發現一款在 USB 驅動器上運行的經濟實惠的防病毒軟件並不容易. 本文將揭示為什麼 Gridinsoft Trojan Killer 能夠成為滿足您數字保護需求的理想伴侶,並指導您有效利用其強大功能.
在我們互聯的世界中, 反惡意軟件的發展反映了全球化的步伐. 隨著每次更新, 卡巴斯基和諾頓等領先的防病毒解決方案擴展了其產品範圍, 成為數字保護的瑞士軍刀. 他們保護密碼, 用於按鍵監控的監控應用程序, 提供家長控制, 並加強瀏覽器安全, 全部包含在一個包中. 這種包羅萬象的方法太棒了, 前提是您的系統能夠毫不費力地承受如此廣泛的功能. 然而, 對於那些設置不太穩健的人, 這些龐然大物的程序可能會壟斷 60-70% 系統資源, 除了基本任務之外,幾乎沒有留下任何空間.
在此背景下, 越來越多的用戶正在尋找靈活的, 然而有效的替代方案涵蓋了基本的安全措施,例如掃描和網絡修復,而不會造成臃腫. 上面的櫻桃? 可移植性. 可以靈活地通過 USB 記憶棒攜帶防病毒軟件, 準備好在任何 PC 上立即採取行動, 對許多人來說不僅是一種便利,而且是必需品, 從日常用戶到 IT 專業人員. 在眾多承諾很多但效果甚微的選擇中, Gridinsoft Trojan殺手 成為不折不扣地滿足這些標準的稀有寶石.
木馬殺手的主要特點
是什麼讓 木馬殺手 我選擇的防病毒軟件? 超越其 令人難以置信的靈活性, 它對系統資源的佔用非常少. 然而, 它不吝惜功能, 奉獻 所有必要的反惡意軟件功能: 全面的系統掃描, 有針對性的可移動驅動器檢查, 可定制的掃描, 和專用的瀏覽器修復工具. 此瀏覽器修復功能, 獨特但與主應用程序無縫集成, 脫穎而出,證明了 Trojan Killer 的深思熟慮的設計.
特洛伊木馬殺手的威力還不止於此. 其突出特點是 能夠直接從 USB 驅動器進行操作, 將任何可移動存儲轉變為強大的惡意軟件根除設備. 這種級別的可移植性確保軟件不會受到惡意軟件的影響, 允許有效清理受感染的電腦 在任何情況下. 與領先的文件/磁盤恢復工具(如 PhotoRec 或 ReclaiMe)相結合, 它形成了一個不可或缺的工具包,可以解決惡意軟件攻擊後的幾乎所有挑戰.
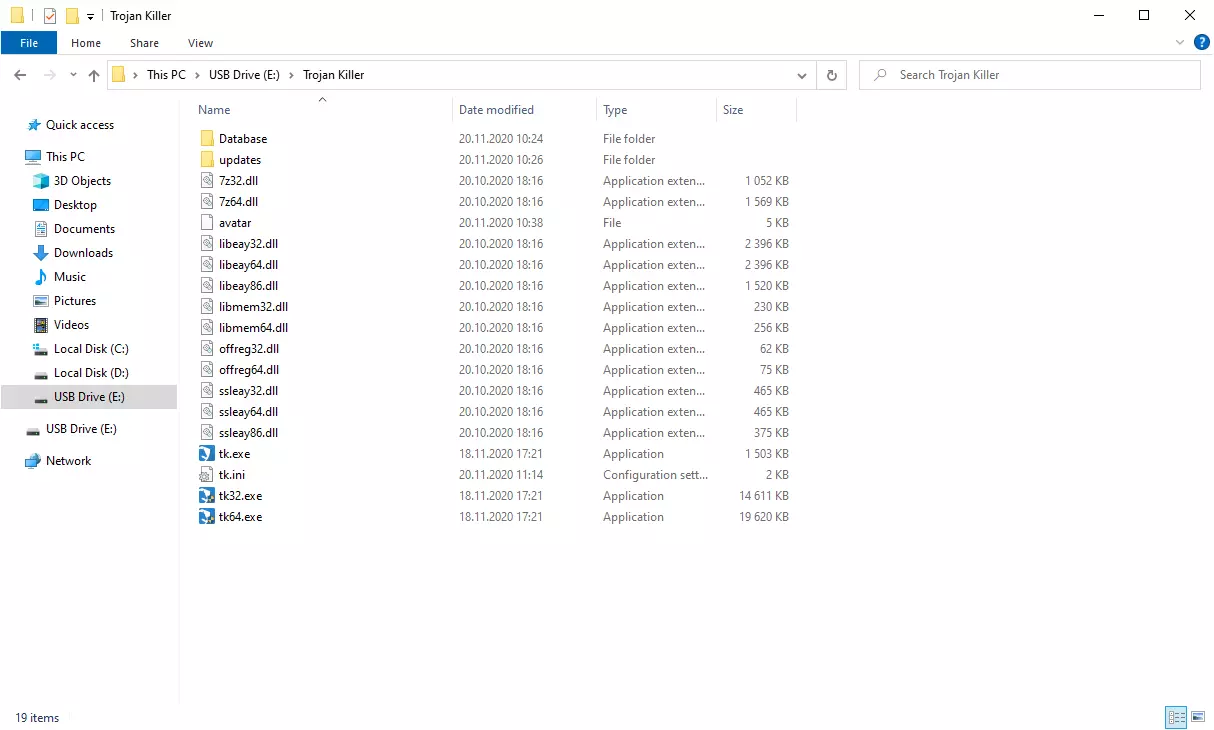
外觀與接口
Trojan Killer 不僅僅在功能上表現出色; 其設計簡潔性是另一個亮點. 與一個 直觀的界面 讓所有年齡段的用戶都能輕鬆導航, 它揭開了網絡安全的神秘面紗. 令人困惑的技術術語和侵入性的彈出窗口已經消失, 替換為透明的, 直白的語言.
主屏幕立即呈現所有重要功能, 無需費力瀏覽層層菜單. 無論您進行標準掃描還是全面掃描, 檢查可移動驅動器, 或自定義掃描, 一切從一開始就可以訪問. 即使更新 Trojan Killer 也輕而易舉 - 只需快速點擊窗口頂部的刷新圖標即可.
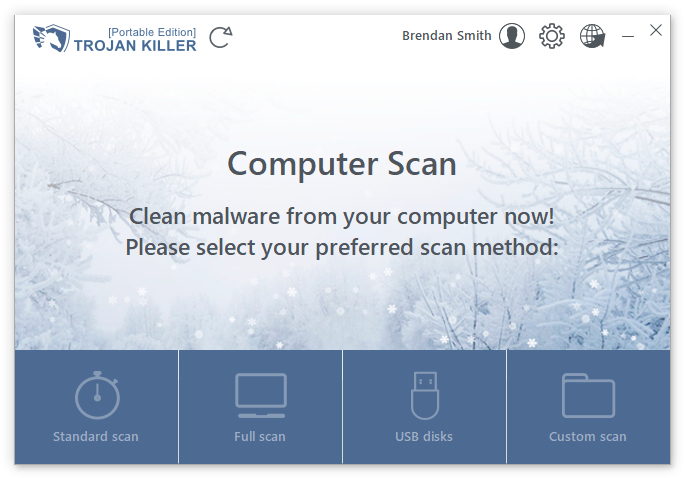
瀏覽器重置工具同樣用戶友好, 支持所有流行瀏覽器——Chrome, 歌劇, 火狐瀏覽器, 邊緣, 和 Internet Explorer. 調整要重置的瀏覽器非常簡單, 只需點擊一下即可打開或關閉 (灰色表示沒有復位). 以下, 您會發現一個完整的設置列表,可以輕鬆恢復到默認狀態, 確保您的瀏覽體驗盡可能流暢和安全.
木馬殺手的驚人效率
驗證特洛伊木馬殺手對抗數字威脅的能力, 我開始了嚴格的測試——與裝滿文件夾的攤牌 1392 惡意軟件樣本. 這個數字潘多拉魔盒包含了所有可以想像的威脅類型: 廣告軟件, 瀏覽器劫持者, 偷竊者, 後門, 勒索軟件——凡是你能想到的. 我的惡意軟件庫中的這種多樣性確保了徹底、客觀的評估.
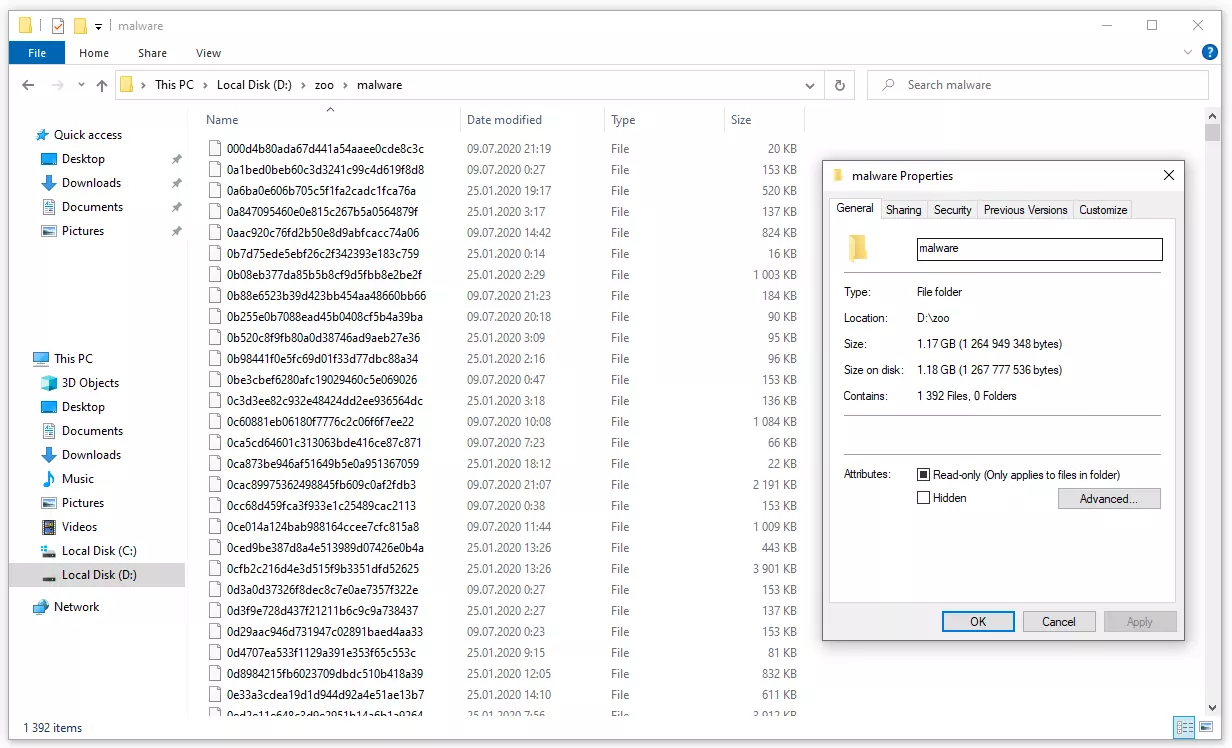
通過自定義掃描開始戰鬥, 我把特洛伊殺手引向風暴的中心並襲擊了 “立即掃描。”
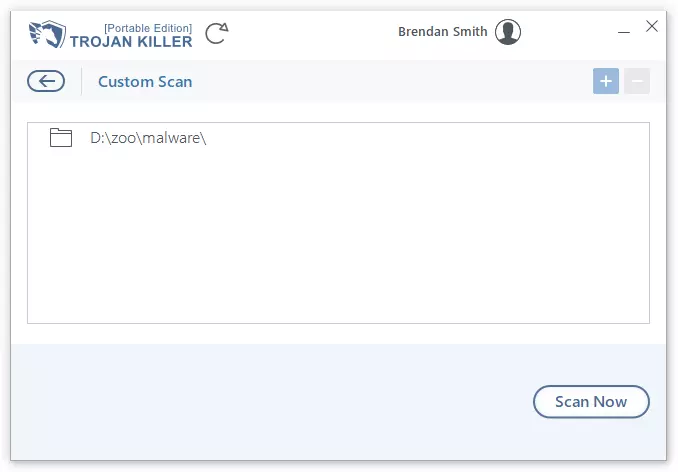
這場小衝突很短暫——僅僅持續了 15 秒, 展示特洛伊木馬殺手在集中條件下的運行速度. 自然, 跨越整個磁盤的更廣泛的探險需要更長的時間, 但最初的閃電戰令人印象深刻.
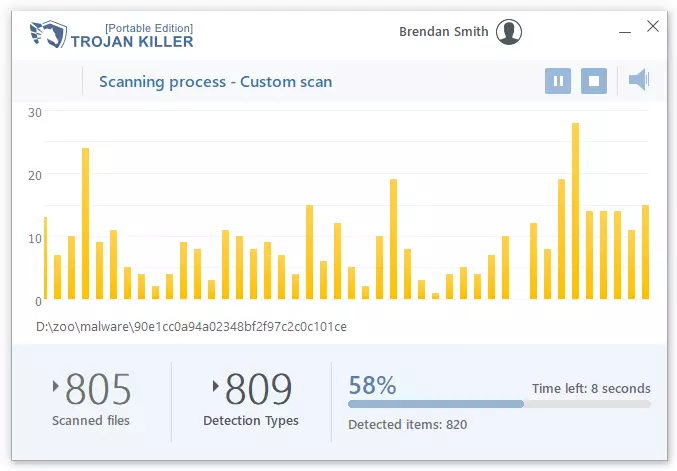
在最後, 勝利已經完成: 全部 1392 數字入侵者被揭露, 準備好用簡單的“立即清潔”進行清除!“ 命令.
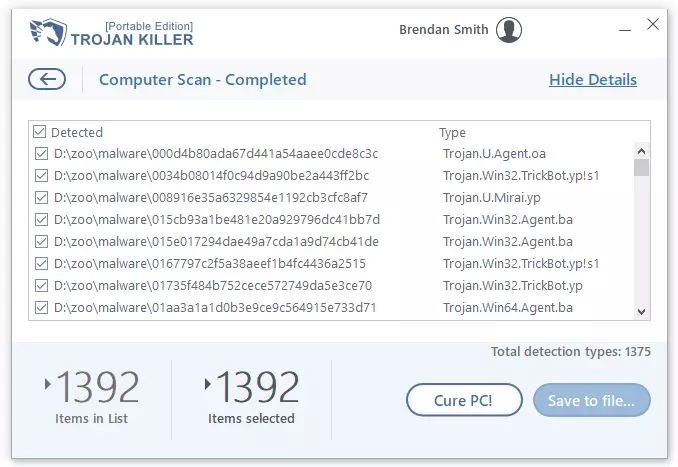
這一實力壯舉不僅證明了 Trojan Killer 的功效,還強調了其尚未開發的潛力, 具有掃描檔案等功能,無需提取.
您無法忽視的優惠: 木馬殺手的定價
回想一下通常與高級反惡意軟件解決方案相關的財務負擔? 木馬殺手挑戰了這一規範. 領先的解決方案徘徊在 80$ 年度許可證標記, 木馬殺手介紹 令人耳目一新的價格點 36$ 一年的強大保護. 細分如下:
- 個人的 – 僅僅一個 24$ 六個月, 36$ 一年, 或者 48$ 兩年了, 覆蓋單個設備.
- 公司的 – 在 72$ 每年, 為無限設備提供年度保護.
- 商業的 – 專為商業用途而設計 70$ 每月, 設備數量沒有上限.
但這不僅僅是數字的問題. 每個計劃適合不同的需求, 從個人防護到企業級防護, 包括 為企業提供專業支持 用戶和一個選項 嵌入您公司的徽標 商業訂閱者的特洛伊木馬殺手.
發表評論