Verification.exe is a malicious process found on Windows systems. It may serve as a miner or pose as legitimate while being malicious. This malicious software is designed to execute various harmful operations on compromised systems. Such actions encompass data theft, deployment of further malware, and facilitation of unauthorized access and control by attackers.
Verification.exe Overview
The Verification.exe Trojan is a harmful program that can cause various issues on your compromised computer. It can be used to steal personal data, install other malware, and provide unauthorized access to attackers. This Trojan carries out various malicious activities, such as downloading and installing other malware, exploiting your computer for click fraud, logging keystrokes, and tracking visited sites.
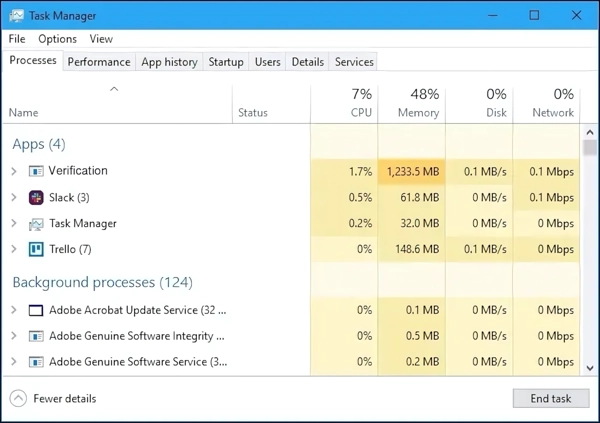
Verification.exe process in the Task manager
It can also transmit your PC information, like usernames and browsing history, to remote malicious entities, grant remote access to your PC, display advertisements, and redirect browser search queries. Además, it can utilize your computer resources for cryptocurrency mining. It is crucial to be aware of this Trojan’s potential threats and take steps to protect your computer from such attacks.
Resumen de amenazas
| Nombre | Verification.exe |
| Tipo de amenaza | Virus troyano |
| Detalles | Steals personal data, brings other malicious programs, mangles system security, can mine cryptocurrencies. |
The reason why this malware has picked the Verification.exe name is rather simple – to blend in with other background process. This typically makes the user think it is legit. Sin embargo, when it takes too much system resources, or runs regardless of what program is running, then it’s time for raising the alarm.
How did I get infected?
The Verification.exe can infiltrate your system in various ways. One standard method is through malicious ads that may appear while browsing the internet. These ads can trick you into clicking on a link or downloading an attachment that contains the Trojan. Another way the malware can spread is through spam emails, which may contain infected attachments. It can also take advantage of your operating system or software vulnerabilities to gain access to your system.
Another distribution method is through pirated software or illegal downloads. Most pirated software requires mandatory disabling of the security software on the device. This is because the mechanics of hacking tools are similar to those of malware, making it ideal for spreading it. Entonces, supposeå you are downloading software from an untrusted source or engaging in software piracy. In that case, you are putting your system at risk.
Remove Verification.exe with Gridinsoft Anti-Malware
También hemos estado utilizando este software en nuestros sistemas desde entonces., y siempre ha tenido éxito en la detección de virus.. Ha bloqueado los troyanos más comunes como mostrado en nuestras pruebas con el software, and we assure you that it can remove Verification.exe as well as other malware hiding on your computer.
Para utilizar Gridinsoft para eliminar amenazas maliciosas, sigue los pasos a continuación:
1. Comience descargando Gridinsoft Anti-Malware, accesible a través del botón azul a continuación o directamente desde el sitio web oficial gridinsoft.com.
2.Una vez que el archivo de instalación de Gridinsoft (setup-gridinsoft-fix.exe) se descarga, ejecutarlo haciendo clic en el archivo. Follow the installation setup wizard's instructions diligently.
3. Acceder al "Pestaña Escanear" on the application's start screen and launch a comprehensive "Análisis completo" para examinar toda su computadora. Este escaneo inclusivo abarca la memoria., elementos de inicio, el registro, servicios, conductores, y todos los archivos, asegurando que detecta malware oculto en todas las ubicaciones posibles.
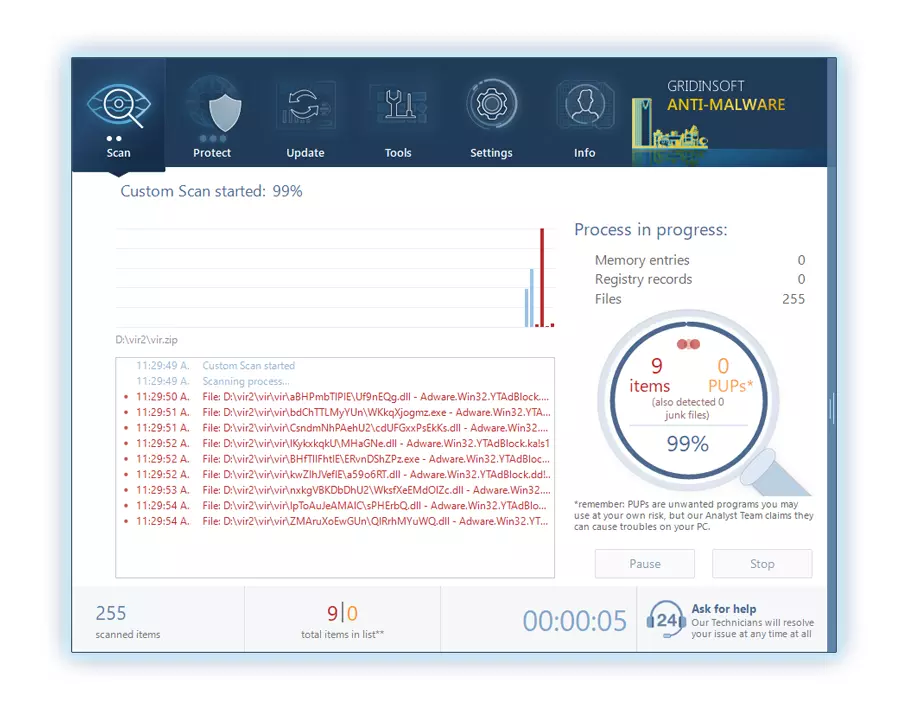
Ser paciente, as the scan duration depends on the number of files and your computer's hardware capabilities. Utilice este tiempo para relajarse o atender otras tareas..
4. Al finalizar, Anti-Malware presentará un informe detallado que contiene todos los elementos maliciosos y amenazas detectados en su PC.
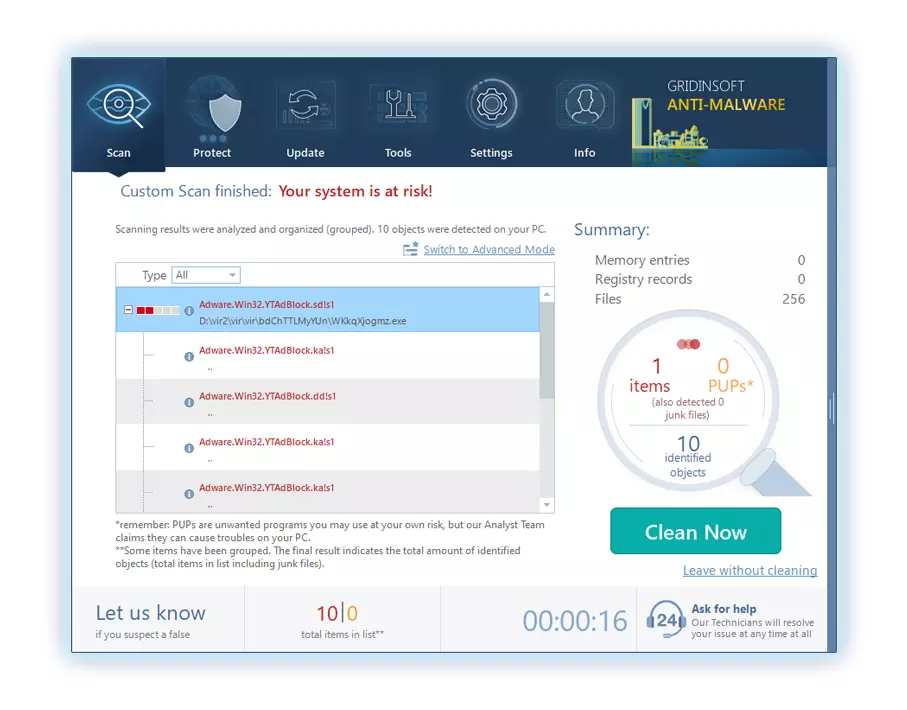
5. Seleccione todos los elementos identificados del informe y haga clic con confianza en el "Limpio ahora" botón. Esta acción eliminará de forma segura los archivos maliciosos de su computadora., transfiriéndolos a la zona de cuarentena segura del programa antimalware para evitar futuras acciones dañinas.
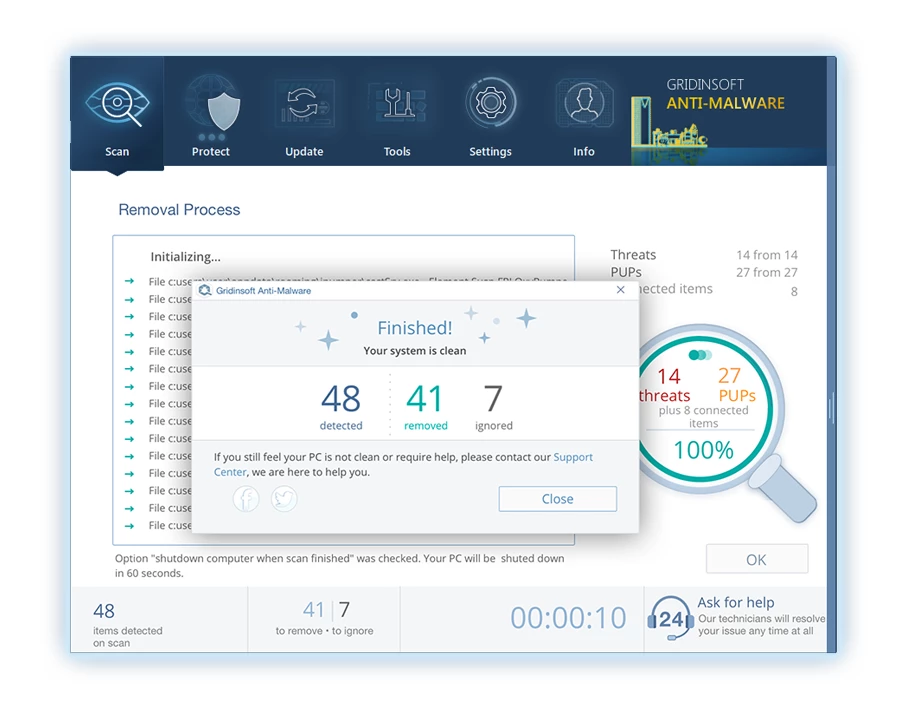
6. Si se le solicita, reinicie su computadora para finalizar el procedimiento de escaneo completo del sistema. Este paso es crucial para garantizar la eliminación completa de cualquier amenaza restante.. Después del reinicio, Gridinsoft Anti-Malware se abrirá y mostrará un mensaje confirmando la finalización del escaneo.
Recuerde Gridinsoft ofrece una prueba gratuita de 6 días. Esto significa que puede aprovechar el período de prueba sin costo alguno para experimentar todos los beneficios del software y prevenir futuras infecciones de malware en su sistema.. Embrace this opportunity to fortify your computer's security without any financial commitment.






Deja un comentario