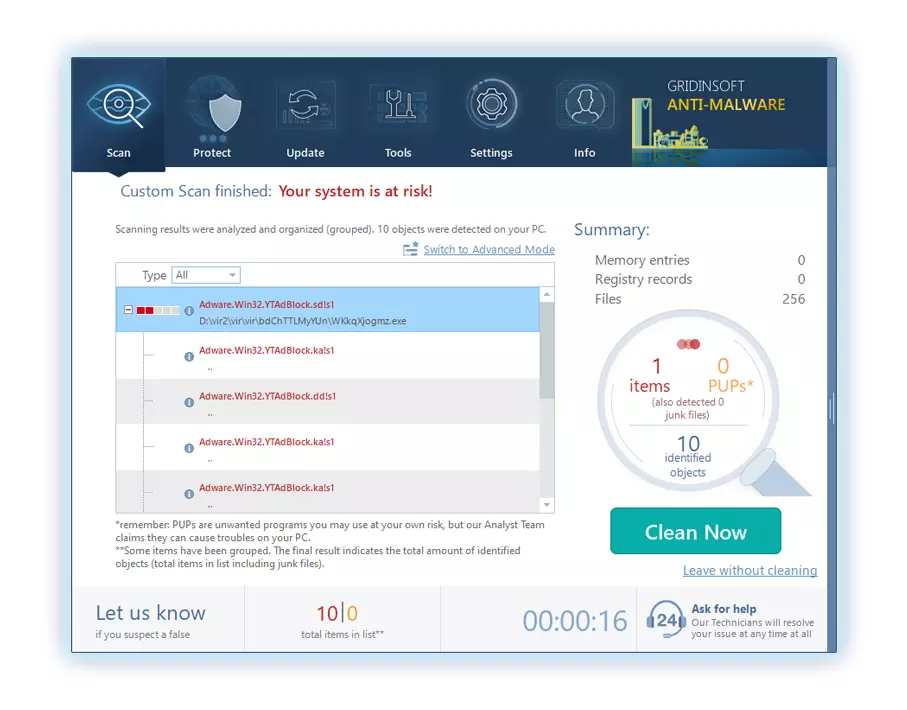
5. Sélectionnez tous les éléments identifiés dans le rapport et cliquez en toute confiance sur le "Nettoie maintenant" bouton. Cette action supprimera en toute sécurité les fichiers malveillants de votre ordinateur, les transférer vers la zone de quarantaine sécurisée du programme anti-malware pour éviter toute autre action nuisible.
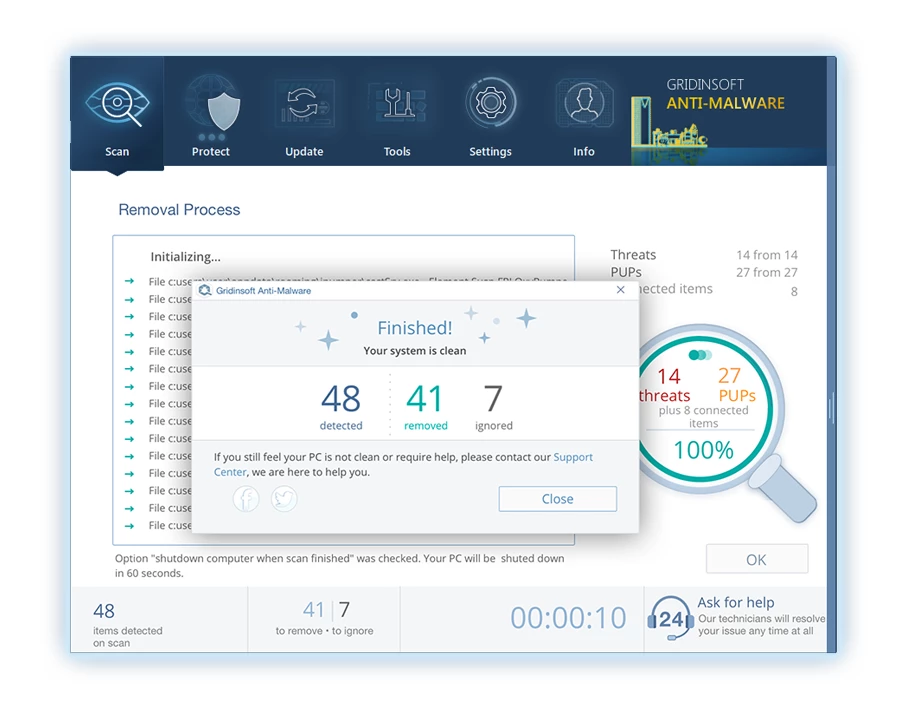
6. Si vous y êtes invité, redémarrez votre ordinateur pour finaliser la procédure d'analyse complète du système. Cette étape est cruciale pour garantir la suppression complète de toutes les menaces restantes.. Après le redémarrage, Gridinsoft Anti-Malware s'ouvrira et affichera un message confirmant le fin de l'analyse.
N'oubliez pas que Gridinsoft propose un essai gratuit de 6 jours. Cela signifie que vous pouvez profiter gratuitement de la période d'essai pour profiter de tous les avantages du logiciel et prévenir toute future infection par des logiciels malveillants sur votre système.. Embrace this opportunity to fortify your computer's security without any financial commitment.







Laissez un commentaire