¿Qué es el virus Veza??
El virus Veza es como un mal hechizo mágico que bloquea los archivos en las computadoras para que no pueda usarlos. Cambia los nombres de los archivos agregando “.conexión” al final, lo que significa que no puedes abrirlos sin una llave especial.
Cuando Veza entra en una computadora, Pide dinero, pagado en bitcoin, para desbloquear los archivos. Deja una nota llamada “_readme.txt” en el escritorio y en carpetas diciéndole cómo pagar el dinero. Pero incluso si pagas, No hay promesa de que sus archivos se desbloqueen.
El virus usa un bloqueo difícil llamado Algoritmo de cifrado SALSA20 Eso hace que sea muy difícil abrir los archivos sin la ayuda del chico malo. Pero si el virus VEZA no podía hablar con su base de operaciones antes de bloquear los archivos, Utiliza un bloqueo más simple que podría ser más fácil de abrir.
Abajo, Una imagen muestra cómo se ven los archivos bloqueados, marcado por el “.conexión” extensión:
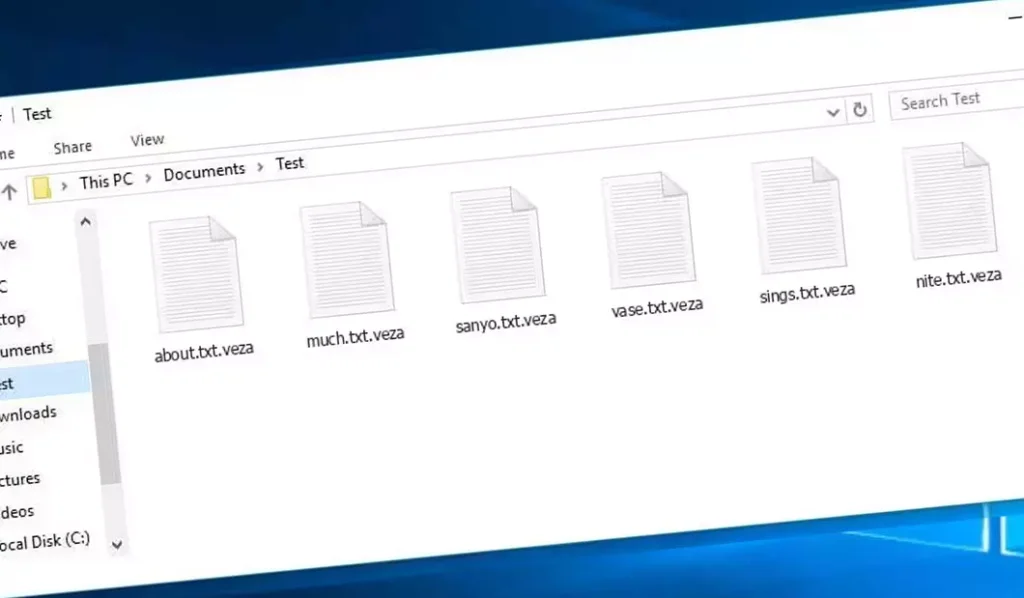
Archivos cifrados por VEZA Ransomware
| Nombre | Un virus de unión |
| Familia 1 | Parada / ransomware DJVU |
| Extensión | .conexión |
| Nota de ransomware | _readme.txt |
| Rescate | De $499 a $999 (en bitcoins) |
| Contacto | support@freshingmail.top, datarestorehelpyou@airmail.cc |
| Síntomas |
|
| Recuperación | Iniciar recuperación con un integral exploración antivirus. Aunque no todos los archivos pueden ser recuperables, Nuestra guía describe varios métodos potenciales para recuperar el acceso a los archivos cifrados. |
Descripción general del virus VEZA
Cuando el virus VEZA sube a una computadora, comienza a hacer muchas cosas astutas. Primero, Finge ser una actualización de Windows con un mensaje falso de un programa llamado winupdate.exe para engañar al usuario de la computadora para que piense que todo es normal.
Al mismo tiempo, Ejecuta otro programa secreto que comienza a buscar archivos importantes en la computadora para bloquearlos. También usa un comando especial:
vssadmin.exe Eliminar sombras /todo /tranquilo
Este comando evita que la computadora pueda volver a cómo era antes del virus, lo que significa que no puede arreglar fácilmente lo que cambia el virus.
El virus también se mete con una lista en la computadora que le ayuda a encontrar sitios web. Cambia esta lista para que algunos sitios web ya no funcionen, especialmente sitios que podrían ayudar a arreglar la computadora o dar consejos sobre el virus. Hace esto haciendo que la computadora piense que estos sitios web están solo en su computadora y en ningún otro lugar, que no es cierto.
El virus también deja atrás dos archivos de texto en la computadora que tienen códigos secretos relacionados con el ataque, estos se llaman bowsakkdestx.txt y Personalid.txt.
Pero eso no es todo. Este virus también puede escabullirse en otro programa malo llamado Vidar, que puede robar contraseñas y otras cosas privadas de la computadora. Esto es lo que Vidar puede hacer:
- Poner otros programas malos en la computadora.
- Robar contraseñas de programas como Steam, Telegrama, y Skype.
- Mire y cambie los archivos sin que sepa.
- Robar billeteras de dinero digital.
- Deje que los hackers controlen la computadora desde muy lejos.
- Tome información privada como los sitios web que visita y sus contraseñas guardadas.
El virus Veza usa un bloqueo súper resistente llamado salsa20 para mantener los archivos bloqueados. Si bloquea sus archivos con una llave especial, solo sabe, Es realmente difícil desbloquearlos de nuevo. Cada clave es diferente para todos, haciendo que sea casi imposible adivinar.
Si desea obtener la clave para desbloquear sus archivos, Los piratas informáticos piden $999. Te dicen que les envíe un correo electrónico a (support@fishmail.top) para averiguar cómo pagarles.
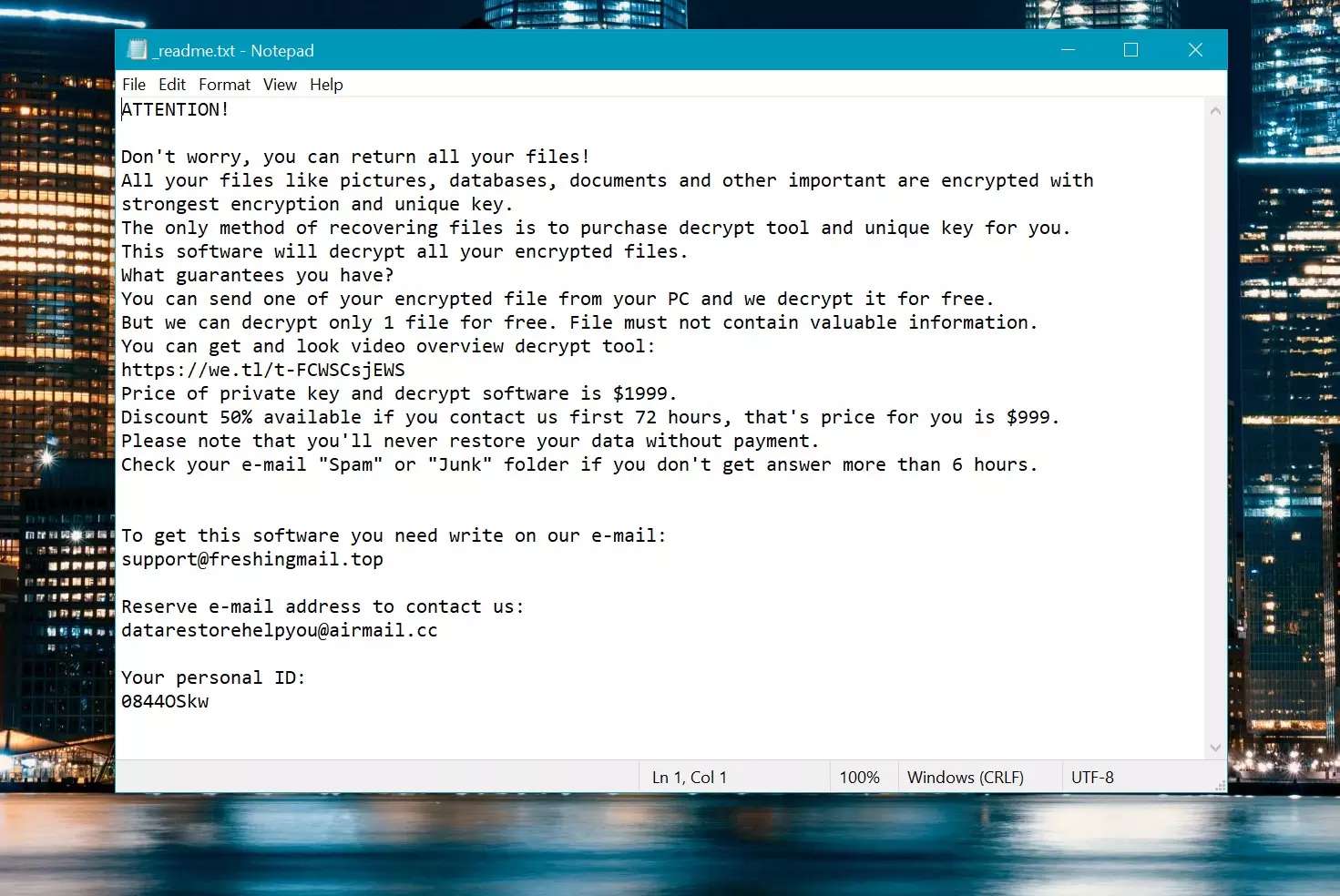
Nota de rescate: _readme.txt
Cómo quitar?
Eliminar el virus VEZA con el anti-malware de GridinSoft
También hemos estado utilizando este software en nuestros sistemas desde entonces., y siempre ha tenido éxito en la detección de virus.. Ha bloqueado el ransomware más común como mostrado en nuestras pruebas con el software, y le aseguramos que puede eliminar el virus VEZA, así como otro malware que se esconde en su computadora..
Para utilizar Gridinsoft para eliminar amenazas maliciosas, sigue los pasos a continuación:
1. Comience descargando Gridinsoft Anti-Malware, accesible a través del botón azul a continuación o directamente desde el sitio web oficial gridinsoft.com.
2.Una vez que el archivo de instalación de Gridinsoft (setup-gridinsoft-fix.exe) se descarga, ejecutarlo haciendo clic en el archivo. Follow the installation setup wizard's instructions diligently.
3. Acceder al "Pestaña Escanear" on the application's start screen and launch a comprehensive "Análisis completo" para examinar toda su computadora. Este escaneo inclusivo abarca la memoria., elementos de inicio, el registro, servicios, conductores, y todos los archivos, asegurando que detecta malware oculto en todas las ubicaciones posibles.
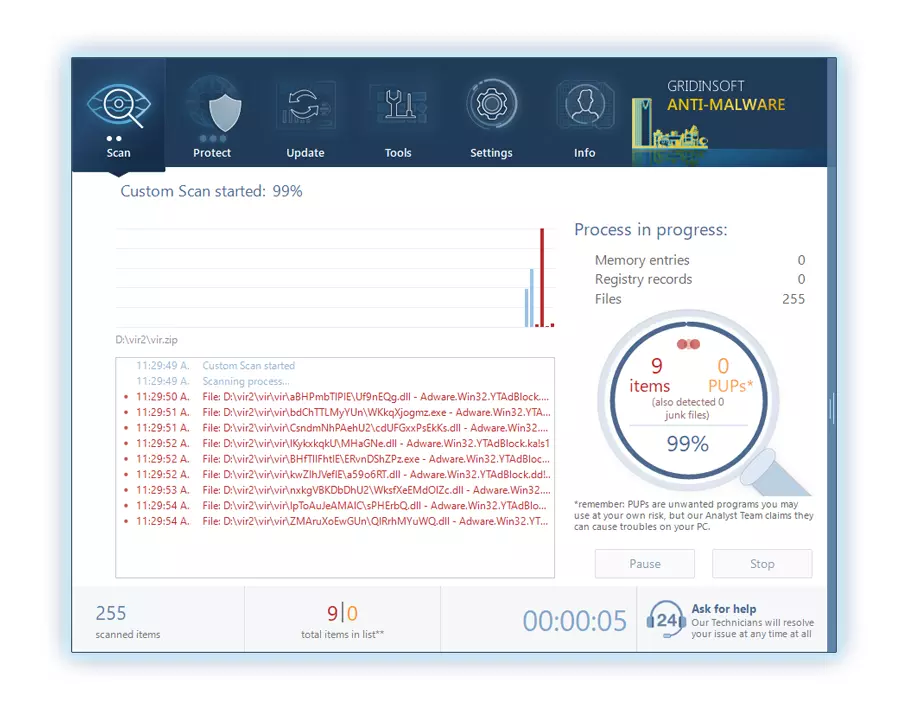
Ser paciente, as the scan duration depends on the number of files and your computer's hardware capabilities. Utilice este tiempo para relajarse o atender otras tareas..
4. Al finalizar, Anti-Malware presentará un informe detallado que contiene todos los elementos maliciosos y amenazas detectados en su PC.
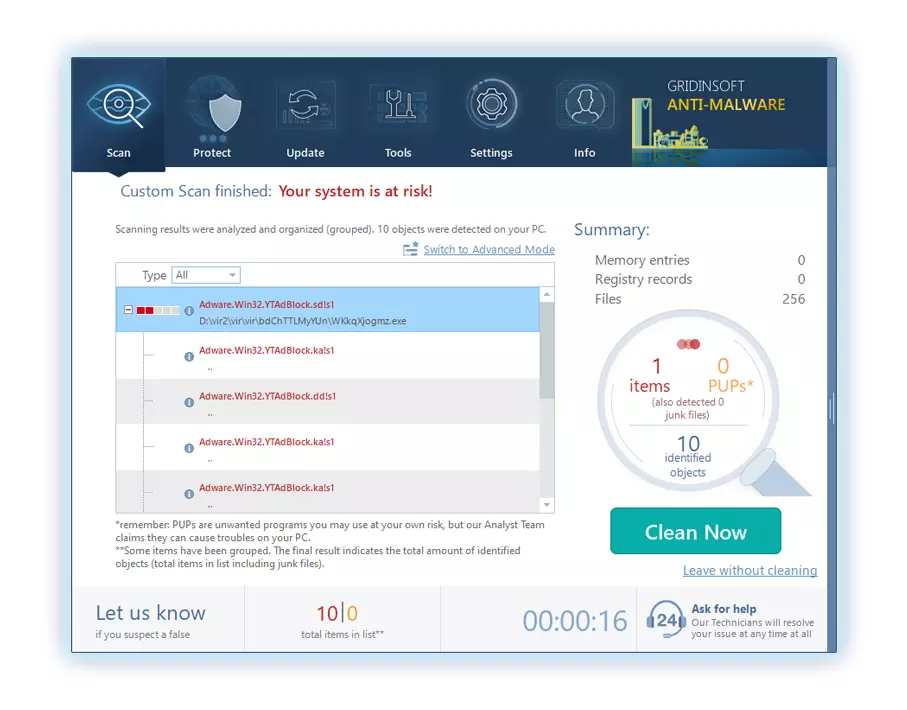
5. Seleccione todos los elementos identificados del informe y haga clic con confianza en el "Limpio ahora" botón. Esta acción eliminará de forma segura los archivos maliciosos de su computadora., transfiriéndolos a la zona de cuarentena segura del programa antimalware para evitar futuras acciones dañinas.
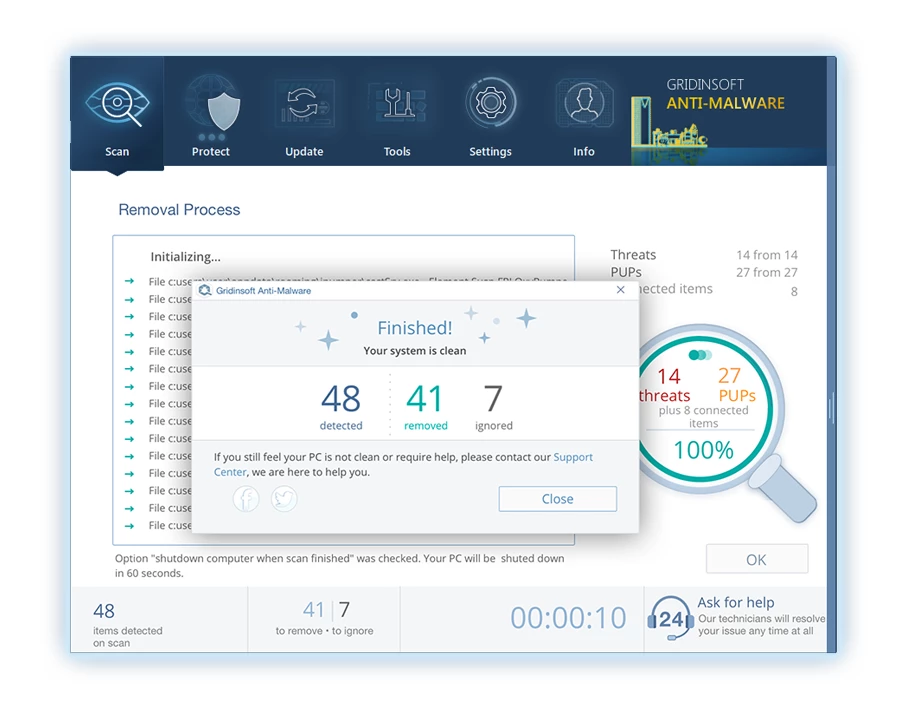
6. Si se le solicita, reinicie su computadora para finalizar el procedimiento de escaneo completo del sistema. Este paso es crucial para garantizar la eliminación completa de cualquier amenaza restante.. Después del reinicio, Gridinsoft Anti-Malware se abrirá y mostrará un mensaje confirmando la finalización del escaneo.
Recuerde Gridinsoft ofrece una prueba gratuita de 6 días. Esto significa que puede aprovechar el período de prueba sin costo alguno para experimentar todos los beneficios del software y prevenir futuras infecciones de malware en su sistema.. Embrace this opportunity to fortify your computer's security without any financial commitment.
Guía de vídeo
Cómo descifrar los archivos .vza?
Primero, Intenta eliminar el “.conexión” extensión de algunos archivos grandes y luego abrirlos. Este malware lucha con el cifrado de archivos grandes. El virus no pudo bloquear el archivo al acceso o encontró un error y omitió agregar el marcador de archivo. Si sus archivos exceden 2 GB de tamaño, el último escenario es más probable.
Los delincuentes publicaron las extensiones más nuevas a fines de agosto 2019 Después de hacer varios cambios.
Los cambios por parte de los delincuentes dejaron stopdecrypter sin apoyo, Conduciendo a su reemplazo con el descifrador Emsisoft para el ransomware DJVU desarrollado por Emsisoft.
- Descargue y ejecute la herramienta de descifrado: Descargar herramienta de descifrado. Asegúrese de ejecutar la utilidad de descifrado como administrador y acepte los términos de la licencia que aparecen haciendo clic en el “Sí” botón. Al aceptar los términos de la licencia.
- Seleccione carpetas para el descifrado: El descifrador, por defecto, Selecciona automáticamente directorios en unidades conectadas y de red para el descifrado. Usar el “Agregar” botón para seleccionar ubicaciones adicionales. Dependiendo de la familia de malware, Los descifrantes ofrecen varias opciones, que puede activar o desactivar en la pestaña Opciones. Abajo, Encontrará una lista detallada de las opciones actualmente activas.
- Iniciar el descifrado haciendo clic en el “Descifrar” Botón. Después de agregar todas las ubicaciones deseadas a la lista, haga clic en el “Descifrar” botón para iniciar el proceso de descifrado. El Decryptor le informará al completar el proceso de descifrado. Si es necesario para la documentación, Puede guardar el informe haciendo clic en el “Guardar registro” botón. También es posible copiar el informe a su portapapeles para pegar correos electrónicos o mensajes..
Cómo restaurar los archivos .veza?
En algún caso, El ransomware no puede cifrar sus archivos…
El proceso de cifrado de ransomware VEZA implica cifrar cada archivo byte-by byte, creando un duplicado, y luego eliminar (No sobrescribir) el archivo original. Esta eliminación significa que el disco físico ya no enumera el archivo en su sistema, Aunque el archivo original permanece en la unidad. El sector que contenía el archivo aún podría contenerlo, Pero dado que el sistema no lo enumera, Los nuevos datos pueden sobrescribirlo. Sin embargo, El software especial puede recuperar sus archivos.
Darse cuenta de que era un algoritmo en línea, Sabía que recuperar mis archivos encriptados era imposible. Mi unidad de copia de seguridad, conectado durante la infección, parecía infectado también. Cada carpeta de mi unidad de copia de seguridad apareció encriptada. A pesar de esto, Logré recuperarme casi 80% de mi almacenamiento de 2tb.
Examinando las carpetas, Encontré notas de rescate en cada. La apertura de algunos reveló que solo los archivos que no estaban en subcarpetas estaban encriptados. Profundizar en subcarpetas en otras carpetas, Descubrí archivos sin cifrar. A diferencia de mis unidades C y D, donde cada carpeta, incluyendo subcarpetas, fue encriptado, Las subcarpetas de mi unidad de respaldo se guardan 80% de mis datos.
Considero encontrar esta escapatoria en mi impulso de respaldo afortunado. Además, Recuperé otro 10% de mis datos de un disco duro en una PC diferente. De este modo, Mi consejo para usar una unidad de copia de seguridad es crear subcarpetas.. Fue en parte suerte, pero también desgracia que el virus golpeó durante las transferencias de archivo desde mi copia de seguridad.
Espero que esta experiencia pueda ayudar a otros en predicamentos similares..
Jamie NewlandRecupere sus archivos con Photorec
Fotorecia, Diseñado para la recuperación de archivos de discos dañados o eliminación accidental, ahora admite la restauración 400 tipos de archivos, haciéndolo útil después de un ataque de Veza.
Primero, Descargar fotorec. Es gratis, Pero el desarrollador no ofrece garantía para la restauración de archivos. Photorec viene empaquetado con TestDisk, otra herramienta del mismo desarrollador, Bajo el nombre de Testdisk. Sin embargo, Photorec se incluye dentro del archivo.
Para comenzar Photorec, abrir el “qphotorec_win.exe” archivo. No es necesaria una instalación ya que el programa contiene todos los archivos requeridos., permitiendo que se ejecute desde una unidad USB.



Deja un comentario