troyano:Script/Phonzy.b!ml is a detection name used by Microsoft Defender to detect a script-based loader malware. As the detection comes from the AI detection system, there is a chance of it being a false positive.
The more time such a threat remains active, the more malware it can inject into it. Phonzy.B!ml trojan in particular aims at deploying banking trojans that steal online banking services’ credentials. Removing it should be a primary concern.
troyano:Script/Phonzy.b!ml Summary
As I just said, troyano:Script/Phonzy.b!ml operates as a malware downloader, facilitating the injection of additional viruses into the system. It commonly adjusts system configurations, particularly networking settings and Microsoft Defender. This makes it particularly hard to remove without using additional security tools.
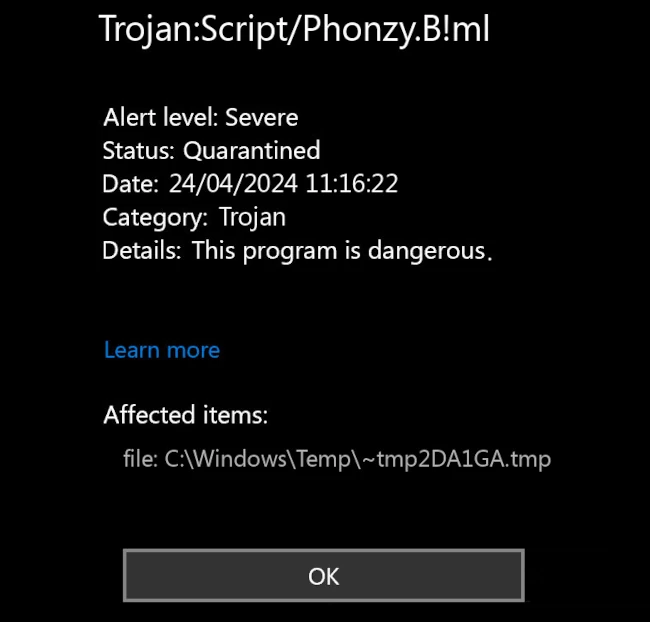
Phonzy.B!ml detection image
Main target of Phonzy.B!ml activity is deploying banking trojans, as far as my observations go. Using DLL hijacking techniques, this malware hooks up malicious programs, effectively granting them max privileges. Following the first post-injection steps, this malware connects to the command servers and waits for the command.
Resumen de amenazas:
| Nombre | Phonzy Trojan |
| Detección | troyano:Script/Phonzy.b!ml |
| Detalles | Phonzy acts as a downloader for other malware, performing initial reconnaissance and weakening the system security. |
Al mismo tiempo, nothing restricts Phonzy from delivering other malware. Everything boils down to who pays, and the rest is unimportant to this malware’s masters. Using the same methods, the malware can deploy spyware, backdoors and even ransomware. The effects of all this malware activity are unpleasant, to say the least – lost online accounts, encrypted files and third-parties being able to control the system remotely.
How Did Trojan:Script/Phonzy.b!ml Get Into My System?
Más a menudo, malware like Phonzy.B!ml arrives to the system as a part of cracked software or a program downloaded from a shady source. Users can see advertisements in search engines that pose as original software downloading pages, but are in fact malignant copies. Cracked software, on the other hand, is typically spread on dedicated websites.
It is worth noting that hackers constantly seek for new malware spreading ways. Either by modifying already existing approaches, or targeting some new trends, they achieve much higher infection rates. Users should keep track of the latest trends and stay away from all the related elements.
Is it a False Positive?
Microsoft’s detection naming convention reveals that the “!ml” designation stands for “machine learning,” indicating detection by their AI engine. While effective, it necessitates confirmation from a signature detection system to avoid false positives. When none is available, the built-in antivirus may display a detection of a completely legit file.
The problem here is that it is not easy to understand whether it is a real of a false detection. Differentiating between them is particularly hard as modern malware often conceals itself among legitimate files. That is yet another reason why I recommend using a different anti-malware tool.
Eliminar troyano:Script/Phonzy.b!ml con Gridinsoft Anti-Malware
También hemos estado utilizando este software en nuestros sistemas desde entonces., y siempre ha tenido éxito en la detección de virus.. Ha bloqueado los virus troyanos más comunes como mostrado en nuestras pruebas con el software, y te aseguramos que puede eliminar el troyano:Script/Phonzy.b!ml y otros programas maliciosos escondidos en su computadora.
Para utilizar Gridinsoft para eliminar amenazas maliciosas, sigue los pasos a continuación:
1. Comience descargando Gridinsoft Anti-Malware, accesible a través del botón azul a continuación o directamente desde el sitio web oficial gridinsoft.com.
2.Una vez que el archivo de instalación de Gridinsoft (setup-gridinsoft-fix.exe) se descarga, ejecutarlo haciendo clic en el archivo. Follow the installation setup wizard's instructions diligently.
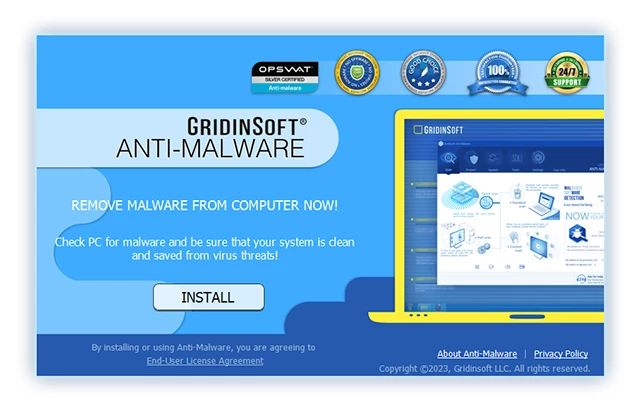
3. Acceder al "Pestaña Escanear" on the application's start screen and launch a comprehensive "Análisis completo" para examinar toda su computadora. Este escaneo inclusivo abarca la memoria., elementos de inicio, el registro, servicios, conductores, y todos los archivos, asegurando que detecta malware oculto en todas las ubicaciones posibles.
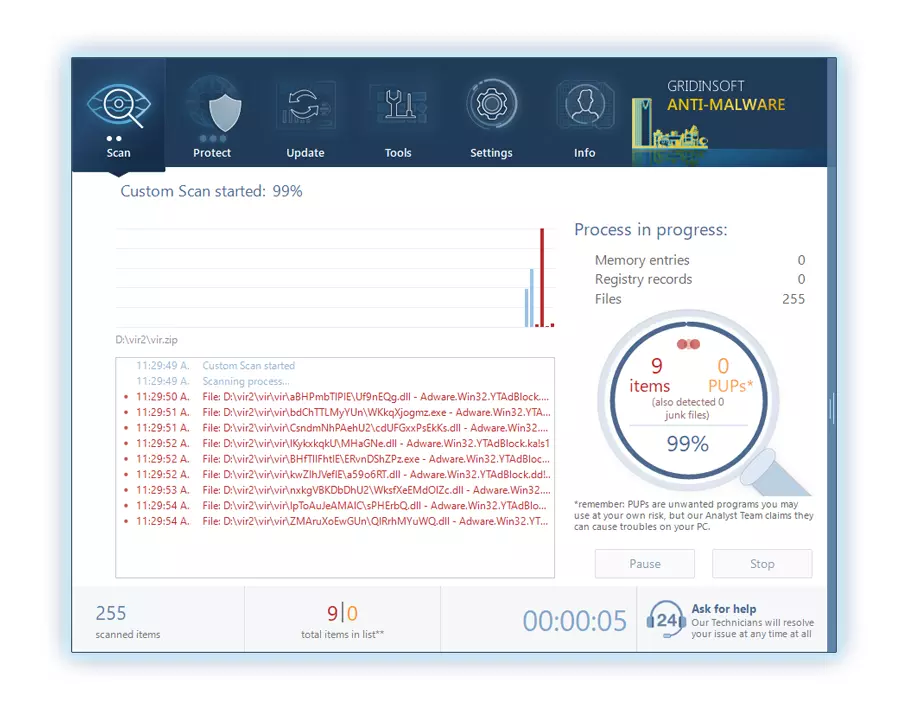
Ser paciente, as the scan duration depends on the number of files and your computer's hardware capabilities. Utilice este tiempo para relajarse o atender otras tareas..
4. Al finalizar, Anti-Malware presentará un informe detallado que contiene todos los elementos maliciosos y amenazas detectados en su PC.
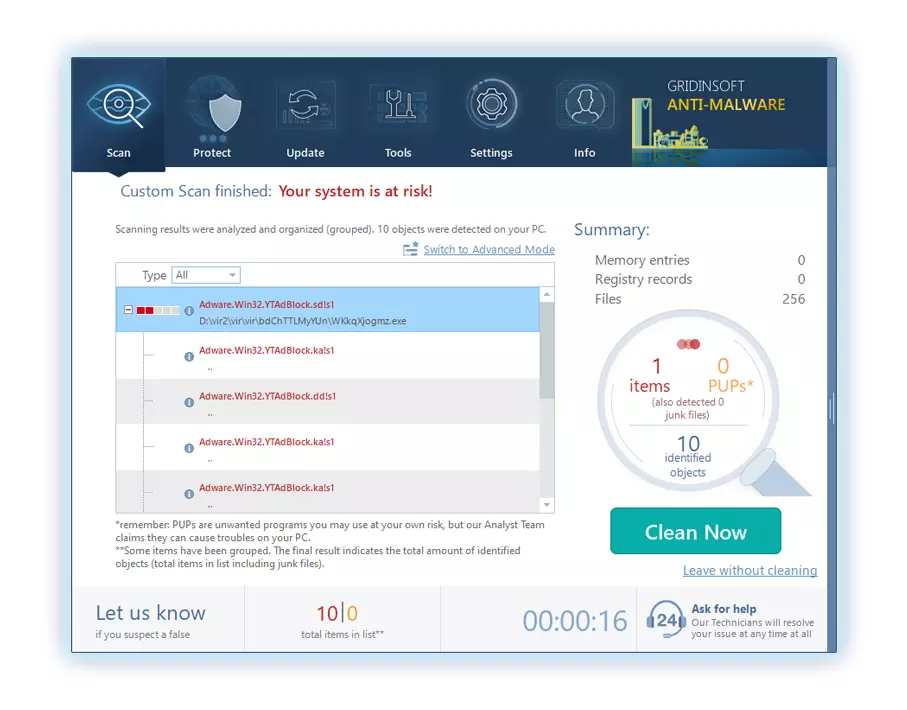
5. Seleccione todos los elementos identificados del informe y haga clic con confianza en el "Limpio ahora" botón. Esta acción eliminará de forma segura los archivos maliciosos de su computadora., transfiriéndolos a la zona de cuarentena segura del programa antimalware para evitar futuras acciones dañinas.
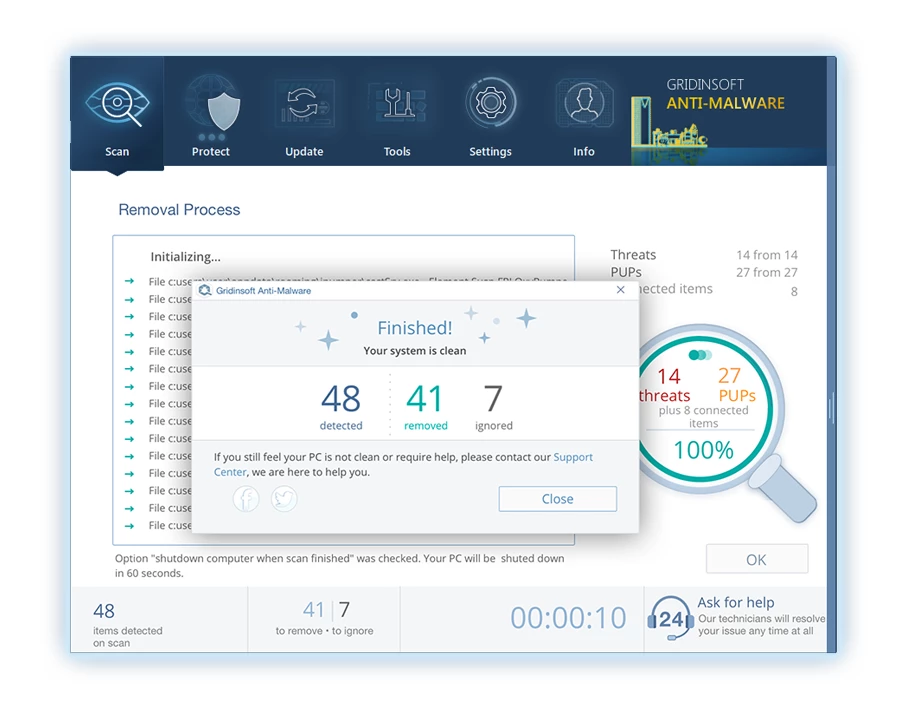
6. Si se le solicita, reinicie su computadora para finalizar el procedimiento de escaneo completo del sistema. Este paso es crucial para garantizar la eliminación completa de cualquier amenaza restante.. Después del reinicio, Gridinsoft Anti-Malware se abrirá y mostrará un mensaje confirmando la finalización del escaneo.
Recuerde Gridinsoft ofrece una prueba gratuita de 6 días. Esto significa que puede aprovechar el período de prueba sin costo alguno para experimentar todos los beneficios del software y prevenir futuras infecciones de malware en su sistema.. Embrace this opportunity to fortify your computer's security without any financial commitment.







Deja un comentario